committed by
 GitHub
GitHub
No known key found for this signature in database
GPG Key ID: 4AEE18F83AFDEB23
52 changed files with 9105 additions and 0 deletions
Split View
Diff Options
-
+3 -0t430/.gitignore
-
+674 -0t430/LICENSE
-
+0 -0t430/NEWS
-
+268 -0t430/README.md
-
BINt430/bootsplash.jpg
-
BINt430/bootsplash.xcf
-
+81 -0t430/build.sh
-
BINt430/ch341a.jpg
-
+46 -0t430/compile.sh
-
+257 -0t430/external_install_bottom.sh
-
+218 -0t430/external_install_top.sh
-
+11 -0t430/free-defconfig-555419f356
-
BINt430/front.jpg
-
+19 -0t430/nonfree-defconfig-555419f356
-
BINt430/pci8086,0166.rom
-
+149 -0t430/release.sh
-
BINt430/rpi_clip.jpg
-
+133 -0t430/t430_heads.sh
-
+221 -0t430/t430_skulls.sh
-
+339 -0t430/util/COPYING
-
+88 -0t430/util/commonlib/include/commonlib/cbfs.h
-
+241 -0t430/util/commonlib/include/commonlib/cbfs_serialized.h
-
+135 -0t430/util/commonlib/include/commonlib/cbmem_id.h
-
+34 -0t430/util/commonlib/include/commonlib/compression.h
-
+470 -0t430/util/commonlib/include/commonlib/coreboot_tables.h
-
+263 -0t430/util/commonlib/include/commonlib/endian.h
-
+74 -0t430/util/commonlib/include/commonlib/fmap_serialized.h
-
+32 -0t430/util/commonlib/include/commonlib/fsp.h
-
+99 -0t430/util/commonlib/include/commonlib/helpers.h
-
+162 -0t430/util/commonlib/include/commonlib/iobuf.h
-
+174 -0t430/util/commonlib/include/commonlib/loglevel.h
-
+69 -0t430/util/commonlib/include/commonlib/mem_pool.h
-
+274 -0t430/util/commonlib/include/commonlib/region.h
-
+60 -0t430/util/commonlib/include/commonlib/rmodule-defs.h
-
+228 -0t430/util/commonlib/include/commonlib/sd_mmc_ctrlr.h
-
+76 -0t430/util/commonlib/include/commonlib/sdhci.h
-
+74 -0t430/util/commonlib/include/commonlib/stdlib.h
-
+151 -0t430/util/commonlib/include/commonlib/storage.h
-
+263 -0t430/util/commonlib/include/commonlib/timestamp_serialized.h
-
+50 -0t430/util/functions.sh
-
+1 -0t430/util/ifdtool/.dependencies
-
+45 -0t430/util/ifdtool/Makefile
-
BINt430/util/ifdtool/ifdtool
-
+1491 -0t430/util/ifdtool/ifdtool.c
-
+127 -0t430/util/ifdtool/ifdtool.h
-
BINt430/util/ifdtool/ifdtool.o
-
+674 -0t430/util/me_cleaner/COPYING
-
+86 -0t430/util/me_cleaner/README.md
-
+159 -0t430/util/me_cleaner/man/me_cleaner.1
-
+166 -0t430/util/me_cleaner/man/me_cleaner.md
-
+897 -0t430/util/me_cleaner/me_cleaner.py
-
+23 -0t430/util/me_cleaner/setup.py
+ 3
- 0
t430/.gitignore
View File
| @ -0,0 +1,3 @@ | |||
| /output | |||
| t430_coreboot_seabios_*rom* | |||
| /build | |||
+ 674
- 0
t430/LICENSE
View File
| @ -0,0 +1,674 @@ | |||
| GNU GENERAL PUBLIC LICENSE | |||
| Version 3, 29 June 2007 | |||
| Copyright (C) 2007 Free Software Foundation, Inc. <http://fsf.org/> | |||
| Everyone is permitted to copy and distribute verbatim copies | |||
| of this license document, but changing it is not allowed. | |||
| Preamble | |||
| The GNU General Public License is a free, copyleft license for | |||
| software and other kinds of works. | |||
| The licenses for most software and other practical works are designed | |||
| to take away your freedom to share and change the works. By contrast, | |||
| the GNU General Public License is intended to guarantee your freedom to | |||
| share and change all versions of a program--to make sure it remains free | |||
| software for all its users. We, the Free Software Foundation, use the | |||
| GNU General Public License for most of our software; it applies also to | |||
| any other work released this way by its authors. You can apply it to | |||
| your programs, too. | |||
| When we speak of free software, we are referring to freedom, not | |||
| price. Our General Public Licenses are designed to make sure that you | |||
| have the freedom to distribute copies of free software (and charge for | |||
| them if you wish), that you receive source code or can get it if you | |||
| want it, that you can change the software or use pieces of it in new | |||
| free programs, and that you know you can do these things. | |||
| To protect your rights, we need to prevent others from denying you | |||
| these rights or asking you to surrender the rights. Therefore, you have | |||
| certain responsibilities if you distribute copies of the software, or if | |||
| you modify it: responsibilities to respect the freedom of others. | |||
| For example, if you distribute copies of such a program, whether | |||
| gratis or for a fee, you must pass on to the recipients the same | |||
| freedoms that you received. You must make sure that they, too, receive | |||
| or can get the source code. And you must show them these terms so they | |||
| know their rights. | |||
| Developers that use the GNU GPL protect your rights with two steps: | |||
| (1) assert copyright on the software, and (2) offer you this License | |||
| giving you legal permission to copy, distribute and/or modify it. | |||
| For the developers' and authors' protection, the GPL clearly explains | |||
| that there is no warranty for this free software. For both users' and | |||
| authors' sake, the GPL requires that modified versions be marked as | |||
| changed, so that their problems will not be attributed erroneously to | |||
| authors of previous versions. | |||
| Some devices are designed to deny users access to install or run | |||
| modified versions of the software inside them, although the manufacturer | |||
| can do so. This is fundamentally incompatible with the aim of | |||
| protecting users' freedom to change the software. The systematic | |||
| pattern of such abuse occurs in the area of products for individuals to | |||
| use, which is precisely where it is most unacceptable. Therefore, we | |||
| have designed this version of the GPL to prohibit the practice for those | |||
| products. If such problems arise substantially in other domains, we | |||
| stand ready to extend this provision to those domains in future versions | |||
| of the GPL, as needed to protect the freedom of users. | |||
| Finally, every program is threatened constantly by software patents. | |||
| States should not allow patents to restrict development and use of | |||
| software on general-purpose computers, but in those that do, we wish to | |||
| avoid the special danger that patents applied to a free program could | |||
| make it effectively proprietary. To prevent this, the GPL assures that | |||
| patents cannot be used to render the program non-free. | |||
| The precise terms and conditions for copying, distribution and | |||
| modification follow. | |||
| TERMS AND CONDITIONS | |||
| 0. Definitions. | |||
| "This License" refers to version 3 of the GNU General Public License. | |||
| "Copyright" also means copyright-like laws that apply to other kinds of | |||
| works, such as semiconductor masks. | |||
| "The Program" refers to any copyrightable work licensed under this | |||
| License. Each licensee is addressed as "you". "Licensees" and | |||
| "recipients" may be individuals or organizations. | |||
| To "modify" a work means to copy from or adapt all or part of the work | |||
| in a fashion requiring copyright permission, other than the making of an | |||
| exact copy. The resulting work is called a "modified version" of the | |||
| earlier work or a work "based on" the earlier work. | |||
| A "covered work" means either the unmodified Program or a work based | |||
| on the Program. | |||
| To "propagate" a work means to do anything with it that, without | |||
| permission, would make you directly or secondarily liable for | |||
| infringement under applicable copyright law, except executing it on a | |||
| computer or modifying a private copy. Propagation includes copying, | |||
| distribution (with or without modification), making available to the | |||
| public, and in some countries other activities as well. | |||
| To "convey" a work means any kind of propagation that enables other | |||
| parties to make or receive copies. Mere interaction with a user through | |||
| a computer network, with no transfer of a copy, is not conveying. | |||
| An interactive user interface displays "Appropriate Legal Notices" | |||
| to the extent that it includes a convenient and prominently visible | |||
| feature that (1) displays an appropriate copyright notice, and (2) | |||
| tells the user that there is no warranty for the work (except to the | |||
| extent that warranties are provided), that licensees may convey the | |||
| work under this License, and how to view a copy of this License. If | |||
| the interface presents a list of user commands or options, such as a | |||
| menu, a prominent item in the list meets this criterion. | |||
| 1. Source Code. | |||
| The "source code" for a work means the preferred form of the work | |||
| for making modifications to it. "Object code" means any non-source | |||
| form of a work. | |||
| A "Standard Interface" means an interface that either is an official | |||
| standard defined by a recognized standards body, or, in the case of | |||
| interfaces specified for a particular programming language, one that | |||
| is widely used among developers working in that language. | |||
| The "System Libraries" of an executable work include anything, other | |||
| than the work as a whole, that (a) is included in the normal form of | |||
| packaging a Major Component, but which is not part of that Major | |||
| Component, and (b) serves only to enable use of the work with that | |||
| Major Component, or to implement a Standard Interface for which an | |||
| implementation is available to the public in source code form. A | |||
| "Major Component", in this context, means a major essential component | |||
| (kernel, window system, and so on) of the specific operating system | |||
| (if any) on which the executable work runs, or a compiler used to | |||
| produce the work, or an object code interpreter used to run it. | |||
| The "Corresponding Source" for a work in object code form means all | |||
| the source code needed to generate, install, and (for an executable | |||
| work) run the object code and to modify the work, including scripts to | |||
| control those activities. However, it does not include the work's | |||
| System Libraries, or general-purpose tools or generally available free | |||
| programs which are used unmodified in performing those activities but | |||
| which are not part of the work. For example, Corresponding Source | |||
| includes interface definition files associated with source files for | |||
| the work, and the source code for shared libraries and dynamically | |||
| linked subprograms that the work is specifically designed to require, | |||
| such as by intimate data communication or control flow between those | |||
| subprograms and other parts of the work. | |||
| The Corresponding Source need not include anything that users | |||
| can regenerate automatically from other parts of the Corresponding | |||
| Source. | |||
| The Corresponding Source for a work in source code form is that | |||
| same work. | |||
| 2. Basic Permissions. | |||
| All rights granted under this License are granted for the term of | |||
| copyright on the Program, and are irrevocable provided the stated | |||
| conditions are met. This License explicitly affirms your unlimited | |||
| permission to run the unmodified Program. The output from running a | |||
| covered work is covered by this License only if the output, given its | |||
| content, constitutes a covered work. This License acknowledges your | |||
| rights of fair use or other equivalent, as provided by copyright law. | |||
| You may make, run and propagate covered works that you do not | |||
| convey, without conditions so long as your license otherwise remains | |||
| in force. You may convey covered works to others for the sole purpose | |||
| of having them make modifications exclusively for you, or provide you | |||
| with facilities for running those works, provided that you comply with | |||
| the terms of this License in conveying all material for which you do | |||
| not control copyright. Those thus making or running the covered works | |||
| for you must do so exclusively on your behalf, under your direction | |||
| and control, on terms that prohibit them from making any copies of | |||
| your copyrighted material outside their relationship with you. | |||
| Conveying under any other circumstances is permitted solely under | |||
| the conditions stated below. Sublicensing is not allowed; section 10 | |||
| makes it unnecessary. | |||
| 3. Protecting Users' Legal Rights From Anti-Circumvention Law. | |||
| No covered work shall be deemed part of an effective technological | |||
| measure under any applicable law fulfilling obligations under article | |||
| 11 of the WIPO copyright treaty adopted on 20 December 1996, or | |||
| similar laws prohibiting or restricting circumvention of such | |||
| measures. | |||
| When you convey a covered work, you waive any legal power to forbid | |||
| circumvention of technological measures to the extent such circumvention | |||
| is effected by exercising rights under this License with respect to | |||
| the covered work, and you disclaim any intention to limit operation or | |||
| modification of the work as a means of enforcing, against the work's | |||
| users, your or third parties' legal rights to forbid circumvention of | |||
| technological measures. | |||
| 4. Conveying Verbatim Copies. | |||
| You may convey verbatim copies of the Program's source code as you | |||
| receive it, in any medium, provided that you conspicuously and | |||
| appropriately publish on each copy an appropriate copyright notice; | |||
| keep intact all notices stating that this License and any | |||
| non-permissive terms added in accord with section 7 apply to the code; | |||
| keep intact all notices of the absence of any warranty; and give all | |||
| recipients a copy of this License along with the Program. | |||
| You may charge any price or no price for each copy that you convey, | |||
| and you may offer support or warranty protection for a fee. | |||
| 5. Conveying Modified Source Versions. | |||
| You may convey a work based on the Program, or the modifications to | |||
| produce it from the Program, in the form of source code under the | |||
| terms of section 4, provided that you also meet all of these conditions: | |||
| a) The work must carry prominent notices stating that you modified | |||
| it, and giving a relevant date. | |||
| b) The work must carry prominent notices stating that it is | |||
| released under this License and any conditions added under section | |||
| 7. This requirement modifies the requirement in section 4 to | |||
| "keep intact all notices". | |||
| c) You must license the entire work, as a whole, under this | |||
| License to anyone who comes into possession of a copy. This | |||
| License will therefore apply, along with any applicable section 7 | |||
| additional terms, to the whole of the work, and all its parts, | |||
| regardless of how they are packaged. This License gives no | |||
| permission to license the work in any other way, but it does not | |||
| invalidate such permission if you have separately received it. | |||
| d) If the work has interactive user interfaces, each must display | |||
| Appropriate Legal Notices; however, if the Program has interactive | |||
| interfaces that do not display Appropriate Legal Notices, your | |||
| work need not make them do so. | |||
| A compilation of a covered work with other separate and independent | |||
| works, which are not by their nature extensions of the covered work, | |||
| and which are not combined with it such as to form a larger program, | |||
| in or on a volume of a storage or distribution medium, is called an | |||
| "aggregate" if the compilation and its resulting copyright are not | |||
| used to limit the access or legal rights of the compilation's users | |||
| beyond what the individual works permit. Inclusion of a covered work | |||
| in an aggregate does not cause this License to apply to the other | |||
| parts of the aggregate. | |||
| 6. Conveying Non-Source Forms. | |||
| You may convey a covered work in object code form under the terms | |||
| of sections 4 and 5, provided that you also convey the | |||
| machine-readable Corresponding Source under the terms of this License, | |||
| in one of these ways: | |||
| a) Convey the object code in, or embodied in, a physical product | |||
| (including a physical distribution medium), accompanied by the | |||
| Corresponding Source fixed on a durable physical medium | |||
| customarily used for software interchange. | |||
| b) Convey the object code in, or embodied in, a physical product | |||
| (including a physical distribution medium), accompanied by a | |||
| written offer, valid for at least three years and valid for as | |||
| long as you offer spare parts or customer support for that product | |||
| model, to give anyone who possesses the object code either (1) a | |||
| copy of the Corresponding Source for all the software in the | |||
| product that is covered by this License, on a durable physical | |||
| medium customarily used for software interchange, for a price no | |||
| more than your reasonable cost of physically performing this | |||
| conveying of source, or (2) access to copy the | |||
| Corresponding Source from a network server at no charge. | |||
| c) Convey individual copies of the object code with a copy of the | |||
| written offer to provide the Corresponding Source. This | |||
| alternative is allowed only occasionally and noncommercially, and | |||
| only if you received the object code with such an offer, in accord | |||
| with subsection 6b. | |||
| d) Convey the object code by offering access from a designated | |||
| place (gratis or for a charge), and offer equivalent access to the | |||
| Corresponding Source in the same way through the same place at no | |||
| further charge. You need not require recipients to copy the | |||
| Corresponding Source along with the object code. If the place to | |||
| copy the object code is a network server, the Corresponding Source | |||
| may be on a different server (operated by you or a third party) | |||
| that supports equivalent copying facilities, provided you maintain | |||
| clear directions next to the object code saying where to find the | |||
| Corresponding Source. Regardless of what server hosts the | |||
| Corresponding Source, you remain obligated to ensure that it is | |||
| available for as long as needed to satisfy these requirements. | |||
| e) Convey the object code using peer-to-peer transmission, provided | |||
| you inform other peers where the object code and Corresponding | |||
| Source of the work are being offered to the general public at no | |||
| charge under subsection 6d. | |||
| A separable portion of the object code, whose source code is excluded | |||
| from the Corresponding Source as a System Library, need not be | |||
| included in conveying the object code work. | |||
| A "User Product" is either (1) a "consumer product", which means any | |||
| tangible personal property which is normally used for personal, family, | |||
| or household purposes, or (2) anything designed or sold for incorporation | |||
| into a dwelling. In determining whether a product is a consumer product, | |||
| doubtful cases shall be resolved in favor of coverage. For a particular | |||
| product received by a particular user, "normally used" refers to a | |||
| typical or common use of that class of product, regardless of the status | |||
| of the particular user or of the way in which the particular user | |||
| actually uses, or expects or is expected to use, the product. A product | |||
| is a consumer product regardless of whether the product has substantial | |||
| commercial, industrial or non-consumer uses, unless such uses represent | |||
| the only significant mode of use of the product. | |||
| "Installation Information" for a User Product means any methods, | |||
| procedures, authorization keys, or other information required to install | |||
| and execute modified versions of a covered work in that User Product from | |||
| a modified version of its Corresponding Source. The information must | |||
| suffice to ensure that the continued functioning of the modified object | |||
| code is in no case prevented or interfered with solely because | |||
| modification has been made. | |||
| If you convey an object code work under this section in, or with, or | |||
| specifically for use in, a User Product, and the conveying occurs as | |||
| part of a transaction in which the right of possession and use of the | |||
| User Product is transferred to the recipient in perpetuity or for a | |||
| fixed term (regardless of how the transaction is characterized), the | |||
| Corresponding Source conveyed under this section must be accompanied | |||
| by the Installation Information. But this requirement does not apply | |||
| if neither you nor any third party retains the ability to install | |||
| modified object code on the User Product (for example, the work has | |||
| been installed in ROM). | |||
| The requirement to provide Installation Information does not include a | |||
| requirement to continue to provide support service, warranty, or updates | |||
| for a work that has been modified or installed by the recipient, or for | |||
| the User Product in which it has been modified or installed. Access to a | |||
| network may be denied when the modification itself materially and | |||
| adversely affects the operation of the network or violates the rules and | |||
| protocols for communication across the network. | |||
| Corresponding Source conveyed, and Installation Information provided, | |||
| in accord with this section must be in a format that is publicly | |||
| documented (and with an implementation available to the public in | |||
| source code form), and must require no special password or key for | |||
| unpacking, reading or copying. | |||
| 7. Additional Terms. | |||
| "Additional permissions" are terms that supplement the terms of this | |||
| License by making exceptions from one or more of its conditions. | |||
| Additional permissions that are applicable to the entire Program shall | |||
| be treated as though they were included in this License, to the extent | |||
| that they are valid under applicable law. If additional permissions | |||
| apply only to part of the Program, that part may be used separately | |||
| under those permissions, but the entire Program remains governed by | |||
| this License without regard to the additional permissions. | |||
| When you convey a copy of a covered work, you may at your option | |||
| remove any additional permissions from that copy, or from any part of | |||
| it. (Additional permissions may be written to require their own | |||
| removal in certain cases when you modify the work.) You may place | |||
| additional permissions on material, added by you to a covered work, | |||
| for which you have or can give appropriate copyright permission. | |||
| Notwithstanding any other provision of this License, for material you | |||
| add to a covered work, you may (if authorized by the copyright holders of | |||
| that material) supplement the terms of this License with terms: | |||
| a) Disclaiming warranty or limiting liability differently from the | |||
| terms of sections 15 and 16 of this License; or | |||
| b) Requiring preservation of specified reasonable legal notices or | |||
| author attributions in that material or in the Appropriate Legal | |||
| Notices displayed by works containing it; or | |||
| c) Prohibiting misrepresentation of the origin of that material, or | |||
| requiring that modified versions of such material be marked in | |||
| reasonable ways as different from the original version; or | |||
| d) Limiting the use for publicity purposes of names of licensors or | |||
| authors of the material; or | |||
| e) Declining to grant rights under trademark law for use of some | |||
| trade names, trademarks, or service marks; or | |||
| f) Requiring indemnification of licensors and authors of that | |||
| material by anyone who conveys the material (or modified versions of | |||
| it) with contractual assumptions of liability to the recipient, for | |||
| any liability that these contractual assumptions directly impose on | |||
| those licensors and authors. | |||
| All other non-permissive additional terms are considered "further | |||
| restrictions" within the meaning of section 10. If the Program as you | |||
| received it, or any part of it, contains a notice stating that it is | |||
| governed by this License along with a term that is a further | |||
| restriction, you may remove that term. If a license document contains | |||
| a further restriction but permits relicensing or conveying under this | |||
| License, you may add to a covered work material governed by the terms | |||
| of that license document, provided that the further restriction does | |||
| not survive such relicensing or conveying. | |||
| If you add terms to a covered work in accord with this section, you | |||
| must place, in the relevant source files, a statement of the | |||
| additional terms that apply to those files, or a notice indicating | |||
| where to find the applicable terms. | |||
| Additional terms, permissive or non-permissive, may be stated in the | |||
| form of a separately written license, or stated as exceptions; | |||
| the above requirements apply either way. | |||
| 8. Termination. | |||
| You may not propagate or modify a covered work except as expressly | |||
| provided under this License. Any attempt otherwise to propagate or | |||
| modify it is void, and will automatically terminate your rights under | |||
| this License (including any patent licenses granted under the third | |||
| paragraph of section 11). | |||
| However, if you cease all violation of this License, then your | |||
| license from a particular copyright holder is reinstated (a) | |||
| provisionally, unless and until the copyright holder explicitly and | |||
| finally terminates your license, and (b) permanently, if the copyright | |||
| holder fails to notify you of the violation by some reasonable means | |||
| prior to 60 days after the cessation. | |||
| Moreover, your license from a particular copyright holder is | |||
| reinstated permanently if the copyright holder notifies you of the | |||
| violation by some reasonable means, this is the first time you have | |||
| received notice of violation of this License (for any work) from that | |||
| copyright holder, and you cure the violation prior to 30 days after | |||
| your receipt of the notice. | |||
| Termination of your rights under this section does not terminate the | |||
| licenses of parties who have received copies or rights from you under | |||
| this License. If your rights have been terminated and not permanently | |||
| reinstated, you do not qualify to receive new licenses for the same | |||
| material under section 10. | |||
| 9. Acceptance Not Required for Having Copies. | |||
| You are not required to accept this License in order to receive or | |||
| run a copy of the Program. Ancillary propagation of a covered work | |||
| occurring solely as a consequence of using peer-to-peer transmission | |||
| to receive a copy likewise does not require acceptance. However, | |||
| nothing other than this License grants you permission to propagate or | |||
| modify any covered work. These actions infringe copyright if you do | |||
| not accept this License. Therefore, by modifying or propagating a | |||
| covered work, you indicate your acceptance of this License to do so. | |||
| 10. Automatic Licensing of Downstream Recipients. | |||
| Each time you convey a covered work, the recipient automatically | |||
| receives a license from the original licensors, to run, modify and | |||
| propagate that work, subject to this License. You are not responsible | |||
| for enforcing compliance by third parties with this License. | |||
| An "entity transaction" is a transaction transferring control of an | |||
| organization, or substantially all assets of one, or subdividing an | |||
| organization, or merging organizations. If propagation of a covered | |||
| work results from an entity transaction, each party to that | |||
| transaction who receives a copy of the work also receives whatever | |||
| licenses to the work the party's predecessor in interest had or could | |||
| give under the previous paragraph, plus a right to possession of the | |||
| Corresponding Source of the work from the predecessor in interest, if | |||
| the predecessor has it or can get it with reasonable efforts. | |||
| You may not impose any further restrictions on the exercise of the | |||
| rights granted or affirmed under this License. For example, you may | |||
| not impose a license fee, royalty, or other charge for exercise of | |||
| rights granted under this License, and you may not initiate litigation | |||
| (including a cross-claim or counterclaim in a lawsuit) alleging that | |||
| any patent claim is infringed by making, using, selling, offering for | |||
| sale, or importing the Program or any portion of it. | |||
| 11. Patents. | |||
| A "contributor" is a copyright holder who authorizes use under this | |||
| License of the Program or a work on which the Program is based. The | |||
| work thus licensed is called the contributor's "contributor version". | |||
| A contributor's "essential patent claims" are all patent claims | |||
| owned or controlled by the contributor, whether already acquired or | |||
| hereafter acquired, that would be infringed by some manner, permitted | |||
| by this License, of making, using, or selling its contributor version, | |||
| but do not include claims that would be infringed only as a | |||
| consequence of further modification of the contributor version. For | |||
| purposes of this definition, "control" includes the right to grant | |||
| patent sublicenses in a manner consistent with the requirements of | |||
| this License. | |||
| Each contributor grants you a non-exclusive, worldwide, royalty-free | |||
| patent license under the contributor's essential patent claims, to | |||
| make, use, sell, offer for sale, import and otherwise run, modify and | |||
| propagate the contents of its contributor version. | |||
| In the following three paragraphs, a "patent license" is any express | |||
| agreement or commitment, however denominated, not to enforce a patent | |||
| (such as an express permission to practice a patent or covenant not to | |||
| sue for patent infringement). To "grant" such a patent license to a | |||
| party means to make such an agreement or commitment not to enforce a | |||
| patent against the party. | |||
| If you convey a covered work, knowingly relying on a patent license, | |||
| and the Corresponding Source of the work is not available for anyone | |||
| to copy, free of charge and under the terms of this License, through a | |||
| publicly available network server or other readily accessible means, | |||
| then you must either (1) cause the Corresponding Source to be so | |||
| available, or (2) arrange to deprive yourself of the benefit of the | |||
| patent license for this particular work, or (3) arrange, in a manner | |||
| consistent with the requirements of this License, to extend the patent | |||
| license to downstream recipients. "Knowingly relying" means you have | |||
| actual knowledge that, but for the patent license, your conveying the | |||
| covered work in a country, or your recipient's use of the covered work | |||
| in a country, would infringe one or more identifiable patents in that | |||
| country that you have reason to believe are valid. | |||
| If, pursuant to or in connection with a single transaction or | |||
| arrangement, you convey, or propagate by procuring conveyance of, a | |||
| covered work, and grant a patent license to some of the parties | |||
| receiving the covered work authorizing them to use, propagate, modify | |||
| or convey a specific copy of the covered work, then the patent license | |||
| you grant is automatically extended to all recipients of the covered | |||
| work and works based on it. | |||
| A patent license is "discriminatory" if it does not include within | |||
| the scope of its coverage, prohibits the exercise of, or is | |||
| conditioned on the non-exercise of one or more of the rights that are | |||
| specifically granted under this License. You may not convey a covered | |||
| work if you are a party to an arrangement with a third party that is | |||
| in the business of distributing software, under which you make payment | |||
| to the third party based on the extent of your activity of conveying | |||
| the work, and under which the third party grants, to any of the | |||
| parties who would receive the covered work from you, a discriminatory | |||
| patent license (a) in connection with copies of the covered work | |||
| conveyed by you (or copies made from those copies), or (b) primarily | |||
| for and in connection with specific products or compilations that | |||
| contain the covered work, unless you entered into that arrangement, | |||
| or that patent license was granted, prior to 28 March 2007. | |||
| Nothing in this License shall be construed as excluding or limiting | |||
| any implied license or other defenses to infringement that may | |||
| otherwise be available to you under applicable patent law. | |||
| 12. No Surrender of Others' Freedom. | |||
| If conditions are imposed on you (whether by court order, agreement or | |||
| otherwise) that contradict the conditions of this License, they do not | |||
| excuse you from the conditions of this License. If you cannot convey a | |||
| covered work so as to satisfy simultaneously your obligations under this | |||
| License and any other pertinent obligations, then as a consequence you may | |||
| not convey it at all. For example, if you agree to terms that obligate you | |||
| to collect a royalty for further conveying from those to whom you convey | |||
| the Program, the only way you could satisfy both those terms and this | |||
| License would be to refrain entirely from conveying the Program. | |||
| 13. Use with the GNU Affero General Public License. | |||
| Notwithstanding any other provision of this License, you have | |||
| permission to link or combine any covered work with a work licensed | |||
| under version 3 of the GNU Affero General Public License into a single | |||
| combined work, and to convey the resulting work. The terms of this | |||
| License will continue to apply to the part which is the covered work, | |||
| but the special requirements of the GNU Affero General Public License, | |||
| section 13, concerning interaction through a network will apply to the | |||
| combination as such. | |||
| 14. Revised Versions of this License. | |||
| The Free Software Foundation may publish revised and/or new versions of | |||
| the GNU General Public License from time to time. Such new versions will | |||
| be similar in spirit to the present version, but may differ in detail to | |||
| address new problems or concerns. | |||
| Each version is given a distinguishing version number. If the | |||
| Program specifies that a certain numbered version of the GNU General | |||
| Public License "or any later version" applies to it, you have the | |||
| option of following the terms and conditions either of that numbered | |||
| version or of any later version published by the Free Software | |||
| Foundation. If the Program does not specify a version number of the | |||
| GNU General Public License, you may choose any version ever published | |||
| by the Free Software Foundation. | |||
| If the Program specifies that a proxy can decide which future | |||
| versions of the GNU General Public License can be used, that proxy's | |||
| public statement of acceptance of a version permanently authorizes you | |||
| to choose that version for the Program. | |||
| Later license versions may give you additional or different | |||
| permissions. However, no additional obligations are imposed on any | |||
| author or copyright holder as a result of your choosing to follow a | |||
| later version. | |||
| 15. Disclaimer of Warranty. | |||
| THERE IS NO WARRANTY FOR THE PROGRAM, TO THE EXTENT PERMITTED BY | |||
| APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED IN WRITING THE COPYRIGHT | |||
| HOLDERS AND/OR OTHER PARTIES PROVIDE THE PROGRAM "AS IS" WITHOUT WARRANTY | |||
| OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, | |||
| THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR | |||
| PURPOSE. THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE PROGRAM | |||
| IS WITH YOU. SHOULD THE PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF | |||
| ALL NECESSARY SERVICING, REPAIR OR CORRECTION. | |||
| 16. Limitation of Liability. | |||
| IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING | |||
| WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MODIFIES AND/OR CONVEYS | |||
| THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY | |||
| GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE | |||
| USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED TO LOSS OF | |||
| DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD | |||
| PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER PROGRAMS), | |||
| EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF | |||
| SUCH DAMAGES. | |||
| 17. Interpretation of Sections 15 and 16. | |||
| If the disclaimer of warranty and limitation of liability provided | |||
| above cannot be given local legal effect according to their terms, | |||
| reviewing courts shall apply local law that most closely approximates | |||
| an absolute waiver of all civil liability in connection with the | |||
| Program, unless a warranty or assumption of liability accompanies a | |||
| copy of the Program in return for a fee. | |||
| END OF TERMS AND CONDITIONS | |||
| How to Apply These Terms to Your New Programs | |||
| If you develop a new program, and you want it to be of the greatest | |||
| possible use to the public, the best way to achieve this is to make it | |||
| free software which everyone can redistribute and change under these terms. | |||
| To do so, attach the following notices to the program. It is safest | |||
| to attach them to the start of each source file to most effectively | |||
| state the exclusion of warranty; and each file should have at least | |||
| the "copyright" line and a pointer to where the full notice is found. | |||
| <one line to give the program's name and a brief idea of what it does.> | |||
| Copyright (C) <year> <name of author> | |||
| This program is free software: you can redistribute it and/or modify | |||
| it under the terms of the GNU General Public License as published by | |||
| the Free Software Foundation, either version 3 of the License, or | |||
| (at your option) any later version. | |||
| This program is distributed in the hope that it will be useful, | |||
| but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| GNU General Public License for more details. | |||
| You should have received a copy of the GNU General Public License | |||
| along with this program. If not, see <http://www.gnu.org/licenses/>. | |||
| Also add information on how to contact you by electronic and paper mail. | |||
| If the program does terminal interaction, make it output a short | |||
| notice like this when it starts in an interactive mode: | |||
| <program> Copyright (C) <year> <name of author> | |||
| This program comes with ABSOLUTELY NO WARRANTY; for details type `show w'. | |||
| This is free software, and you are welcome to redistribute it | |||
| under certain conditions; type `show c' for details. | |||
| The hypothetical commands `show w' and `show c' should show the appropriate | |||
| parts of the General Public License. Of course, your program's commands | |||
| might be different; for a GUI interface, you would use an "about box". | |||
| You should also get your employer (if you work as a programmer) or school, | |||
| if any, to sign a "copyright disclaimer" for the program, if necessary. | |||
| For more information on this, and how to apply and follow the GNU GPL, see | |||
| <http://www.gnu.org/licenses/>. | |||
| The GNU General Public License does not permit incorporating your program | |||
| into proprietary programs. If your program is a subroutine library, you | |||
| may consider it more useful to permit linking proprietary applications with | |||
| the library. If this is what you want to do, use the GNU Lesser General | |||
| Public License instead of this License. But first, please read | |||
| <http://www.gnu.org/philosophy/why-not-lgpl.html>. | |||
+ 0
- 0
t430/NEWS
View File
+ 268
- 0
t430/README.md
View File
| @ -0,0 +1,268 @@ | |||
| # Skulls - [Thinkpad T430](https://pcsupport.lenovo.com/en/products/laptops-and-netbooks/thinkpad-t-series-laptops/thinkpad-t430) | |||
|  | |||
| ## Latest release | |||
| Get it from our [release page](https://github.com/merge/coreboot-t430/releases) | |||
| * __coreboot__: We take coreboot's master branch at the time we build a release image. | |||
| * __microcode update__: revision `0x21` from 2019-02-13 | |||
| * __SeaBIOS__: version [1.12.1](https://seabios.org/Releases) from 2019-02-04 | |||
| ### release images to choose from | |||
| We release multiple different, but _very similar_ images you can choose from. | |||
| They all should work on all versions of the T430/T430T. These are the | |||
| differences; (xxxxxxxxxx stands for random characters in the filename): | |||
| * `t430_coreboot_seabios_xxxxxxxxxx_top.rom` includes the _proprietary_ | |||
| [VGA BIOS](https://en.wikipedia.org/wiki/Video_BIOS) from [Intel](https://www.intel.com/content/www/us/en/intelligent-systems/intel-embedded-graphics-drivers/faq-bios-firmware.html) | |||
| which is non-free software. It is executed in "secure" mode. | |||
| * `t430_coreboot_seabios_free_xxxxxxxxxx_top.rom` includes the | |||
| [VGA BIOS](https://en.wikipedia.org/wiki/Video_BIOS) | |||
| [SeaVGABIOS](https://www.seabios.org/SeaVGABIOS) which is free software. | |||
| While technically more interesting, visually this is currently not as | |||
| beautiful: | |||
| * The [bootspash image is not shown](https://github.com/merge/skulls/issues/59). | |||
| * Early boot console messages (after your HDD's bootloader has started a kernel) might be [missing](https://github.com/merge/skulls/issues/46). | |||
| ## table of contents | |||
| * [TL;DR](#tldr) | |||
| * [First-time installation](#first-time-installation) | |||
| * [Updating](#updating) | |||
| * [Moving to Heads](#moving-to-heads) | |||
| * [Why does this work](#why-does-this-work) | |||
| * [How to rebuild](#how-to-reproduce-the-release-images) | |||
| ## TL;DR | |||
| 1. run `sudo ./t430_skulls.sh` on your current T430 Linux system | |||
| 2. Power down, remove the battery. Remove the keyboard and palmrest. Connect | |||
| a hardware flasher to an external PC (or a Raspberry Pi with a SPI 8-pin chip clip | |||
| can directly be used), and run | |||
| `sudo ./external_install_bottom.sh` on the lower chip | |||
| and `sudo ./external_install_top.sh` on the top chip of the two. | |||
| 3. For updating later, run `./t430_skulls.sh`. No need to disassemble. | |||
| And always use the latest [released](https://github.com/merge/coreboot-t430/releases) | |||
| package. This will be tested. The git master | |||
| branch is _not_ meant to be stable. Use it for testing only. | |||
| ## First-time installation | |||
| #### before you begin | |||
| Run Linux on your T430, install `dmidecode` and run | |||
| `sudo ./t430_skulls.sh`. It simply prints system information and | |||
| helps you to be up to date. | |||
| Make sure you have the latest skulls-t430 package release by running | |||
| `./t430_skulls.sh -U`. | |||
| #### original BIOS update / EC firmware (optional) | |||
| If the script, `sudo ./t430_skulls.sh` says "The installed original BIOS is very | |||
| old.", it means that you have a BIOS version that may include an EC version | |||
| older than 1.14. | |||
| If that's the case, consider doing one original Lenovo upgrade process. This is not | |||
| supported anymore, once you're running coreboot (You'd have to manually | |||
| flash back your backup images first, see later chapters). | |||
| This updates the BIOS _and_ Embedded Controller (EC) firmware. The EC | |||
| is not updated anymore, when running coreboot. The latest EC version is 1.14 | |||
| and that's unlikely to change. | |||
| You have 2 options: | |||
| * use [the latest original CD](https://pcsupport.lenovo.com/us/en/products/laptops-and-netbooks/thinkpad-x-series-laptops/thinkpad-t430/downloads/ds029187) and burn it, or | |||
| * use the same, only with a patched EC firmware that allows using any aftermarket-battery: | |||
| By default, only original Lenovo batteries are allowed. | |||
| Thanks to [this](http://zmatt.net/unlocking-my-lenovo-laptop-part-3/) | |||
| [project](https://github.com/eigenmatt/mec-tools) we can use Lenovo's bootable | |||
| upgrade image, change it and create a bootable _USB_ image (even with EC updates | |||
| that allows one to use 3rd party aftermarket batteries). For this, follow instructions | |||
| at [github.com/hamishcoleman/thinkpad-ec](https://github.com/hamishcoleman/thinkpad-ec). | |||
| #### preparation: required hardware | |||
| * An 8 Pin SOIC Clip, for example from | |||
| [Pomona electronics](https://www.pomonaelectronics.com/products/test-clips/soic-clip-8-pin) | |||
| (for availability, check | |||
| [aliexpress](https://de.aliexpress.com/item/POMONA-SOIC-CLIP-5250-8pin-eeprom-for-tacho-8pin-cable-for-pomana-soic-8pin/32814247676.html) or | |||
| [elsewhere](https://geizhals.eu/?fs=pomona+test+clip+5250)) | |||
| or alternatively hooks like | |||
| [E-Z-Hook](http://catalog.e-z-hook.com/viewitems/test-hooks/e-z-micro-hooks-single-hook-style) | |||
| * 6 [female](https://electronics.stackexchange.com/questions/37783/how-can-i-create-a-female-jumper-wire-connector) | |||
| [jumper wires](https://en.wikipedia.org/wiki/Jump_wire) like | |||
| [these](https://geizhals.eu/jumper-cable-female-female-20cm-a1471094.html) | |||
| to connect the clip to a hardware flasher (if not included with the clip) | |||
| * a hardware flasher | |||
| [supported by flashrom](https://www.flashrom.org/Flashrom/0.9.9/Supported_Hardware#USB_Devices), see below for the examples we support | |||
| #### open up the T430 | |||
| Remove the 7 screws of your T430 to remove the keyboard (by pushing it towards the | |||
| screen before lifting) and the palmrest. You'll find the chips using the photo | |||
| below. This is how the SPI connection looks like on both of the T430's chips: | |||
| Screen (furthest from you) | |||
| ______ | |||
| MOSI 5 --| |-- 4 GND | |||
| CLK 6 --| |-- 3 N/C | |||
| N/C 7 --| |-- 2 MISO | |||
| VCC 8 --|______|-- 1 CS | |||
| Edge (closest to you) | |||
| ... choose __one of the following__ supported flashing hardware examples: | |||
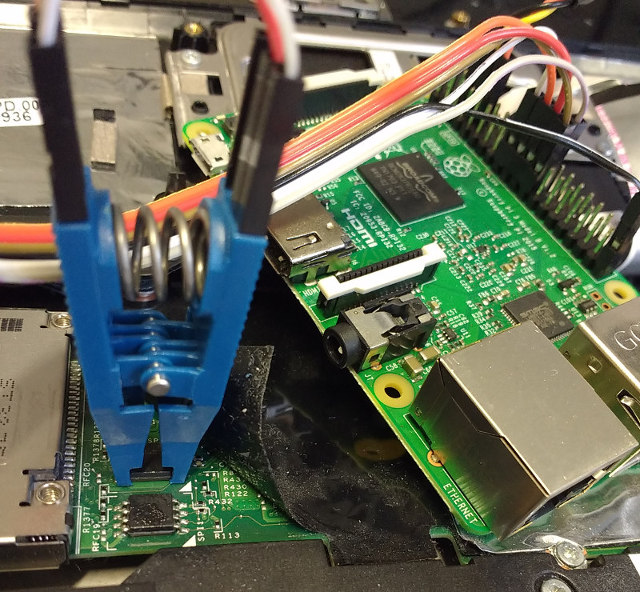
| #### Hardware Example: Raspberry Pi 3 | |||
| A Raspberry Pi can directly be a flasher through it's I/O pins, see below. | |||
| Use a test clip or hooks, see [required hardware](#preparation-required-hardware). | |||
| On the RPi we run [Raspbian](https://www.raspberrypi.org/downloads/raspbian/) | |||
| and have the following setup: | |||
| * Connect to the console: Either | |||
| * connect a screen and a keyboard, or | |||
| * Use the [Serial connection](https://elinux.org/RPi_Serial_Connection) using a | |||
| USB-to-serial cable (like [Adafruit 954](http://www.adafruit.com/products/954), | |||
| [FTDI TTL-232R-RPI](http://www.ftdichip.com/Products/Cables/RPi.htm) or | |||
| [others](https://geizhals.eu/usb-to-ttl-serial-adapter-cable-a1461312.html)) and | |||
| picocom (`picocom -b 115200 /dev/ttyUSB0`) or minicom | |||
| * in the SD Cards's `/boot/config.txt` file `enable_uart=1` and `dtparam=spi=on` | |||
| * [For flashrom](https://www.flashrom.org/RaspberryPi) we put `spi_bcm2835` | |||
| and `spidev` in /etc/modules | |||
| * [Connect to a wifi](https://www.raspberrypi.org/documentation/configuration/wireless/wireless-cli.md) | |||
| or ethernet to `sudo apt-get install flashrom` | |||
| * connect the Clip to the Raspberry Pi 3 (there are | |||
| [prettier images](https://github.com/splitbrain/rpibplusleaf) too): | |||
| Edge of pi (furthest from you) | |||
| (UART) | |||
| L GND TX RX CS | |||
| E | | | | | |||
| F +---------------------------------------------------------------------------------+ | |||
| T | x x x x x x x x x x x x x x x x x x x x | | |||
| | x x x x x x x x x x x x x x x x x x x x | | |||
| E +----------------------------------^---^---^---^-------------------------------^--+ | |||
| D | | | | | | |||
| G 3.3V MOSIMISO| GND | |||
| E (VCC) CLK | |||
| Body of Pi (closest to you) | |||
|  | |||
| Now copy the Skulls release tarball over to the Rasperry Pi and | |||
| [continue](#unpack-the-skulls-release-archive) on the Pi. | |||
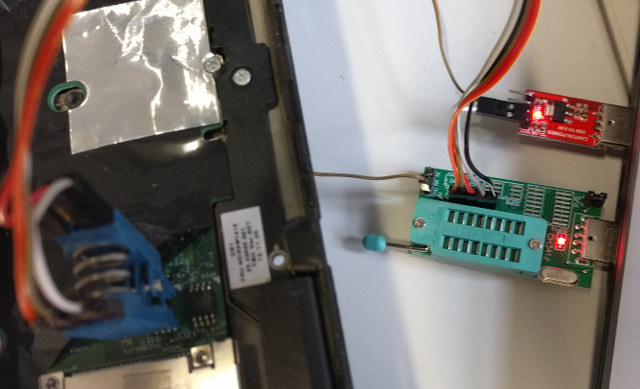
| #### Hardware Example: CH341A based | |||
| The CH341A from [Winchiphead](http://www.wch.cn/), a USB interface chip, | |||
| is used by some cheap memory programmers. | |||
| The one we describe can be bought at | |||
| [aliexpress](http://www.aliexpress.com/item/Free-Shipping-CH341A-24-25-Series-EEPROM-Flash-BIOS-DVD-USB-Programmer-DVD-programmer-router-Nine/32583059603.html), | |||
| but it's available [elsewhere](https://geizhals.eu/?fs=ch341a) too. | |||
| This means you need a different computer running a Linux based system here. | |||
| Also, we don't use the included 3,3V power output (provides too little power), | |||
| but a separate power supply. If you don't have any, consider getting a AMS1117 | |||
| based supply for a second USB port (like [this](https://de.aliexpress.com/item/1PCS-AMS1117-3-3V-Mini-USB-5V-3-3V-DC-Perfect-Power-Supply-Module/32785334595.html) or [this](https://www.ebay.com/sch/i.html?_nkw=ams1117+usb)). | |||
| * Leave the P/S Jumper connected (programmer mode, 1a86:5512 USB device) | |||
| * Connect 3,3V from your external supply to the Pomona clip's (or hook) VCC | |||
| * Connect GND from your external supply to GND on your CH341A programmer | |||
| * Connect your clip or hooks to the rest of the programmer's SPI pins | |||
| * Connect the programmer (and power supply, if USB) to your PC's USB port | |||
|  | |||
| #### unpack the Skulls release archive | |||
| tar -xf skulls-t430-<version>.tar.xz | |||
| cd skulls-t430-<version> | |||
| #### ifd unlock and me_cleaner: the 8MB chip | |||
| Flashing the bottom chip (closer to you) is optional. It has the same pinout | |||
| than the upper chip. This allows you to enable/disable in-system flashing | |||
| (without disassembling the Thinkpad) and/or to neuter the | |||
| [Intel Management Engine](https://en.wikipedia.org/wiki/Intel_Management_Engine) | |||
| for [security reasons](https://en.wikipedia.org/wiki/Intel_Management_Engine#Security_vulnerabilities). | |||
| sudo ./external_install_bottom.sh -m -k <backup-file-to-create> | |||
| That's it. Keep the backup safe. Here are the options (just so you know): | |||
| * The `-m` option applies `me_cleaner -S -d` before flashing back, see | |||
| [me_cleaner](https://github.com/corna/me_cleaner). | |||
| * The `-l` option will (re-)lock your flash ROM, in case you want to force | |||
| yourself (and others) to hardware-flashing, see [updating](#updating). | |||
| #### Your BIOS choice: the 4MB chip | |||
| Now it's time to make your choice! Choose one of the images included in our | |||
| release and select it during running: | |||
| sudo ./external_install_top.sh -k <backup-file-to-create> | |||
| This selects and flashes it and that's it. | |||
| Keep the backup safe, assemble and | |||
| turn on the T430. coreboot will do hardware init and start SeaBIOS. | |||
| ## Updating | |||
| If you have locked your flash (i.e. `./external_install_bottom -l`) you can | |||
| flash externally using `external_install_top.sh` just like the | |||
| first time, see above. Only the "upper" 4MB chip has to be written. | |||
| It is recommended to do the the update directly on your T430 using Linux | |||
| though. This is considered more safe for your hardware and is very convenient - | |||
| just install the "flashrom" program and run `./t430_skulls.sh`, see below. | |||
| 1. boot Linux with the `iomem=relaxed` boot parameter (for example in /etc/default/grub `GRUB_CMDLINE_LINUX_DEFAULT`) | |||
| 2. [download](https://github.com/merge/skulls/releases) the latest Skulls release tarball and unpack it or check for updates by running `./t430_skulls.sh -U`. | |||
| 3. run `sudo ./t430_skulls.sh` and choose the image to flash. | |||
| Hint: In case your Linux distribution's GRUB bootloader doesn't use the full | |||
| screen, put the line `GRUB_GFXMODE=1366x768x32` in your `/etc/default/grub` file | |||
| (and run `update_grub`). | |||
| ## Moving to Heads | |||
| [Heads](http://osresearch.net/) is an alternative BIOS system with advanced | |||
| security features. It's more complicated to use though. When having Skulls | |||
| installed, installing Heads is as easy as updating Skulls. You can directly | |||
| start using it: | |||
| * [build Heads](https://github.com/osresearch/heads) | |||
| * boot Linux with the `iomem=relaxed` boot parameter | |||
| * copy Heads' 12M image file `build/t430/coreboot.rom` to Skulls' t430 directory | |||
| * run `sudo ./t430_heads.sh` | |||
| That's it. Heads is a completely different project. Please read the | |||
| [documentation](http://osresearch.net/) for how to use it and report bugs | |||
| [over there](https://github.com/osresearch/heads/issues) | |||
| Switching back to Skulls is the same as [updating](#updating). Just run | |||
| `./t430_skulls.sh`. | |||
| ## Why does this work? | |||
| On the T430, there are 2 physical "BIOS" chips. The "upper" 4MB | |||
| one holds the actual bios we can generate using coreboot, and the "lower" 8MB | |||
| one holds the rest that you can [modify yourself once](#first-time-installation), | |||
| if you like, but strictly speaking, you | |||
| [don't need to touch it at all](https://www.coreboot.org/Board:lenovo/t430#Building_Firmware). | |||
| What's this "rest"? | |||
| Mainly a tiny binary used by the Ethernet card and the Intel Management Engine. | |||
| Read the [coreboot documentation](https://doc.coreboot.org/mainboard/lenovo/xx30_series.html) | |||
| for more details. | |||
| ## how to reproduce the release images | |||
| * `git clone https://github.com/merge/skulls` | |||
| * `cd skulls/t430` | |||
| * `git checkout 0.1.5` for the release you want to build. In this example 0.1.5. | |||
| * `./build.sh` and choose the configuration you want to build | |||
| ### replace the splashscreen image | |||
| In order to create your own splashscreen image, before building, | |||
| overwrite the `splashscreen.jpg` with your own JPEG, using | |||
| * "Progressive" turned off, and | |||
| * "4:2:0 (chroma quartered)" Subsampling | |||
BIN
t430/bootsplash.jpg
View File
BIN
t430/bootsplash.xcf
View File
+ 81
- 0
t430/build.sh
View File
| @ -0,0 +1,81 @@ | |||
| #!/bin/bash | |||
| source "util/functions.sh" | |||
| warn_not_root | |||
| have_config=0 | |||
| usage() | |||
| { | |||
| echo "Skulls for the T430" | |||
| echo " Run this script to rebuild a released image" | |||
| echo "" | |||
| echo "Usage: $0 [-c <config_file>]" | |||
| echo "" | |||
| echo " -c <config_file> to use for flashrom" | |||
| } | |||
| args=$(getopt -o c:h -- "$@") | |||
| if [ $? -ne 0 ] ; then | |||
| usage | |||
| exit 1 | |||
| fi | |||
| eval set -- "$args" | |||
| while [ $# -gt 0 ] | |||
| do | |||
| case "$1" in | |||
| -c) | |||
| CONFIGFILE=$2 | |||
| have_config=1 | |||
| shift | |||
| ;; | |||
| -h) | |||
| usage | |||
| exit 1 | |||
| ;; | |||
| --) | |||
| shift | |||
| break | |||
| ;; | |||
| *) | |||
| echo "Invalid option: $1" | |||
| exit 1 | |||
| ;; | |||
| esac | |||
| shift | |||
| done | |||
| if [ ! "$have_config" -gt 0 ] ; then | |||
| configs_available=$(ls -1 | grep config || true) | |||
| if [ -z "${configs_available}" ] ; then | |||
| echo "No config file found. Please add -c <file>" | |||
| echo "" | |||
| usage | |||
| exit 1 | |||
| fi | |||
| prompt="Please select a configuration to use for building or start with the -c option to use a different one:" | |||
| options=( $(find -maxdepth 1 -name "*config*" -print0 | xargs -0) ) | |||
| PS3="$prompt " | |||
| select CONFIGFILE in "${options[@]}" "Quit" ; do | |||
| if (( REPLY == 1 + ${#options[@]} )) ; then | |||
| exit | |||
| elif (( REPLY > 0 && REPLY <= ${#options[@]} )) ; then | |||
| break | |||
| else | |||
| echo "Invalid option. Try another one." | |||
| fi | |||
| done | |||
| fi | |||
| rm -f defconfig-* | |||
| CONFIGFILE_READY=$(echo $CONFIGFILE | cut -d'-' -f2-) | |||
| cp $CONFIGFILE $CONFIGFILE_READY | |||
| cd .. | |||
| ./build.sh --clean-slate --commit $(ls -1 t430/defconfig-* | cut -d'-' -f2-) t430 | |||
| rm -f t430/defconfig-* | |||
BIN
t430/ch341a.jpg
View File
+ 46
- 0
t430/compile.sh
View File
| @ -0,0 +1,46 @@ | |||
| #!/bin/bash | |||
| # SPDX-License-Identifier: GPL-3.0+ | |||
| # Copyright (C) 2018, Tom Hiller <thrilleratplay@gmail.com> | |||
| # shellcheck disable=SC1091 | |||
| source /home/coreboot/common_scripts/variables.sh | |||
| source /home/coreboot/common_scripts/download_coreboot.sh | |||
| source /home/coreboot/common_scripts/config_and_make.sh | |||
| ################################################################################ | |||
| ## MODEL VARIABLES | |||
| ################################################################################ | |||
| MAINBOARD="lenovo" | |||
| MODEL="t430" | |||
| ################################################################################ | |||
| ############################################### | |||
| ## download/git clone/git pull Coreboot ## | |||
| ############################################### | |||
| downloadOrUpdateCoreboot | |||
| ############################## | |||
| ## Copy config and make ## | |||
| ############################## | |||
| configAndMake | |||
| ##################### | |||
| ## Post build ## | |||
| ##################### | |||
| if [ ! -f "$DOCKER_COREBOOT_DIR/build/coreboot.rom" ]; then | |||
| echo "Uh oh. Things did not go according to plan." | |||
| exit 1; | |||
| else | |||
| #split out top BIOS | |||
| if [ ! -z "$COREBOOT_COMMIT" ]; then | |||
| RELEASEFILE="${MODEL}_coreboot_seabios_$(echo ${COREBOOT_COMMIT} | cut -c 1-10)_top.rom" | |||
| else | |||
| RELEASEFILE="coreboot_$MAINBOARD-$MODEL-top.rom" | |||
| fi | |||
| dd if="$DOCKER_COREBOOT_DIR/build/coreboot.rom" of="$DOCKER_COREBOOT_DIR/$RELEASEFILE" bs=1M skip=8 | |||
| sha256sum "$DOCKER_COREBOOT_DIR/$RELEASEFILE" > "$DOCKER_COREBOOT_DIR/${RELEASEFILE}".sha256 | |||
| echo "==================== result: ======================" | |||
| echo "$DOCKER_COREBOOT_DIR/$RELEASEFILE" | |||
| echo "===================================================" | |||
| fi | |||
+ 257
- 0
t430/external_install_bottom.sh
View File
| @ -0,0 +1,257 @@ | |||
| #!/bin/bash | |||
| # SPDX-License-Identifier: GPL-3.0+ | |||
| # Copyright (C) 2018, Martin Kepplinger <martink@posteo.de> | |||
| RED='\033[0;31m' | |||
| GREEN='\033[0;32m' | |||
| NC='\033[0m' | |||
| set -e | |||
| cd "$(dirname "$0")" | |||
| IFDTOOL_PATH=./util/ifdtool/ifdtool | |||
| ME_CLEANER_PATH=./util/me_cleaner/me_cleaner.py | |||
| have_chipname=0 | |||
| have_backupname=0 | |||
| me_clean=0 | |||
| lock=0 | |||
| have_flasher=0 | |||
| rpi_frequency=0 | |||
| usage() | |||
| { | |||
| echo "Skulls for the T430" | |||
| echo " Run this script on an external computer with a flasher" | |||
| echo " connected to the T430's bottom chip (closer to the HDD/SSD SATA" | |||
| echo " connector, further from the connector for the CD)." | |||
| echo "" | |||
| echo "Usage: $0 [-m] [-k <backup_filename>] [-l] [-f <flasher>] [-b <spispeed>] [-c <chip>]" | |||
| echo "" | |||
| echo " -f <hardware_flasher> supported flashers: rpi, ch341a" | |||
| echo " -c <chipname> flashrom chip name to use" | |||
| echo " -m apply me_cleaner -S -d" | |||
| echo " -l lock the flash instead of unlocking it" | |||
| echo " -k <backup> save the current image as" | |||
| echo " -b <spi frequency> frequency of the RPi SPI bus in Hz. default: 128" | |||
| } | |||
| args=$(getopt -o f:mlc:k:hb: -- "$@") | |||
| if [ $? -ne 0 ] ; then | |||
| usage | |||
| exit 1 | |||
| fi | |||
| eval set -- "$args" | |||
| while [ $# -gt 0 ] | |||
| do | |||
| case "$1" in | |||
| -f) | |||
| FLASHER=$2 | |||
| have_flasher=1 | |||
| shift | |||
| ;; | |||
| -m) | |||
| me_clean=1 | |||
| ;; | |||
| -l) | |||
| lock=1 | |||
| ;; | |||
| -c) | |||
| CHIPNAME=$2 | |||
| have_chipname=1 | |||
| shift | |||
| ;; | |||
| -k) | |||
| BACKUPNAME=$2 | |||
| have_backupname=1 | |||
| shift | |||
| ;; | |||
| -b) | |||
| rpi_frequency=$2 | |||
| shift | |||
| ;; | |||
| -h) | |||
| usage | |||
| exit 1 | |||
| ;; | |||
| --) | |||
| shift | |||
| break | |||
| ;; | |||
| *) | |||
| echo "Invalid option: $1" | |||
| usage | |||
| exit 1 | |||
| ;; | |||
| esac | |||
| shift | |||
| done | |||
| command -v flashrom >/dev/null 2>&1 || { echo -e >&2 "${RED}Please install flashrom and run as root${NC}."; exit 1; } | |||
| command -v make >/dev/null 2>&1 || { echo -e >&2 "${RED}Please install make and a C compiler${NC}."; exit 1; } | |||
| command -v mktemp >/dev/null 2>&1 || { echo -e >&2 "${RED}Please install mktemp (coreutils)${NC}."; exit 1; } | |||
| if [ ! "$have_flasher" -gt 0 ] ; then | |||
| echo "Skulls for the T430" | |||
| echo "" | |||
| echo "Please select the hardware you use:" | |||
| PS3='Please select the hardware flasher: ' | |||
| options=("Raspberry Pi" "CH341A" "Exit") | |||
| select opt in "${options[@]}" | |||
| do | |||
| case $opt in | |||
| "Raspberry Pi") | |||
| FLASHER="rpi" | |||
| break | |||
| ;; | |||
| "CH341A") | |||
| FLASHER="ch341a" | |||
| break | |||
| ;; | |||
| "Exit") | |||
| exit 0 | |||
| ;; | |||
| *) echo invalid option;; | |||
| esac | |||
| done | |||
| fi | |||
| if [ ! "${rpi_frequency}" -gt 0 ] ; then | |||
| rpi_frequency=512 | |||
| fi | |||
| programmer="" | |||
| if [ "${FLASHER}" = "rpi" ] ; then | |||
| echo "Ok. Run this on a Rasperry Pi." | |||
| programmer="linux_spi:dev=/dev/spidev0.0,spispeed=${rpi_frequency}" | |||
| elif [ "${FLASHER}" = "ch341a" ] ; then | |||
| echo "Ok. Connect a CH341A programmer" | |||
| programmer="ch341a_spi" | |||
| else | |||
| echo "invalid flashrom programmer" | |||
| usage | |||
| exit 1 | |||
| fi | |||
| TEMP_DIR=$(mktemp -d) | |||
| if [ ! -d "$TEMP_DIR" ]; then | |||
| echo -e "${RED}Error:${NC} Could not create temp dir" | |||
| rm -rf "${TEMP_DIR}" | |||
| exit 1 | |||
| fi | |||
| if [ ! "$have_chipname" -gt 0 ] ; then | |||
| echo "trying to detect the chip..." | |||
| flashrom -p ${programmer} &> "${TEMP_DIR}"/chips || true | |||
| flashrom_error="" | |||
| flashrom_error=$(cat "${TEMP_DIR}"/chips | grep -i error || true) | |||
| if [ ! -z "${flashrom_error}" ] ; then | |||
| usage | |||
| echo "-------------- flashrom error: ---------------" | |||
| cat "${TEMP_DIR}"/chips | |||
| rm -rf "${TEMP_DIR}" | |||
| exit 1 | |||
| fi | |||
| CHIPNAME="" | |||
| chip_found=0 | |||
| if [ ! "$chip_found" -gt 0 ] ; then | |||
| CHIPNAME=$(cat "${TEMP_DIR}"/chips | grep Found | grep "MX25L6406E/MX25L6408E" | grep -oP '"\K[^"\047]+(?=["\047])' || true) | |||
| if [ ! -z "${CHIPNAME}" ] ; then | |||
| chip_found=1 | |||
| fi | |||
| fi | |||
| if [ ! "$chip_found" -gt 0 ] ; then | |||
| CHIPNAME=$(cat "${TEMP_DIR}"/chips | grep Found | grep "EN25QH64" | grep -o '".*"' | grep -oP '"\K[^"\047]+(?=["\047])' || true) | |||
| if [ ! -z "${CHIPNAME}" ] ; then | |||
| chip_found=1 | |||
| fi | |||
| fi | |||
| if [ ! "$chip_found" -gt 0 ] ; then | |||
| echo "chip not detected." | |||
| flashrom -p ${programmer} || true | |||
| rm -rf "${TEMP_DIR}" | |||
| echo "chip not detected. Please find it manually and rerun with the -c parameter." | |||
| exit 1 | |||
| else | |||
| echo -e "Detected ${GREEN}${CHIPNAME}${NC}." | |||
| fi | |||
| fi | |||
| make -C util/ifdtool | |||
| if [ ! -e ${IFDTOOL_PATH} ] ; then | |||
| echo "ifdtool not found at ${IFDTOOL_PATH}" | |||
| exit 1 | |||
| fi | |||
| if [ ! "$me_clean" -gt 0 ] ; then | |||
| echo -e "Intel ME will ${RED}not${NC} be cleaned. Use -m if it should be." | |||
| else | |||
| echo -e "Intel ME will be ${GREEN}cleaned${NC}." | |||
| fi | |||
| if [ ! "$lock" -gt 0 ] ; then | |||
| echo -e "The flash ROM will be ${GREEN}unlocked${NC}." | |||
| else | |||
| echo -e "The flash ROM will be ${RED}locked${NC}." | |||
| fi | |||
| if [ "$me_clean" -gt 0 ] ; then | |||
| if [ ! -e ${ME_CLEANER_PATH} ] ; then | |||
| echo "me_cleaner not found at ${ME_CLEANER_PATH}" | |||
| rm -rf "${TEMP_DIR}" | |||
| exit 1 | |||
| fi | |||
| fi | |||
| echo "Start reading 2 times. Please be patient..." | |||
| flashrom -p ${programmer} -c ${CHIPNAME} -r "${TEMP_DIR}"/test1.rom | |||
| flashrom -p ${programmer} -c ${CHIPNAME} -r "${TEMP_DIR}"/test2.rom | |||
| cmp --silent "${TEMP_DIR}"/test1.rom "${TEMP_DIR}"/test2.rom | |||
| if [ "$have_backupname" -gt 0 ] ; then | |||
| cp "${TEMP_DIR}"/test1.rom "${BACKUPNAME}" | |||
| echo "current image saved as ${BACKUPNAME}" | |||
| fi | |||
| reference_size=8388608 | |||
| TEMP_SIZE=$(wc -c <"$TEMP_DIR/test1.rom") | |||
| if [ ! "$reference_size" -eq "$TEMP_SIZE" ] ; then | |||
| echo -e "${RED}Error:${NC} didn't read 8M. You might be at the wrong chip." | |||
| rm -rf "${TEMP_DIR}" | |||
| exit 1 | |||
| fi | |||
| echo -e "${GREEN}connection ok${NC}" | |||
| echo "start unlocking ..." | |||
| if [ "$me_clean" -gt 0 ] ; then | |||
| ${ME_CLEANER_PATH} -d -S -O "${TEMP_DIR}"/work.rom "${TEMP_DIR}"/test1.rom | |||
| else | |||
| cp "${TEMP_DIR}"/test1.rom "${TEMP_DIR}"/work.rom | |||
| fi | |||
| if [ ! "$lock" -gt 0 ] ; then | |||
| ${IFDTOOL_PATH} -u "${TEMP_DIR}"/work.rom | |||
| else | |||
| ${IFDTOOL_PATH} -l "${TEMP_DIR}"/work.rom | |||
| fi | |||
| if [ ! -e "${TEMP_DIR}"/work.rom.new ] ; then | |||
| echo -e "${RED}Error:${NC} ifdtool failed. ${TEMP_DIR}/work.rom.new not found." | |||
| rm -rf "${TEMP_DIR}" | |||
| exit 1 | |||
| fi | |||
| if [ "$me_clean" -gt 0 ] ; then | |||
| echo -e "${GREEN}ifdtool and me_cleaner ok${NC}" | |||
| else | |||
| echo -e "${GREEN}ifdtool ok${NC}" | |||
| fi | |||
| make clean -C util/ifdtool | |||
| echo "start writing..." | |||
| flashrom -p ${programmer} -c "${CHIPNAME}" -w "${TEMP_DIR}"/work.rom.new | |||
| rm -rf "${TEMP_DIR}" | |||
| echo -e "${GREEN}DONE${NC}" | |||
+ 218
- 0
t430/external_install_top.sh
View File
| @ -0,0 +1,218 @@ | |||
| #!/bin/bash | |||
| # SPDX-License-Identifier: GPL-3.0+ | |||
| # Copyright (C) 2018, Martin Kepplinger <martink@posteo.de> | |||
| RED='\033[0;31m' | |||
| GREEN='\033[0;32m' | |||
| NC='\033[0m' | |||
| set -e | |||
| have_input_image=0 | |||
| have_chipname=0 | |||
| have_backupname=0 | |||
| have_flasher=0 | |||
| rpi_frequency=0 | |||
| usage() | |||
| { | |||
| echo "Skulls for the T430" | |||
| echo " Run this script on an external computer with a flasher" | |||
| echo " connected to the T430's top chip (closer to the display" | |||
| echo " and farther from you)" | |||
| echo "" | |||
| echo "Usage: $0 [-i <image.rom>] [-c <chipname>] [-k <backup_filename>] [-f <flasher>] [-b <spispeed>]" | |||
| echo "" | |||
| echo " -f <hardware_flasher> supported flashers: rpi, ch341a" | |||
| echo " -i <image> path to image to flash" | |||
| echo " -c <chipname> to use for flashrom" | |||
| echo " -k <backup> save the current image as" | |||
| echo " -b <spi frequency> frequency of the RPi SPI bus in Hz. default: 128" | |||
| } | |||
| args=$(getopt -o f:i:c:k:hb: -- "$@") | |||
| if [ $? -ne 0 ] ; then | |||
| usage | |||
| exit 1 | |||
| fi | |||
| eval set -- "$args" | |||
| while [ $# -gt 0 ] | |||
| do | |||
| case "$1" in | |||
| -f) | |||
| FLASHER=$2 | |||
| have_flasher=1 | |||
| shift | |||
| ;; | |||
| -i) | |||
| INPUT_IMAGE_PATH=$2 | |||
| have_input_image=1 | |||
| shift | |||
| ;; | |||
| -c) | |||
| CHIPNAME=$2 | |||
| have_chipname=1 | |||
| shift | |||
| ;; | |||
| -k) | |||
| BACKUPNAME=$2 | |||
| have_backupname=1 | |||
| shift | |||
| ;; | |||
| -b) | |||
| rpi_frequency=$2 | |||
| shift | |||
| ;; | |||
| -h) | |||
| usage | |||
| exit 1 | |||
| ;; | |||
| --) | |||
| shift | |||
| break | |||
| ;; | |||
| *) | |||
| echo "Invalid option: $1" | |||
| exit 1 | |||
| ;; | |||
| esac | |||
| shift | |||
| done | |||
| command -v flashrom >/dev/null 2>&1 || { echo -e >&2 "${RED}Please install flashrom and run as root${NC}."; exit 1; } | |||
| command -v mktemp >/dev/null 2>&1 || { echo -e >&2 "${RED}Please install mktemp (coreutils)${NC}."; exit 1; } | |||
| if [ ! "$have_input_image" -gt 0 ] ; then | |||
| image_available=$(ls -1 | grep t430_coreboot_seabios || true) | |||
| if [ -z "${image_available}" ] ; then | |||
| echo "No image file found. Please add -i <file>" | |||
| echo "" | |||
| usage | |||
| exit 1 | |||
| fi | |||
| prompt="Please select a file to flash or start with the -i option to use a different one:" | |||
| options=( $(find -maxdepth 1 -name "*rom" -print0 | xargs -0) ) | |||
| PS3="$prompt " | |||
| select INPUT_IMAGE_PATH in "${options[@]}" "Quit" ; do | |||
| if (( REPLY == 1 + ${#options[@]} )) ; then | |||
| exit | |||
| elif (( REPLY > 0 && REPLY <= ${#options[@]} )) ; then | |||
| break | |||
| else | |||
| echo "Invalid option. Try another one." | |||
| fi | |||
| done | |||
| fi | |||
| if [ ! "$have_flasher" -gt 0 ] ; then | |||
| echo "Please select the hardware you use:" | |||
| PS3='Please select the hardware flasher: ' | |||
| options=("Raspberry Pi" "CH341A" "Quit") | |||
| select opt in "${options[@]}" | |||
| do | |||
| case $opt in | |||
| "Raspberry Pi") | |||
| FLASHER="rpi" | |||
| break | |||
| ;; | |||
| "CH341A") | |||
| FLASHER="ch341a" | |||
| break | |||
| ;; | |||
| "Quit") | |||
| exit 0 | |||
| ;; | |||
| *) echo invalid option;; | |||
| esac | |||
| done | |||
| fi | |||
| if [ ! "${rpi_frequency}" -gt 0 ] ; then | |||
| rpi_frequency=512 | |||
| fi | |||
| programmer="" | |||
| if [ "${FLASHER}" = "rpi" ] ; then | |||
| programmer="linux_spi:dev=/dev/spidev0.0,spispeed=${rpi_frequency}" | |||
| elif [ "${FLASHER}" = "ch341a" ] ; then | |||
| programmer="ch341a_spi" | |||
| else | |||
| echo "invalid flashrom programmer" | |||
| usage | |||
| exit 1 | |||
| fi | |||
| TEMP_DIR=$(mktemp -d) | |||
| if [ ! -d "$TEMP_DIR" ]; then | |||
| echo "${RED}Error:${NC} Could not create temp dir" | |||
| exit 1 | |||
| fi | |||
| if [ ! "$have_chipname" -gt 0 ] ; then | |||
| echo "trying to detect the chip..." | |||
| flashrom -p ${programmer} &> "${TEMP_DIR}"/chips || true | |||
| flashrom_error="" | |||
| flashrom_error=$(cat "${TEMP_DIR}"/chips | grep -i error || true) | |||
| if [ ! -z "${flashrom_error}" ] ; then | |||
| cat "${TEMP_DIR}"/chips | |||
| rm -rf "${TEMP_DIR}" | |||
| exit 1 | |||
| fi | |||
| CHIPNAME="" | |||
| chip_found=0 | |||
| if [ ! "$chip_found" -gt 0 ] ; then | |||
| CHIPNAME=$(cat "${TEMP_DIR}"/chips | grep Found | grep MX25L3206E | grep -oP '"\K[^"\047]+(?=["\047])' || true) | |||
| if [ ! -z "${CHIPNAME}" ] ; then | |||
| chip_found=1 | |||
| fi | |||
| fi | |||
| if [ ! "$chip_found" -gt 0 ] ; then | |||
| CHIPNAME=$(cat "${TEMP_DIR}"/chips | grep Found | grep EN25QH32 | grep -oP '"\K[^"\047]+(?=["\047])' || true) | |||
| if [ ! -z "${CHIPNAME}" ] ; then | |||
| chip_found=1 | |||
| fi | |||
| fi | |||
| if [ ! "$chip_found" -gt 0 ] ; then | |||
| echo "chip not detected." | |||
| flashrom -p ${programmer} || true | |||
| rm -rf "${TEMP_DIR}" | |||
| echo "Please find it manually in the list above and rerun with the -c parameter." | |||
| exit 1 | |||
| else | |||
| echo -e "Detected ${GREEN}${CHIPNAME}${NC}." | |||
| fi | |||
| fi | |||
| INPUT_IMAGE_NAME=$(basename "${INPUT_IMAGE_PATH}") | |||
| INPUT_IMAGE_SIZE=$(wc -c < "$INPUT_IMAGE_PATH") | |||
| reference_filesize=4194304 | |||
| if [ ! "$INPUT_IMAGE_SIZE" -eq "$reference_filesize" ] ; then | |||
| echo -e "${RED}Error:${NC} input file must be 4MB of size" | |||
| exit 1 | |||
| fi | |||
| echo "verifying SPI connection by reading 2 times. please wait." | |||
| flashrom -p ${programmer} -c ${CHIPNAME} -r ${TEMP_DIR}/test1.rom | |||
| flashrom -p ${programmer} -c ${CHIPNAME} -r ${TEMP_DIR}/test2.rom | |||
| cmp --silent "${TEMP_DIR}"/test1.rom "${TEMP_DIR}"/test2.rom | |||
| if [ "$have_backupname" -gt 0 ] ; then | |||
| cp "${TEMP_DIR}"/test1.rom "${BACKUPNAME}" | |||
| echo "current image saved as ${BACKUPNAME}" | |||
| fi | |||
| TEMP_SIZE=$(wc -c < "$TEMP_DIR/test1.rom") | |||
| if [ ! "$INPUT_IMAGE_SIZE" -eq "$TEMP_SIZE" ] ; then | |||
| echo -e "${RED}Error:${NC} read image (${TEMP_SIZE}) has different size that new image $INPUT_IMAGE_NAME (${INPUT_IMAGE_SIZE})" | |||
| exit 1 | |||
| fi | |||
| rm -rf "${TEMP_DIR}" | |||
| echo -e "${GREEN}connection ok${NC}. flashing ${INPUT_IMAGE_NAME}" | |||
| flashrom -p ${programmer} -c "${CHIPNAME}" -w "${INPUT_IMAGE_PATH}" | |||
| echo -e "${GREEN}DONE${NC}" | |||
+ 11
- 0
t430/free-defconfig-555419f356
View File
| @ -0,0 +1,11 @@ | |||
| CONFIG_USE_OPTION_TABLE=y | |||
| CONFIG_VENDOR_LENOVO=y | |||
| CONFIG_CBFS_SIZE=0x400000 | |||
| CONFIG_BOARD_LENOVO_THINKPAD_T430=y | |||
| # CONFIG_H8_BEEP_ON_DEATH is not set | |||
| CONFIG_GENERIC_LINEAR_FRAMEBUFFER=y | |||
| CONFIG_DEFAULT_CONSOLE_LOGLEVEL_8=y | |||
| CONFIG_NO_POST=y | |||
| CONFIG_COREINFO_SECONDARY_PAYLOAD=y | |||
| CONFIG_MEMTEST_SECONDARY_PAYLOAD=y | |||
| CONFIG_NVRAMCUI_SECONDARY_PAYLOAD=y | |||
BIN
t430/front.jpg
View File
+ 19
- 0
t430/nonfree-defconfig-555419f356
View File
| @ -0,0 +1,19 @@ | |||
| CONFIG_USE_OPTION_TABLE=y | |||
| CONFIG_USE_BLOBS=y | |||
| CONFIG_BOOTSPLASH_IMAGE=y | |||
| CONFIG_VENDOR_LENOVO=y | |||
| CONFIG_CBFS_SIZE=0x400000 | |||
| CONFIG_VGA_BIOS=y | |||
| CONFIG_BOARD_LENOVO_THINKPAD_T430=y | |||
| # CONFIG_S3_VGA_ROM_RUN is not set | |||
| # CONFIG_H8_BEEP_ON_DEATH is not set | |||
| CONFIG_VGA_ROM_RUN=y | |||
| CONFIG_PCI_OPTION_ROM_RUN_YABEL=y | |||
| CONFIG_FRAMEBUFFER_SET_VESA_MODE=y | |||
| CONFIG_BOOTSPLASH=y | |||
| CONFIG_VBE_LINEAR_FRAMEBUFFER=y | |||
| CONFIG_DEFAULT_CONSOLE_LOGLEVEL_8=y | |||
| CONFIG_NO_POST=y | |||
| CONFIG_COREINFO_SECONDARY_PAYLOAD=y | |||
| CONFIG_MEMTEST_SECONDARY_PAYLOAD=y | |||
| CONFIG_NVRAMCUI_SECONDARY_PAYLOAD=y | |||
BIN
t430/pci8086,0166.rom
View File
+ 149
- 0
t430/release.sh
View File
| @ -0,0 +1,149 @@ | |||
| #!/bin/bash | |||
| # SPDX-License-Identifier: GPL-3.0+ | |||
| # Copyright (C) 2018, Martin Kepplinger <martink@posteo.de> | |||
| # | |||
| # Script to build release-archives with. This requires a checkout from git. | |||
| # WARNING: This script is very dangerous! It may delete any untracked files. | |||
| set -e | |||
| have_version=0 | |||
| have_image=0 | |||
| have_image_2=0 | |||
| usage() | |||
| { | |||
| echo "Usage: $0 -v version -i release_image -f second_release_image" | |||
| } | |||
| args=$(getopt -o v:i:f: -- "$@") | |||
| if [ $? -ne 0 ] ; then | |||
| usage | |||
| exit 1 | |||
| fi | |||
| eval set -- "$args" | |||
| while [ $# -gt 0 ] | |||
| do | |||
| case "$1" in | |||
| -i) | |||
| RELEASE_IMAGE=$2 | |||
| have_image=1 | |||
| shift | |||
| ;; | |||
| -f) | |||
| RELEASE_IMAGE_2=$2 | |||
| have_image_2=1 | |||
| shift | |||
| ;; | |||
| -v) | |||
| version=$2 | |||
| have_version=1 | |||
| shift | |||
| ;; | |||
| --) | |||
| shift | |||
| break | |||
| ;; | |||
| *) | |||
| echo "Invalid option: $1" | |||
| usage | |||
| exit 1 | |||
| ;; | |||
| esac | |||
| shift | |||
| done | |||
| if [ ! "$have_image" -gt 0 ] ; then | |||
| echo "we currently need 2 release images" | |||
| usage | |||
| exit 1 | |||
| fi | |||
| if [ ! "$have_image_2" -gt 0 ] ; then | |||
| echo "we currently need 2 release images" | |||
| usage | |||
| exit 1 | |||
| fi | |||
| # Do we have a desired version number? | |||
| if [ "$have_version" -gt 0 ] ; then | |||
| echo "trying to build version $version" | |||
| else | |||
| echo "please specify a version" | |||
| usage | |||
| exit 1 | |||
| fi | |||
| # Version number sanity check | |||
| if grep "${version}" NEWS | |||
| then | |||
| echo "configurations seems ok" | |||
| else | |||
| echo "please check the NEWS file" | |||
| exit 1 | |||
| fi | |||
| # Check that we are on master | |||
| branch=$(git rev-parse --abbrev-ref HEAD) | |||
| echo "we are on branch $branch" | |||
| if [ ! "${branch}" = "master" ] ; then | |||
| echo "you don't seem to be on the master branch" | |||
| exit 1 | |||
| fi | |||
| if git diff-index --quiet HEAD --; then | |||
| # no changes | |||
| echo "there are no uncommitted changes (version bump)" | |||
| exit 1 | |||
| fi | |||
| echo "======================================================" | |||
| echo " are you fine with the following version bump?" | |||
| echo "======================================================" | |||
| git diff | |||
| echo "======================================================" | |||
| read -r -p " Press enter to continue" | |||
| echo "======================================================" | |||
| filesize=$(wc -c <"${RELEASE_IMAGE}") | |||
| reference_filesize=4194304 | |||
| if [ ! "$filesize" -eq "$reference_filesize" ] ; then | |||
| echo "filesize of release image is wrong" | |||
| exit 1 | |||
| fi | |||
| filesize=$(wc -c <"${RELEASE_IMAGE_2}") | |||
| reference_filesize=4194304 | |||
| if [ ! "$filesize" -eq "$reference_filesize" ] ; then | |||
| echo "filesize of release image is wrong" | |||
| exit 1 | |||
| fi | |||
| RELEASE_DIR="skulls-t430-${version}" | |||
| rm -rf "$RELEASE_DIR" | |||
| mkdir -p "$RELEASE_DIR" | |||
| # copy-in the ROMs | |||
| cp "${RELEASE_IMAGE}" "$RELEASE_DIR" | |||
| cp "${RELEASE_IMAGE_2}" "$RELEASE_DIR" | |||
| RELEASE_IMAGE_FILE=$(basename "${RELEASE_IMAGE}") | |||
| sha256sum ${RELEASE_DIR}/${RELEASE_IMAGE_FILE} > "${RELEASE_DIR}/${RELEASE_IMAGE_FILE}.sha256" | |||
| RELEASE_IMAGE_FILE_2=$(basename "${RELEASE_IMAGE_2}") | |||
| sha256sum ${RELEASE_DIR}/${RELEASE_IMAGE_FILE_2} > "${RELEASE_DIR}/${RELEASE_IMAGE_FILE_2}.sha256" | |||
| # copy in device independent stuff | |||
| cp ../SOURCE.md "$RELEASE_DIR" | |||
| # copy in t430 stuff | |||
| cp -a README.md NEWS util LICENSE* \ | |||
| t430_skulls.sh t430_heads.sh \ | |||
| external_install_bottom.sh external_install_top.sh \ | |||
| "$RELEASE_DIR" | |||
| tar -cJf "$RELEASE_DIR".tar.xz "$RELEASE_DIR" | |||
| rm -rf "$RELEASE_DIR" | |||
| git commit -a -m "update to ${version}" | |||
| git tag -s "${version}" -m "skulls-t430 ${version}" | |||
| sha256sum "$RELEASE_DIR".tar.xz > "$RELEASE_DIR".tar.xz.sha256 | |||
| sha512sum "$RELEASE_DIR".tar.xz > "$RELEASE_DIR".tar.xz.sha512 | |||
| gpg -b -a "$RELEASE_DIR".tar.xz | |||
BIN
t430/rpi_clip.jpg
View File
+ 133
- 0
t430/t430_heads.sh
View File
| @ -0,0 +1,133 @@ | |||
| #!/bin/bash | |||
| # SPDX-License-Identifier: GPL-3.0+ | |||
| # Copyright (C) 2018, Martin Kepplinger <martink@posteo.de> | |||
| set -e | |||
| cd "$(dirname "$0")" | |||
| source "util/functions.sh" | |||
| have_input_image=0 | |||
| usage() | |||
| { | |||
| echo "Skulls for the T430" | |||
| echo " Run this script on the T430 directly." | |||
| echo "" | |||
| echo " This flashes Heads to your BIOS, see http://osresearch.net" | |||
| echo " Heads is a different project. No image is included." | |||
| echo " Read https://github.com/osresearch/heads for how to build it" | |||
| echo " Make sure you booted Linux with iomem=relaxed" | |||
| echo "" | |||
| echo "Usage: $0 -i <heads_image>.rom" | |||
| } | |||
| args=$(getopt -o i:h -- "$@") | |||
| if [ $? -ne 0 ] ; then | |||
| usage | |||
| exit 1 | |||
| fi | |||
| eval set -- "$args" | |||
| while [ $# -gt 0 ] | |||
| do | |||
| case "$1" in | |||
| -i) | |||
| INPUT_IMAGE_PATH=$2 | |||
| have_input_image=1 | |||
| shift | |||
| ;; | |||
| -h) | |||
| usage | |||
| exit 1 | |||
| ;; | |||
| --) | |||
| shift | |||
| break | |||
| ;; | |||
| *) | |||
| echo "Invalid option: $1" | |||
| exit 1 | |||
| ;; | |||
| esac | |||
| shift | |||
| done | |||
| force_t430_and_root | |||
| if [ ! "$have_input_image" -gt 0 ] ; then | |||
| image_available=$(ls -1 | grep rom || true) | |||
| if [ -z "${image_available}" ] ; then | |||
| echo "No image file found. Please add -i <file>" | |||
| echo "" | |||
| usage | |||
| exit 1 | |||
| fi | |||
| prompt="file not specified. Please select a file to flash:" | |||
| options=( $(find -maxdepth 1 -name "*rom" -print0 | xargs -0) ) | |||
| PS3="$prompt " | |||
| select INPUT_IMAGE_PATH in "${options[@]}" "Quit" ; do | |||
| if (( REPLY == 1 + ${#options[@]} )) ; then | |||
| exit | |||
| elif (( REPLY > 0 && REPLY <= ${#options[@]} )) ; then | |||
| break | |||
| else | |||
| echo "Invalid option. Try another one." | |||
| fi | |||
| done | |||
| fi | |||
| OUTPUT_PATH=output | |||
| INPUT_IMAGE_NAME=$(basename "${INPUT_IMAGE_PATH}") | |||
| OUTPUT_IMAGE_NAME=${INPUT_IMAGE_NAME%%.*}_prepared.rom | |||
| OUTPUT_IMAGE_PATH=${OUTPUT_PATH}/${OUTPUT_IMAGE_NAME} | |||
| echo -e "input: ${INPUT_IMAGE_NAME}" | |||
| echo -e "output: ${OUTPUT_IMAGE_PATH}" | |||
| input_filesize=$(wc -c <"$INPUT_IMAGE_PATH") | |||
| reference_filesize=12582912 | |||
| if [ ! "$input_filesize" -eq "$reference_filesize" ] ; then | |||
| echo "Error: input file must be 12MB of size" | |||
| exit 1 | |||
| fi | |||
| rm -rf ${OUTPUT_PATH} | |||
| mkdir ${OUTPUT_PATH} | |||
| cp "${INPUT_IMAGE_PATH}" "${OUTPUT_IMAGE_PATH}" | |||
| LAYOUT_FILENAME="t430-layout-heads.txt" | |||
| echo "0x00000000:0x00000fff ifd" > ${OUTPUT_PATH}/${LAYOUT_FILENAME} | |||
| echo "0x00001000:0x00002fff gbe" >> ${OUTPUT_PATH}/${LAYOUT_FILENAME} | |||
| echo "0x00003000:0x004fffff me" >> ${OUTPUT_PATH}/${LAYOUT_FILENAME} | |||
| echo "0x00500000:0x00bfffff bios" >> ${OUTPUT_PATH}/${LAYOUT_FILENAME} | |||
| echo -e "${YELLOW}WARNING${NC}: Make sure not to power off your computer or interrupt this process in any way!" | |||
| echo -e " Interrupting this process may result in irreparable damage to your computer!" | |||
| check_battery | |||
| while true; do | |||
| read -r -p "Flash the BIOS now? y/N: " yn | |||
| case $yn in | |||
| [Yy]* ) cd ${OUTPUT_PATH} && flashrom -p internal --layout ${LAYOUT_FILENAME} --image bios -w "${OUTPUT_IMAGE_NAME}"; break;; | |||
| [Nn]* ) exit;; | |||
| * ) exit;; | |||
| esac | |||
| done | |||
| rm -rf ${OUTPUT_PATH} | |||
| while true; do | |||
| read -r -p "Reboot now? (please do!) Y/n: " yn | |||
| case $yn in | |||
| [Yy]* ) reboot ;; | |||
| [Nn]* ) exit;; | |||
| * ) reboot;; | |||
| esac | |||
| done | |||
+ 221
- 0
t430/t430_skulls.sh
View File
| @ -0,0 +1,221 @@ | |||
| #!/bin/bash | |||
| # SPDX-License-Identifier: GPL-3.0+ | |||
| # Copyright (C) 2019, Martin Kepplinger <martink@posteo.de> | |||
| set -e | |||
| cd "$(dirname "$0")" | |||
| source "util/functions.sh" | |||
| have_input_image=0 | |||
| request_update=0 | |||
| verbose=0 | |||
| usage() | |||
| { | |||
| echo "Skulls for the T430" | |||
| echo " Run this script on the T430 directly." | |||
| echo "" | |||
| echo " This flashes the BIOS with the given image." | |||
| echo " Make sure you booted Linux with iomem=relaxed" | |||
| echo "" | |||
| echo "Usage: $0 [-i <4mb_top_image>.rom] [-U] [-h]" | |||
| echo "Options:" | |||
| echo " -i path to the image to flash" | |||
| echo " -U update: check for a new Skulls package online" | |||
| echo " -v verbose output. prints more information" | |||
| echo " -h print this help text" | |||
| } | |||
| args=$(getopt -o i:hUv -- "$@") | |||
| if [ $? -ne 0 ] ; then | |||
| usage | |||
| exit 1 | |||
| fi | |||
| eval set -- "$args" | |||
| while [ $# -gt 0 ] | |||
| do | |||
| case "$1" in | |||
| -i) | |||
| INPUT_IMAGE_PATH=$2 | |||
| have_input_image=1 | |||
| shift | |||
| ;; | |||
| -h) | |||
| usage | |||
| exit 1 | |||
| ;; | |||
| -U) | |||
| request_update=1 | |||
| ;; | |||
| -v) | |||
| verbose=1 | |||
| ;; | |||
| --) | |||
| shift | |||
| break | |||
| ;; | |||
| *) | |||
| echo "Invalid option: $1" | |||
| exit 1 | |||
| ;; | |||
| esac | |||
| shift | |||
| done | |||
| if [ "$request_update" -gt 0 ] ; then | |||
| warn_not_root | |||
| command -v curl >/dev/null 2>&1 || { echo -e >&2 "${RED}Please install curl.${NC}"; exit 1; } | |||
| CURRENT_VERSION=$(head -2 NEWS | egrep -o "([0-9]{1,}\.)+[0-9]{1,}") | |||
| UPSTREAM_FILE=$(curl -s https://api.github.com/repos/merge/skulls/releases/latest | grep browser_download_url | cut -d'"' -f4 | cut -d'/' -f9 | head -n 1) | |||
| UPSTREAM_VERSION=$(curl -s https://api.github.com/repos/merge/skulls/releases/latest | grep browser_download_url | cut -d'"' -f4 | cut -d'/' -f9 | head -n 1 | egrep -o "([0-9]{1,}\.)+[0-9]{1,}") | |||
| UPSTREAM_T430=$(echo ${UPSTREAM_FILE} | grep t430) | |||
| if [[ -z "$UPSTREAM_T430" ]] ; then | |||
| echo "The latest release didn't include the T430" | |||
| exit 0 | |||
| fi | |||
| if [[ $verbose -gt 0 ]] ; then | |||
| echo "This is v$CURRENT_VERSION and latest is v$UPSTREAM_VERSION" | |||
| fi | |||
| if [[ "$CURRENT_VERSION" = "$UPSTREAM_VERSION" ]] ; then | |||
| echo -e "${GREEN}You are using the latest version of Skulls for the T430${NC}" | |||
| exit 0 | |||
| elif [[ "$CURRENT_VERSION" < "$UPSTREAM_VERSION" ]] ; then | |||
| echo -e "${RED}You have ${CURRENT_VERSION} but there is version ${UPSTREAM_VERSION} available for the T430. Please update.${NC}" | |||
| read -r -p "Download it to the parent directory now? [y/N] " response | |||
| case "$response" in | |||
| [yY][eE][sS]|[yY]) | |||
| UPSTREAM_URL=$(curl -s https://api.github.com/repos/merge/skulls/releases/latest | grep browser_download_url | cut -d'"' -f4 | head -n 1) | |||
| UPSTREAM_URL_SHA256=$(curl -s https://api.github.com/repos/merge/skulls/releases/latest | grep browser_download_url | cut -d'"' -f4 | head -n 3 | tail -n 1) | |||
| cd .. | |||
| curl -LO ${UPSTREAM_URL} | |||
| curl -LO ${UPSTREAM_URL_SHA256} | |||
| sha256sum -c ${UPSTREAM_FILE}.sha256 | |||
| mkdir skulls-t430-${UPSTREAM_VERSION} | |||
| tar -xf ${UPSTREAM_FILE} -C skulls-t430-${UPSTREAM_VERSION}/ | |||
| echo "Version ${UPSTREAM_VERSION} extracted to ../skulls-t430-${UPSTREAM_VERSION}/" | |||
| echo "Please continue in the new directory." | |||
| ;; | |||
| *) | |||
| exit 0 | |||
| ;; | |||
| esac | |||
| else | |||
| echo "You seem to use a development version. Please use release package skulls-t430 ${UPSTREAM_VERSION} for flashing." | |||
| fi | |||
| exit 0 | |||
| fi | |||
| force_t430_and_root | |||
| BIOS_VENDOR=$(dmidecode -t bios | grep Vendor | cut -d':' -f2) | |||
| if [[ $BIOS_VENDOR != *"coreboot"* ]] ; then | |||
| BIOS_VERSION=$(dmidecode -s bios-version | grep -o '[1-2].[0-7][0-9]') | |||
| bios_major=$(echo "$BIOS_VERSION" | cut -d. -f1) | |||
| bios_minor=$(echo "$BIOS_VERSION" | cut -d. -f2) | |||
| if [ "${bios_minor}" -ge "61" ] ; then | |||
| echo "Ready to use external_install_bottom.sh and external_install_top.sh" | |||
| echo "Please run both scripts from a different computer with a" | |||
| echo "hardware SPI flasher." | |||
| else | |||
| echo -e "The installed original BIOS is very old." | |||
| echo -e "${RED}Please upgrade${NC} from lenovo.com before installing coreboot." | |||
| fi | |||
| exit 0 | |||
| fi | |||
| if [[ "$verbose" -gt 0 ]] ; then | |||
| if [ -d "/sys/class/power_supply/BAT0" ] ; then | |||
| bat_last_full=$(cat /sys/class/power_supply/BAT0/charge_full) | |||
| bat_design_cap=$(cat /sys/class/power_supply/BAT0/charge_full_design) | |||
| bat_health=$(echo "scale=2 ; $bat_last_full/$bat_design_cap" | bc | sed 's/^\./0./') | |||
| echo "INFO: Battery hardware health is $bat_health%" | |||
| fi | |||
| fi | |||
| if [ ! "$have_input_image" -gt 0 ] ; then | |||
| image_available=$(ls -1 | grep t430_coreboot_seabios || true) | |||
| if [ -z "${image_available}" ] ; then | |||
| echo "No image file found. Please add -i <file>" | |||
| echo "" | |||
| usage | |||
| exit 1 | |||
| fi | |||
| prompt="file not specified. Please select a file to flash. Please read the README for details about the differences:" | |||
| options=( $(find -maxdepth 1 -name "t430_coreboot_seabios*rom" -print0 | xargs -0) ) | |||
| PS3="$prompt " | |||
| select INPUT_IMAGE_PATH in "${options[@]}" "Quit" ; do | |||
| if (( REPLY == 1 + ${#options[@]} )) ; then | |||
| exit | |||
| elif (( REPLY > 0 && REPLY <= ${#options[@]} )) ; then | |||
| break | |||
| else | |||
| echo "Invalid option. Try another one." | |||
| fi | |||
| done | |||
| fi | |||
| OUTPUT_PATH=output | |||
| INPUT_IMAGE_NAME=$(basename "${INPUT_IMAGE_PATH}") | |||
| OUTPUT_IMAGE_NAME=${INPUT_IMAGE_NAME%%.*}_prepared_12mb.rom | |||
| OUTPUT_IMAGE_PATH=${OUTPUT_PATH}/${OUTPUT_IMAGE_NAME} | |||
| echo -e "input: ${INPUT_IMAGE_NAME}" | |||
| echo -e "output: ${OUTPUT_IMAGE_PATH}" | |||
| input_filesize=$(wc -c <"$INPUT_IMAGE_PATH") | |||
| reference_filesize=4194304 | |||
| if [ ! "$input_filesize" -eq "$reference_filesize" ] ; then | |||
| echo "Error: input file must be 4MB of size" | |||
| exit 1 | |||
| fi | |||
| rm -rf ${OUTPUT_PATH} | |||
| mkdir ${OUTPUT_PATH} | |||
| dd if=/dev/zero of="${OUTPUT_IMAGE_PATH}" bs=4M count=2 status=none | |||
| dd if="${INPUT_IMAGE_PATH}" oflag=append conv=notrunc of="${OUTPUT_IMAGE_PATH}" bs=4M status=none | |||
| LAYOUT_FILENAME="t430-layout.txt" | |||
| echo "0x00000000:0x007fffff ifdmegbe" > ${OUTPUT_PATH}/${LAYOUT_FILENAME} | |||
| echo "0x00800000:0x00bfffff bios" >> ${OUTPUT_PATH}/${LAYOUT_FILENAME} | |||
| echo -e "${YELLOW}WARNING${NC}: Make sure not to power off your computer or interrupt this process in any way!" | |||
| echo -e " Interrupting this process may result in irreparable damage to your computer!" | |||
| check_battery | |||
| while true; do | |||
| read -r -p "Flash the BIOS now? y/N: " yn | |||
| case $yn in | |||
| [Yy]* ) cd ${OUTPUT_PATH} && flashrom -p internal --layout ${LAYOUT_FILENAME} --image bios -w "${OUTPUT_IMAGE_NAME}"; break;; | |||
| [Nn]* ) exit;; | |||
| * ) exit;; | |||
| esac | |||
| done | |||
| rm -rf ${OUTPUT_PATH} | |||
| while true; do | |||
| read -r -p "Reboot now? (please do!) Y/n: " yn | |||
| case $yn in | |||
| [Yy]* ) reboot ;; | |||
| [Nn]* ) exit;; | |||
| * ) reboot;; | |||
| esac | |||
| done | |||
+ 339
- 0
t430/util/COPYING
View File
| @ -0,0 +1,339 @@ | |||
| GNU GENERAL PUBLIC LICENSE | |||
| Version 2, June 1991 | |||
| Copyright (C) 1989, 1991 Free Software Foundation, Inc., | |||
| 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA | |||
| Everyone is permitted to copy and distribute verbatim copies | |||
| of this license document, but changing it is not allowed. | |||
| Preamble | |||
| The licenses for most software are designed to take away your | |||
| freedom to share and change it. By contrast, the GNU General Public | |||
| License is intended to guarantee your freedom to share and change free | |||
| software--to make sure the software is free for all its users. This | |||
| General Public License applies to most of the Free Software | |||
| Foundation's software and to any other program whose authors commit to | |||
| using it. (Some other Free Software Foundation software is covered by | |||
| the GNU Lesser General Public License instead.) You can apply it to | |||
| your programs, too. | |||
| When we speak of free software, we are referring to freedom, not | |||
| price. Our General Public Licenses are designed to make sure that you | |||
| have the freedom to distribute copies of free software (and charge for | |||
| this service if you wish), that you receive source code or can get it | |||
| if you want it, that you can change the software or use pieces of it | |||
| in new free programs; and that you know you can do these things. | |||
| To protect your rights, we need to make restrictions that forbid | |||
| anyone to deny you these rights or to ask you to surrender the rights. | |||
| These restrictions translate to certain responsibilities for you if you | |||
| distribute copies of the software, or if you modify it. | |||
| For example, if you distribute copies of such a program, whether | |||
| gratis or for a fee, you must give the recipients all the rights that | |||
| you have. You must make sure that they, too, receive or can get the | |||
| source code. And you must show them these terms so they know their | |||
| rights. | |||
| We protect your rights with two steps: (1) copyright the software, and | |||
| (2) offer you this license which gives you legal permission to copy, | |||
| distribute and/or modify the software. | |||
| Also, for each author's protection and ours, we want to make certain | |||
| that everyone understands that there is no warranty for this free | |||
| software. If the software is modified by someone else and passed on, we | |||
| want its recipients to know that what they have is not the original, so | |||
| that any problems introduced by others will not reflect on the original | |||
| authors' reputations. | |||
| Finally, any free program is threatened constantly by software | |||
| patents. We wish to avoid the danger that redistributors of a free | |||
| program will individually obtain patent licenses, in effect making the | |||
| program proprietary. To prevent this, we have made it clear that any | |||
| patent must be licensed for everyone's free use or not licensed at all. | |||
| The precise terms and conditions for copying, distribution and | |||
| modification follow. | |||
| GNU GENERAL PUBLIC LICENSE | |||
| TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION | |||
| 0. This License applies to any program or other work which contains | |||
| a notice placed by the copyright holder saying it may be distributed | |||
| under the terms of this General Public License. The "Program", below, | |||
| refers to any such program or work, and a "work based on the Program" | |||
| means either the Program or any derivative work under copyright law: | |||
| that is to say, a work containing the Program or a portion of it, | |||
| either verbatim or with modifications and/or translated into another | |||
| language. (Hereinafter, translation is included without limitation in | |||
| the term "modification".) Each licensee is addressed as "you". | |||
| Activities other than copying, distribution and modification are not | |||
| covered by this License; they are outside its scope. The act of | |||
| running the Program is not restricted, and the output from the Program | |||
| is covered only if its contents constitute a work based on the | |||
| Program (independent of having been made by running the Program). | |||
| Whether that is true depends on what the Program does. | |||
| 1. You may copy and distribute verbatim copies of the Program's | |||
| source code as you receive it, in any medium, provided that you | |||
| conspicuously and appropriately publish on each copy an appropriate | |||
| copyright notice and disclaimer of warranty; keep intact all the | |||
| notices that refer to this License and to the absence of any warranty; | |||
| and give any other recipients of the Program a copy of this License | |||
| along with the Program. | |||
| You may charge a fee for the physical act of transferring a copy, and | |||
| you may at your option offer warranty protection in exchange for a fee. | |||
| 2. You may modify your copy or copies of the Program or any portion | |||
| of it, thus forming a work based on the Program, and copy and | |||
| distribute such modifications or work under the terms of Section 1 | |||
| above, provided that you also meet all of these conditions: | |||
| a) You must cause the modified files to carry prominent notices | |||
| stating that you changed the files and the date of any change. | |||
| b) You must cause any work that you distribute or publish, that in | |||
| whole or in part contains or is derived from the Program or any | |||
| part thereof, to be licensed as a whole at no charge to all third | |||
| parties under the terms of this License. | |||
| c) If the modified program normally reads commands interactively | |||
| when run, you must cause it, when started running for such | |||
| interactive use in the most ordinary way, to print or display an | |||
| announcement including an appropriate copyright notice and a | |||
| notice that there is no warranty (or else, saying that you provide | |||
| a warranty) and that users may redistribute the program under | |||
| these conditions, and telling the user how to view a copy of this | |||
| License. (Exception: if the Program itself is interactive but | |||
| does not normally print such an announcement, your work based on | |||
| the Program is not required to print an announcement.) | |||
| These requirements apply to the modified work as a whole. If | |||
| identifiable sections of that work are not derived from the Program, | |||
| and can be reasonably considered independent and separate works in | |||
| themselves, then this License, and its terms, do not apply to those | |||
| sections when you distribute them as separate works. But when you | |||
| distribute the same sections as part of a whole which is a work based | |||
| on the Program, the distribution of the whole must be on the terms of | |||
| this License, whose permissions for other licensees extend to the | |||
| entire whole, and thus to each and every part regardless of who wrote it. | |||
| Thus, it is not the intent of this section to claim rights or contest | |||
| your rights to work written entirely by you; rather, the intent is to | |||
| exercise the right to control the distribution of derivative or | |||
| collective works based on the Program. | |||
| In addition, mere aggregation of another work not based on the Program | |||
| with the Program (or with a work based on the Program) on a volume of | |||
| a storage or distribution medium does not bring the other work under | |||
| the scope of this License. | |||
| 3. You may copy and distribute the Program (or a work based on it, | |||
| under Section 2) in object code or executable form under the terms of | |||
| Sections 1 and 2 above provided that you also do one of the following: | |||
| a) Accompany it with the complete corresponding machine-readable | |||
| source code, which must be distributed under the terms of Sections | |||
| 1 and 2 above on a medium customarily used for software interchange; or, | |||
| b) Accompany it with a written offer, valid for at least three | |||
| years, to give any third party, for a charge no more than your | |||
| cost of physically performing source distribution, a complete | |||
| machine-readable copy of the corresponding source code, to be | |||
| distributed under the terms of Sections 1 and 2 above on a medium | |||
| customarily used for software interchange; or, | |||
| c) Accompany it with the information you received as to the offer | |||
| to distribute corresponding source code. (This alternative is | |||
| allowed only for noncommercial distribution and only if you | |||
| received the program in object code or executable form with such | |||
| an offer, in accord with Subsection b above.) | |||
| The source code for a work means the preferred form of the work for | |||
| making modifications to it. For an executable work, complete source | |||
| code means all the source code for all modules it contains, plus any | |||
| associated interface definition files, plus the scripts used to | |||
| control compilation and installation of the executable. However, as a | |||
| special exception, the source code distributed need not include | |||
| anything that is normally distributed (in either source or binary | |||
| form) with the major components (compiler, kernel, and so on) of the | |||
| operating system on which the executable runs, unless that component | |||
| itself accompanies the executable. | |||
| If distribution of executable or object code is made by offering | |||
| access to copy from a designated place, then offering equivalent | |||
| access to copy the source code from the same place counts as | |||
| distribution of the source code, even though third parties are not | |||
| compelled to copy the source along with the object code. | |||
| 4. You may not copy, modify, sublicense, or distribute the Program | |||
| except as expressly provided under this License. Any attempt | |||
| otherwise to copy, modify, sublicense or distribute the Program is | |||
| void, and will automatically terminate your rights under this License. | |||
| However, parties who have received copies, or rights, from you under | |||
| this License will not have their licenses terminated so long as such | |||
| parties remain in full compliance. | |||
| 5. You are not required to accept this License, since you have not | |||
| signed it. However, nothing else grants you permission to modify or | |||
| distribute the Program or its derivative works. These actions are | |||
| prohibited by law if you do not accept this License. Therefore, by | |||
| modifying or distributing the Program (or any work based on the | |||
| Program), you indicate your acceptance of this License to do so, and | |||
| all its terms and conditions for copying, distributing or modifying | |||
| the Program or works based on it. | |||
| 6. Each time you redistribute the Program (or any work based on the | |||
| Program), the recipient automatically receives a license from the | |||
| original licensor to copy, distribute or modify the Program subject to | |||
| these terms and conditions. You may not impose any further | |||
| restrictions on the recipients' exercise of the rights granted herein. | |||
| You are not responsible for enforcing compliance by third parties to | |||
| this License. | |||
| 7. If, as a consequence of a court judgment or allegation of patent | |||
| infringement or for any other reason (not limited to patent issues), | |||
| conditions are imposed on you (whether by court order, agreement or | |||
| otherwise) that contradict the conditions of this License, they do not | |||
| excuse you from the conditions of this License. If you cannot | |||
| distribute so as to satisfy simultaneously your obligations under this | |||
| License and any other pertinent obligations, then as a consequence you | |||
| may not distribute the Program at all. For example, if a patent | |||
| license would not permit royalty-free redistribution of the Program by | |||
| all those who receive copies directly or indirectly through you, then | |||
| the only way you could satisfy both it and this License would be to | |||
| refrain entirely from distribution of the Program. | |||
| If any portion of this section is held invalid or unenforceable under | |||
| any particular circumstance, the balance of the section is intended to | |||
| apply and the section as a whole is intended to apply in other | |||
| circumstances. | |||
| It is not the purpose of this section to induce you to infringe any | |||
| patents or other property right claims or to contest validity of any | |||
| such claims; this section has the sole purpose of protecting the | |||
| integrity of the free software distribution system, which is | |||
| implemented by public license practices. Many people have made | |||
| generous contributions to the wide range of software distributed | |||
| through that system in reliance on consistent application of that | |||
| system; it is up to the author/donor to decide if he or she is willing | |||
| to distribute software through any other system and a licensee cannot | |||
| impose that choice. | |||
| This section is intended to make thoroughly clear what is believed to | |||
| be a consequence of the rest of this License. | |||
| 8. If the distribution and/or use of the Program is restricted in | |||
| certain countries either by patents or by copyrighted interfaces, the | |||
| original copyright holder who places the Program under this License | |||
| may add an explicit geographical distribution limitation excluding | |||
| those countries, so that distribution is permitted only in or among | |||
| countries not thus excluded. In such case, this License incorporates | |||
| the limitation as if written in the body of this License. | |||
| 9. The Free Software Foundation may publish revised and/or new versions | |||
| of the General Public License from time to time. Such new versions will | |||
| be similar in spirit to the present version, but may differ in detail to | |||
| address new problems or concerns. | |||
| Each version is given a distinguishing version number. If the Program | |||
| specifies a version number of this License which applies to it and "any | |||
| later version", you have the option of following the terms and conditions | |||
| either of that version or of any later version published by the Free | |||
| Software Foundation. If the Program does not specify a version number of | |||
| this License, you may choose any version ever published by the Free Software | |||
| Foundation. | |||
| 10. If you wish to incorporate parts of the Program into other free | |||
| programs whose distribution conditions are different, write to the author | |||
| to ask for permission. For software which is copyrighted by the Free | |||
| Software Foundation, write to the Free Software Foundation; we sometimes | |||
| make exceptions for this. Our decision will be guided by the two goals | |||
| of preserving the free status of all derivatives of our free software and | |||
| of promoting the sharing and reuse of software generally. | |||
| NO WARRANTY | |||
| 11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY | |||
| FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN | |||
| OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES | |||
| PROVIDE THE PROGRAM "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED | |||
| OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF | |||
| MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE RISK AS | |||
| TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE | |||
| PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING, | |||
| REPAIR OR CORRECTION. | |||
| 12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING | |||
| WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR | |||
| REDISTRIBUTE THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES, | |||
| INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING | |||
| OUT OF THE USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED | |||
| TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY | |||
| YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER | |||
| PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE | |||
| POSSIBILITY OF SUCH DAMAGES. | |||
| END OF TERMS AND CONDITIONS | |||
| How to Apply These Terms to Your New Programs | |||
| If you develop a new program, and you want it to be of the greatest | |||
| possible use to the public, the best way to achieve this is to make it | |||
| free software which everyone can redistribute and change under these terms. | |||
| To do so, attach the following notices to the program. It is safest | |||
| to attach them to the start of each source file to most effectively | |||
| convey the exclusion of warranty; and each file should have at least | |||
| the "copyright" line and a pointer to where the full notice is found. | |||
| <one line to give the program's name and a brief idea of what it does.> | |||
| Copyright (C) <year> <name of author> | |||
| This program is free software; you can redistribute it and/or modify | |||
| it under the terms of the GNU General Public License as published by | |||
| the Free Software Foundation; either version 2 of the License, or | |||
| (at your option) any later version. | |||
| This program is distributed in the hope that it will be useful, | |||
| but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| GNU General Public License for more details. | |||
| You should have received a copy of the GNU General Public License along | |||
| with this program; if not, write to the Free Software Foundation, Inc., | |||
| 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA. | |||
| Also add information on how to contact you by electronic and paper mail. | |||
| If the program is interactive, make it output a short notice like this | |||
| when it starts in an interactive mode: | |||
| Gnomovision version 69, Copyright (C) year name of author | |||
| Gnomovision comes with ABSOLUTELY NO WARRANTY; for details type `show w'. | |||
| This is free software, and you are welcome to redistribute it | |||
| under certain conditions; type `show c' for details. | |||
| The hypothetical commands `show w' and `show c' should show the appropriate | |||
| parts of the General Public License. Of course, the commands you use may | |||
| be called something other than `show w' and `show c'; they could even be | |||
| mouse-clicks or menu items--whatever suits your program. | |||
| You should also get your employer (if you work as a programmer) or your | |||
| school, if any, to sign a "copyright disclaimer" for the program, if | |||
| necessary. Here is a sample; alter the names: | |||
| Yoyodyne, Inc., hereby disclaims all copyright interest in the program | |||
| `Gnomovision' (which makes passes at compilers) written by James Hacker. | |||
| <signature of Ty Coon>, 1 April 1989 | |||
| Ty Coon, President of Vice | |||
| This General Public License does not permit incorporating your program into | |||
| proprietary programs. If your program is a subroutine library, you may | |||
| consider it more useful to permit linking proprietary applications with the | |||
| library. If this is what you want to do, use the GNU Lesser General | |||
| Public License instead of this License. | |||
+ 88
- 0
t430/util/commonlib/include/commonlib/cbfs.h
View File
| @ -0,0 +1,88 @@ | |||
| /* | |||
| * This file is part of the coreboot project. | |||
| * | |||
| * Copyright 2015 Google Inc. | |||
| * | |||
| * This program is free software; you can redistribute it and/or modify | |||
| * it under the terms of the GNU General Public License as published by | |||
| * the Free Software Foundation; version 2 of the License. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| */ | |||
| #ifndef _COMMONLIB_CBFS_H_ | |||
| #define _COMMONLIB_CBFS_H_ | |||
| #include <commonlib/cbfs_serialized.h> | |||
| #include <commonlib/region.h> | |||
| #include <vb2_api.h> | |||
| /* Object representing cbfs files. */ | |||
| struct cbfsf { | |||
| struct region_device metadata; | |||
| struct region_device data; | |||
| }; | |||
| /* Locate file by name and optional type. Returns 0 on succcess else < 0 on | |||
| * error.*/ | |||
| int cbfs_locate(struct cbfsf *fh, const struct region_device *cbfs, | |||
| const char *name, uint32_t *type); | |||
| static inline void cbfs_file_data(struct region_device *data, | |||
| const struct cbfsf *file) | |||
| { | |||
| rdev_chain(data, &file->data, 0, region_device_sz(&file->data)); | |||
| } | |||
| static inline void cbfs_file_metadata(struct region_device *metadata, | |||
| const struct cbfsf *file) | |||
| { | |||
| rdev_chain(metadata, &file->metadata, 0, | |||
| region_device_sz(&file->metadata)); | |||
| } | |||
| /* | |||
| * Provide a handle to each cbfs file within a cbfs. The prev pointer represents | |||
| * the previous file (NULL on first invocation). The next object gets filled | |||
| * out with the next file. This returns < 0 on error, 0 on finding the next | |||
| * file, and > 0 at end of cbfs. | |||
| */ | |||
| int cbfs_for_each_file(const struct region_device *cbfs, | |||
| const struct cbfsf *prev, struct cbfsf *fh); | |||
| /* | |||
| * Return the offset for each CBFS attribute in a CBFS file metadata region. | |||
| * The metadata must already be fully mapped by the caller. Will return the | |||
| * offset (relative to the start of the metadata) or 0 when there are no | |||
| * further attributes. Should be called with 0 to begin, then always with | |||
| * the previously returned value until it returns 0. | |||
| */ | |||
| size_t cbfs_for_each_attr(void *metadata, size_t metadata_size, | |||
| size_t last_offset); | |||
| /* | |||
| * Find out the decompression algorithm and decompressed size of a non-stage | |||
| * CBFS file (by parsing its metadata attributes), and return them with | |||
| * out-parameters. Returns 0 on success and < 0 on error. | |||
| */ | |||
| int cbfsf_decompression_info(struct cbfsf *fh, uint32_t *algo, size_t *size); | |||
| /* | |||
| * Return the CBFS file type as out-parameter. | |||
| * Returns 0 on success and < 0 on error. | |||
| */ | |||
| int cbfsf_file_type(struct cbfsf *fh, uint32_t *ftype); | |||
| /* | |||
| * Perform the vb2 hash over the CBFS region skipping empty file contents. | |||
| * Caller is responsible for providing the hash algorithm as well as storage | |||
| * for the final digest. Return 0 on success or non-zero on error. | |||
| */ | |||
| int cbfs_vb2_hash_contents(const struct region_device *cbfs, | |||
| enum vb2_hash_algorithm hash_alg, void *digest, | |||
| size_t digest_sz); | |||
| #endif | |||
+ 241
- 0
t430/util/commonlib/include/commonlib/cbfs_serialized.h
View File
| @ -0,0 +1,241 @@ | |||
| /* | |||
| * This file is part of the coreboot project. | |||
| * | |||
| * Copyright (C) 2008 Jordan Crouse <jordan@cosmicpenguin.net> | |||
| * Copyright (C) 2012 Google, Inc. | |||
| * Copyright (C) 2013 The Chromium OS Authors. All rights reserved. | |||
| * | |||
| * This file is dual-licensed. You can choose between: | |||
| * - The GNU GPL, version 2, as published by the Free Software Foundation | |||
| * - The revised BSD license (without advertising clause) | |||
| * | |||
| * --------------------------------------------------------------------------- | |||
| * This program is free software; you can redistribute it and/or modify | |||
| * it under the terms of the GNU General Public License as published by | |||
| * the Free Software Foundation; version 2 of the License. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| * --------------------------------------------------------------------------- | |||
| * Redistribution and use in source and binary forms, with or without | |||
| * modification, are permitted provided that the following conditions | |||
| * are met: | |||
| * 1. Redistributions of source code must retain the above copyright | |||
| * notice, this list of conditions and the following disclaimer. | |||
| * 2. Redistributions in binary form must reproduce the above copyright | |||
| * notice, this list of conditions and the following disclaimer in the | |||
| * documentation and/or other materials provided with the distribution. | |||
| * 3. The name of the author may not be used to endorse or promote products | |||
| * derived from this software without specific prior written permission. | |||
| * | |||
| * THIS SOFTWARE IS PROVIDED BY THE AUTHOR AND CONTRIBUTORS ``AS IS'' AND | |||
| * ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE | |||
| * IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE | |||
| * ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE | |||
| * FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL | |||
| * DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS | |||
| * OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) | |||
| * HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT | |||
| * LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY | |||
| * OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF | |||
| * SUCH DAMAGE. | |||
| * --------------------------------------------------------------------------- | |||
| */ | |||
| #ifndef _CBFS_SERIALIZED_H_ | |||
| #define _CBFS_SERIALIZED_H_ | |||
| #include <stdint.h> | |||
| #include <compiler.h> | |||
| /** These are standard values for the known compression | |||
| algorithms that coreboot knows about for stages and | |||
| payloads. Of course, other CBFS users can use whatever | |||
| values they want, as long as they understand them. */ | |||
| #define CBFS_COMPRESS_NONE 0 | |||
| #define CBFS_COMPRESS_LZMA 1 | |||
| #define CBFS_COMPRESS_LZ4 2 | |||
| /** These are standard component types for well known | |||
| components (i.e - those that coreboot needs to consume. | |||
| Users are welcome to use any other value for their | |||
| components */ | |||
| #define CBFS_TYPE_DELETED 0x00000000 | |||
| #define CBFS_TYPE_DELETED2 0xffffffff | |||
| #define CBFS_TYPE_STAGE 0x10 | |||
| #define CBFS_TYPE_SELF 0x20 | |||
| #define CBFS_TYPE_FIT 0x21 | |||
| #define CBFS_TYPE_OPTIONROM 0x30 | |||
| #define CBFS_TYPE_BOOTSPLASH 0x40 | |||
| #define CBFS_TYPE_RAW 0x50 | |||
| #define CBFS_TYPE_VSA 0x51 | |||
| #define CBFS_TYPE_MBI 0x52 | |||
| #define CBFS_TYPE_MICROCODE 0x53 | |||
| #define CBFS_TYPE_FSP 0x60 | |||
| #define CBFS_TYPE_MRC 0x61 | |||
| #define CBFS_TYPE_MMA 0x62 | |||
| #define CBFS_TYPE_EFI 0x63 | |||
| #define CBFS_TYPE_STRUCT 0x70 | |||
| #define CBFS_COMPONENT_CMOS_DEFAULT 0xaa | |||
| #define CBFS_TYPE_SPD 0xab | |||
| #define CBFS_TYPE_MRC_CACHE 0xac | |||
| #define CBFS_COMPONENT_CMOS_LAYOUT 0x01aa | |||
| #define CBFS_HEADER_MAGIC 0x4F524243 | |||
| #define CBFS_HEADER_VERSION1 0x31313131 | |||
| #define CBFS_HEADER_VERSION2 0x31313132 | |||
| #define CBFS_HEADER_VERSION CBFS_HEADER_VERSION2 | |||
| /* this is the master cbfs header - it must be located somewhere available | |||
| * to bootblock (to load romstage). The last 4 bytes in the image contain its | |||
| * relative offset from the end of the image (as a 32-bit signed integer). */ | |||
| struct cbfs_header { | |||
| uint32_t magic; | |||
| uint32_t version; | |||
| uint32_t romsize; | |||
| uint32_t bootblocksize; | |||
| uint32_t align; /* fixed to 64 bytes */ | |||
| uint32_t offset; | |||
| uint32_t architecture; | |||
| uint32_t pad[1]; | |||
| } __packed; | |||
| /* this used to be flexible, but wasn't ever set to something different. */ | |||
| #define CBFS_ALIGNMENT 64 | |||
| /* "Unknown" refers to CBFS headers version 1, | |||
| * before the architecture was defined (i.e., x86 only). | |||
| */ | |||
| #define CBFS_ARCHITECTURE_UNKNOWN 0xFFFFFFFF | |||
| #define CBFS_ARCHITECTURE_X86 0x00000001 | |||
| #define CBFS_ARCHITECTURE_ARM 0x00000010 | |||
| /** This is a component header - every entry in the CBFS | |||
| will have this header. | |||
| This is how the component is arranged in the ROM: | |||
| -------------- <- 0 | |||
| component header | |||
| -------------- <- sizeof(struct component) | |||
| component name | |||
| -------------- <- offset | |||
| data | |||
| ... | |||
| -------------- <- offset + len | |||
| */ | |||
| #define CBFS_FILE_MAGIC "LARCHIVE" | |||
| struct cbfs_file { | |||
| char magic[8]; | |||
| uint32_t len; | |||
| uint32_t type; | |||
| uint32_t attributes_offset; | |||
| uint32_t offset; | |||
| } __packed; | |||
| /* The common fields of extended cbfs file attributes. | |||
| Attributes are expected to start with tag/len, then append their | |||
| specific fields. */ | |||
| struct cbfs_file_attribute { | |||
| uint32_t tag; | |||
| /* len covers the whole structure, incl. tag and len */ | |||
| uint32_t len; | |||
| uint8_t data[0]; | |||
| } __packed; | |||
| /* Depending on how the header was initialized, it may be backed with 0x00 or | |||
| * 0xff. Support both. */ | |||
| #define CBFS_FILE_ATTR_TAG_UNUSED 0 | |||
| #define CBFS_FILE_ATTR_TAG_UNUSED2 0xffffffff | |||
| #define CBFS_FILE_ATTR_TAG_COMPRESSION 0x42435a4c | |||
| #define CBFS_FILE_ATTR_TAG_HASH 0x68736148 | |||
| #define CBFS_FILE_ATTR_TAG_POSITION 0x42435350 /* PSCB */ | |||
| #define CBFS_FILE_ATTR_TAG_ALIGNMENT 0x42434c41 /* ALCB */ | |||
| struct cbfs_file_attr_compression { | |||
| uint32_t tag; | |||
| uint32_t len; | |||
| /* whole file compression format. 0 if no compression. */ | |||
| uint32_t compression; | |||
| uint32_t decompressed_size; | |||
| } __packed; | |||
| struct cbfs_file_attr_hash { | |||
| uint32_t tag; | |||
| uint32_t len; | |||
| uint32_t hash_type; | |||
| /* hash_data is len - sizeof(struct) bytes */ | |||
| uint8_t hash_data[]; | |||
| } __packed; | |||
| struct cbfs_file_attr_position { | |||
| uint32_t tag; | |||
| uint32_t len; | |||
| uint32_t position; | |||
| } __packed; | |||
| struct cbfs_file_attr_align { | |||
| uint32_t tag; | |||
| uint32_t len; | |||
| uint32_t alignment; | |||
| } __packed; | |||
| /* | |||
| * ROMCC does not understand uint64_t, so we hide future definitions as they are | |||
| * unlikely to be ever needed from ROMCC | |||
| */ | |||
| #ifndef __ROMCC__ | |||
| /*** Component sub-headers ***/ | |||
| /* Following are component sub-headers for the "standard" | |||
| component types */ | |||
| /** This is the sub-header for stage components. Stages are | |||
| loaded by coreboot during the normal boot process */ | |||
| struct cbfs_stage { | |||
| uint32_t compression; /** Compression type */ | |||
| uint64_t entry; /** entry point */ | |||
| uint64_t load; /** Where to load in memory */ | |||
| uint32_t len; /** length of data to load */ | |||
| uint32_t memlen; /** total length of object in memory */ | |||
| } __packed; | |||
| /** this is the sub-header for payload components. Payloads | |||
| are loaded by coreboot at the end of the boot process */ | |||
| struct cbfs_payload_segment { | |||
| uint32_t type; | |||
| uint32_t compression; | |||
| uint32_t offset; | |||
| uint64_t load_addr; | |||
| uint32_t len; | |||
| uint32_t mem_len; | |||
| } __packed; | |||
| struct cbfs_payload { | |||
| struct cbfs_payload_segment segments; | |||
| }; | |||
| #define PAYLOAD_SEGMENT_CODE 0x434F4445 | |||
| #define PAYLOAD_SEGMENT_DATA 0x44415441 | |||
| #define PAYLOAD_SEGMENT_BSS 0x42535320 | |||
| #define PAYLOAD_SEGMENT_PARAMS 0x50415241 | |||
| #define PAYLOAD_SEGMENT_ENTRY 0x454E5452 | |||
| struct cbfs_optionrom { | |||
| uint32_t compression; | |||
| uint32_t len; | |||
| } __packed; | |||
| #endif /* __ROMCC__ */ | |||
| #endif /* _CBFS_SERIALIZED_H_ */ | |||
+ 135
- 0
t430/util/commonlib/include/commonlib/cbmem_id.h
View File
| @ -0,0 +1,135 @@ | |||
| /* | |||
| * This file is part of the coreboot project. | |||
| * | |||
| * Copyright (C) 2009 coresystems GmbH | |||
| * Copyright (C) 2013 Google, Inc. | |||
| * | |||
| * This program is free software; you can redistribute it and/or modify | |||
| * it under the terms of the GNU General Public License as published by | |||
| * the Free Software Foundation; version 2 of the License. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| */ | |||
| #ifndef _CBMEM_ID_H_ | |||
| #define _CBMEM_ID_H_ | |||
| #define CBMEM_ID_ACPI 0x41435049 | |||
| #define CBMEM_ID_ACPI_GNVS 0x474e5653 | |||
| #define CBMEM_ID_ACPI_GNVS_PTR 0x474e5650 | |||
| #define CBMEM_ID_AFTER_CAR 0xc4787a93 | |||
| #define CBMEM_ID_AGESA_RUNTIME 0x41474553 | |||
| #define CBMEM_ID_AMDMCT_MEMINFO 0x494D454E | |||
| #define CBMEM_ID_CAR_GLOBALS 0xcac4e6a3 | |||
| #define CBMEM_ID_CBTABLE 0x43425442 | |||
| #define CBMEM_ID_CBTABLE_FWD 0x43425443 | |||
| #define CBMEM_ID_CONSOLE 0x434f4e53 | |||
| #define CBMEM_ID_COVERAGE 0x47434f56 | |||
| #define CBMEM_ID_EHCI_DEBUG 0xe4c1deb9 | |||
| #define CBMEM_ID_ELOG 0x454c4f47 | |||
| #define CBMEM_ID_FREESPACE 0x46524545 | |||
| #define CBMEM_ID_FSP_RESERVED_MEMORY 0x46535052 | |||
| #define CBMEM_ID_FSP_RUNTIME 0x52505346 | |||
| #define CBMEM_ID_GDT 0x4c474454 | |||
| #define CBMEM_ID_HOB_POINTER 0x484f4221 | |||
| #define CBMEM_ID_IGD_OPREGION 0x4f444749 | |||
| #define CBMEM_ID_IMD_ROOT 0xff4017ff | |||
| #define CBMEM_ID_IMD_SMALL 0x53a11439 | |||
| #define CBMEM_ID_MEMINFO 0x494D454D | |||
| #define CBMEM_ID_MMA_DATA 0x4D4D4144 | |||
| #define CBMEM_ID_MPTABLE 0x534d5054 | |||
| #define CBMEM_ID_MRCDATA 0x4d524344 | |||
| #define CBMEM_ID_VAR_MRCDATA 0x4d524345 | |||
| #define CBMEM_ID_MTC 0xcb31d31c | |||
| #define CBMEM_ID_NONE 0x00000000 | |||
| #define CBMEM_ID_PIRQ 0x49525154 | |||
| #define CBMEM_ID_POWER_STATE 0x50535454 | |||
| #define CBMEM_ID_RAM_OOPS 0x05430095 | |||
| #define CBMEM_ID_RAMSTAGE 0x9a357a9e | |||
| #define CBMEM_ID_RAMSTAGE_CACHE 0x9a3ca54e | |||
| #define CBMEM_ID_REFCODE 0x04efc0de | |||
| #define CBMEM_ID_REFCODE_CACHE 0x4efc0de5 | |||
| #define CBMEM_ID_RESUME 0x5245534d | |||
| #define CBMEM_ID_RESUME_SCRATCH 0x52455343 | |||
| #define CBMEM_ID_ROMSTAGE_INFO 0x47545352 | |||
| #define CBMEM_ID_ROMSTAGE_RAM_STACK 0x90357ac4 | |||
| #define CBMEM_ID_ROOT 0xff4007ff | |||
| #define CBMEM_ID_SMBIOS 0x534d4254 | |||
| #define CBMEM_ID_SMM_SAVE_SPACE 0x07e9acee | |||
| #define CBMEM_ID_STAGEx_META 0x57a9e000 | |||
| #define CBMEM_ID_STAGEx_CACHE 0x57a9e100 | |||
| #define CBMEM_ID_STAGEx_RAW 0x57a9e200 | |||
| #define CBMEM_ID_STORAGE_DATA 0x53746f72 | |||
| #define CBMEM_ID_TCPA_LOG 0x54435041 | |||
| #define CBMEM_ID_TIMESTAMP 0x54494d45 | |||
| #define CBMEM_ID_VBOOT_HANDOFF 0x780074f0 | |||
| #define CBMEM_ID_VBOOT_SEL_REG 0x780074f1 | |||
| #define CBMEM_ID_VBOOT_WORKBUF 0x78007343 | |||
| #define CBMEM_ID_VPD 0x56504420 | |||
| #define CBMEM_ID_WIFI_CALIBRATION 0x57494649 | |||
| #define CBMEM_ID_EC_HOSTEVENT 0x63ccbbc3 | |||
| #define CBMEM_ID_EXT_VBT 0x69866684 | |||
| #define CBMEM_ID_ROM0 0x524f4d30 | |||
| #define CBMEM_ID_ROM1 0x524f4d31 | |||
| #define CBMEM_ID_ROM2 0x524f4d32 | |||
| #define CBMEM_ID_ROM3 0x524f4d33 | |||
| #define CBMEM_ID_TO_NAME_TABLE \ | |||
| { CBMEM_ID_ACPI, "ACPI " }, \ | |||
| { CBMEM_ID_ACPI_GNVS, "ACPI GNVS " }, \ | |||
| { CBMEM_ID_ACPI_GNVS_PTR, "GNVS PTR " }, \ | |||
| { CBMEM_ID_AGESA_RUNTIME, "AGESA RSVD " }, \ | |||
| { CBMEM_ID_AFTER_CAR, "AFTER CAR " }, \ | |||
| { CBMEM_ID_AMDMCT_MEMINFO, "AMDMEM INFO" }, \ | |||
| { CBMEM_ID_CAR_GLOBALS, "CAR GLOBALS" }, \ | |||
| { CBMEM_ID_CBTABLE, "COREBOOT " }, \ | |||
| { CBMEM_ID_CBTABLE_FWD, "COREBOOTFWD" }, \ | |||
| { CBMEM_ID_CONSOLE, "CONSOLE " }, \ | |||
| { CBMEM_ID_COVERAGE, "COVERAGE " }, \ | |||
| { CBMEM_ID_EHCI_DEBUG, "USBDEBUG " }, \ | |||
| { CBMEM_ID_ELOG, "ELOG " }, \ | |||
| { CBMEM_ID_FREESPACE, "FREE SPACE " }, \ | |||
| { CBMEM_ID_FSP_RESERVED_MEMORY, "FSP MEMORY " }, \ | |||
| { CBMEM_ID_FSP_RUNTIME, "FSP RUNTIME" }, \ | |||
| { CBMEM_ID_GDT, "GDT " }, \ | |||
| { CBMEM_ID_HOB_POINTER, "HOB " }, \ | |||
| { CBMEM_ID_IMD_ROOT, "IMD ROOT " }, \ | |||
| { CBMEM_ID_IMD_SMALL, "IMD SMALL " }, \ | |||
| { CBMEM_ID_MEMINFO, "MEM INFO " }, \ | |||
| { CBMEM_ID_MMA_DATA, "MMA DATA " }, \ | |||
| { CBMEM_ID_MPTABLE, "SMP TABLE " }, \ | |||
| { CBMEM_ID_MRCDATA, "MRC DATA " }, \ | |||
| { CBMEM_ID_VAR_MRCDATA, "VARMRC DATA" }, \ | |||
| { CBMEM_ID_MTC, "MTC " }, \ | |||
| { CBMEM_ID_PIRQ, "IRQ TABLE " }, \ | |||
| { CBMEM_ID_POWER_STATE, "POWER STATE" }, \ | |||
| { CBMEM_ID_RAM_OOPS, "RAMOOPS " }, \ | |||
| { CBMEM_ID_RAMSTAGE_CACHE, "RAMSTAGE $ " }, \ | |||
| { CBMEM_ID_RAMSTAGE, "RAMSTAGE " }, \ | |||
| { CBMEM_ID_REFCODE_CACHE, "REFCODE $ " }, \ | |||
| { CBMEM_ID_REFCODE, "REFCODE " }, \ | |||
| { CBMEM_ID_RESUME, "ACPI RESUME" }, \ | |||
| { CBMEM_ID_RESUME_SCRATCH, "ACPISCRATCH" }, \ | |||
| { CBMEM_ID_ROMSTAGE_INFO, "ROMSTAGE " }, \ | |||
| { CBMEM_ID_ROMSTAGE_RAM_STACK, "ROMSTG STCK" }, \ | |||
| { CBMEM_ID_ROOT, "CBMEM ROOT " }, \ | |||
| { CBMEM_ID_SMBIOS, "SMBIOS " }, \ | |||
| { CBMEM_ID_SMM_SAVE_SPACE, "SMM BACKUP " }, \ | |||
| { CBMEM_ID_STORAGE_DATA, "SD/MMC/eMMC" }, \ | |||
| { CBMEM_ID_TCPA_LOG, "TCPA LOG " }, \ | |||
| { CBMEM_ID_TIMESTAMP, "TIME STAMP " }, \ | |||
| { CBMEM_ID_VBOOT_HANDOFF, "VBOOT " }, \ | |||
| { CBMEM_ID_VBOOT_SEL_REG, "VBOOT SEL " }, \ | |||
| { CBMEM_ID_VBOOT_WORKBUF, "VBOOT WORK " }, \ | |||
| { CBMEM_ID_VPD, "VPD " }, \ | |||
| { CBMEM_ID_WIFI_CALIBRATION, "WIFI CLBR " }, \ | |||
| { CBMEM_ID_EC_HOSTEVENT, "EC HOSTEVENT"}, \ | |||
| { CBMEM_ID_EXT_VBT, "EXT VBT"}, \ | |||
| { CBMEM_ID_ROM0, "VGA ROM #0 "}, \ | |||
| { CBMEM_ID_ROM1, "VGA ROM #1 "}, \ | |||
| { CBMEM_ID_ROM2, "VGA ROM #2 "}, \ | |||
| { CBMEM_ID_ROM3, "VGA ROM #3 "}, | |||
| #endif /* _CBMEM_ID_H_ */ | |||
+ 34
- 0
t430/util/commonlib/include/commonlib/compression.h
View File
| @ -0,0 +1,34 @@ | |||
| /* | |||
| * This file is part of the coreboot project. | |||
| * | |||
| * Copyright 2016 Google Inc. | |||
| * | |||
| * This program is free software; you can redistribute it and/or modify | |||
| * it under the terms of the GNU General Public License as published by | |||
| * the Free Software Foundation; version 2 of the License. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| */ | |||
| #ifndef _COMMONLIB_COMPRESSION_H_ | |||
| #define _COMMONLIB_COMPRESSION_H_ | |||
| #include <stddef.h> | |||
| /* Decompresses an LZ4F image (multiple LZ4 blocks with frame header) from src | |||
| * to dst, ensuring that it doesn't read more than srcn bytes and doesn't write | |||
| * more than dstn. Buffer sizes must stay below 2GB. Can decompress files loaded | |||
| * to the end of a buffer in-place, as long as buffer is larger than the final | |||
| * output size. (Usually just a few bytes, but may be up to (8 + dstn/255) in | |||
| * worst case. Will reliably return an error if buffer was too small.) | |||
| * Returns amount of decompressed bytes, or 0 on error. | |||
| */ | |||
| size_t ulz4fn(const void *src, size_t srcn, void *dst, size_t dstn); | |||
| /* Same as ulz4fn() but does not perform any bounds checks. */ | |||
| size_t ulz4f(const void *src, void *dst); | |||
| #endif /* _COMMONLIB_COMPRESSION_H_ */ | |||
+ 470
- 0
t430/util/commonlib/include/commonlib/coreboot_tables.h
View File
| @ -0,0 +1,470 @@ | |||
| /* | |||
| * This file is part of the coreboot project. | |||
| * | |||
| * This program is free software; you can redistribute it and/or modify | |||
| * it under the terms of the GNU General Public License as published by | |||
| * the Free Software Foundation; version 2 of the License. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| */ | |||
| #ifndef COMMONLIB_COREBOOT_TABLES_H | |||
| #define COMMONLIB_COREBOOT_TABLES_H | |||
| #include <stdint.h> | |||
| /* The coreboot table information is for conveying information | |||
| * from the firmware to the loaded OS image. Primarily this | |||
| * is expected to be information that cannot be discovered by | |||
| * other means, such as querying the hardware directly. | |||
| * | |||
| * All of the information should be Position Independent Data. | |||
| * That is it should be safe to relocated any of the information | |||
| * without it's meaning/correctness changing. For table that | |||
| * can reasonably be used on multiple architectures the data | |||
| * size should be fixed. This should ease the transition between | |||
| * 32 bit and 64 bit architectures etc. | |||
| * | |||
| * The completeness test for the information in this table is: | |||
| * - Can all of the hardware be detected? | |||
| * - Are the per motherboard constants available? | |||
| * - Is there enough to allow a kernel to run that was written before | |||
| * a particular motherboard is constructed? (Assuming the kernel | |||
| * has drivers for all of the hardware but it does not have | |||
| * assumptions on how the hardware is connected together). | |||
| * | |||
| * With this test it should be straight forward to determine if a | |||
| * table entry is required or not. This should remove much of the | |||
| * long term compatibility burden as table entries which are | |||
| * irrelevant or have been replaced by better alternatives may be | |||
| * dropped. Of course it is polite and expedite to include extra | |||
| * table entries and be backwards compatible, but it is not required. | |||
| */ | |||
| /* Since coreboot is usually compiled 32bit, gcc will align 64bit | |||
| * types to 32bit boundaries. If the coreboot table is dumped on a | |||
| * 64bit system, a uint64_t would be aligned to 64bit boundaries, | |||
| * breaking the table format. | |||
| * | |||
| * lb_uint64 will keep 64bit coreboot table values aligned to 32bit | |||
| * to ensure compatibility. They can be accessed with the two functions | |||
| * below: unpack_lb64() and pack_lb64() | |||
| * | |||
| * See also: util/lbtdump/lbtdump.c | |||
| */ | |||
| struct lb_uint64 { | |||
| uint32_t lo; | |||
| uint32_t hi; | |||
| }; | |||
| static inline uint64_t unpack_lb64(struct lb_uint64 value) | |||
| { | |||
| uint64_t result; | |||
| result = value.hi; | |||
| result = (result << 32) + value.lo; | |||
| return result; | |||
| } | |||
| static inline struct lb_uint64 pack_lb64(uint64_t value) | |||
| { | |||
| struct lb_uint64 result; | |||
| result.lo = (value >> 0) & 0xffffffff; | |||
| result.hi = (value >> 32) & 0xffffffff; | |||
| return result; | |||
| } | |||
| struct lb_header { | |||
| uint8_t signature[4]; /* LBIO */ | |||
| uint32_t header_bytes; | |||
| uint32_t header_checksum; | |||
| uint32_t table_bytes; | |||
| uint32_t table_checksum; | |||
| uint32_t table_entries; | |||
| }; | |||
| /* Every entry in the boot environment list will correspond to a boot | |||
| * info record. Encoding both type and size. The type is obviously | |||
| * so you can tell what it is. The size allows you to skip that | |||
| * boot environment record if you don't know what it is. This allows | |||
| * forward compatibility with records not yet defined. | |||
| */ | |||
| struct lb_record { | |||
| uint32_t tag; /* tag ID */ | |||
| uint32_t size; /* size of record (in bytes) */ | |||
| }; | |||
| #define LB_TAG_UNUSED 0x0000 | |||
| #define LB_TAG_MEMORY 0x0001 | |||
| struct lb_memory_range { | |||
| struct lb_uint64 start; | |||
| struct lb_uint64 size; | |||
| uint32_t type; | |||
| #define LB_MEM_RAM 1 /* Memory anyone can use */ | |||
| #define LB_MEM_RESERVED 2 /* Don't use this memory region */ | |||
| #define LB_MEM_ACPI 3 /* ACPI Tables */ | |||
| #define LB_MEM_NVS 4 /* ACPI NVS Memory */ | |||
| #define LB_MEM_UNUSABLE 5 /* Unusable address space */ | |||
| #define LB_MEM_VENDOR_RSVD 6 /* Vendor Reserved */ | |||
| #define LB_MEM_TABLE 16 /* Ram configuration tables are kept in */ | |||
| }; | |||
| struct lb_memory { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| struct lb_memory_range map[0]; | |||
| }; | |||
| #define LB_TAG_HWRPB 0x0002 | |||
| struct lb_hwrpb { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| uint64_t hwrpb; | |||
| }; | |||
| #define LB_TAG_MAINBOARD 0x0003 | |||
| struct lb_mainboard { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| uint8_t vendor_idx; | |||
| uint8_t part_number_idx; | |||
| uint8_t strings[0]; | |||
| }; | |||
| #define LB_TAG_VERSION 0x0004 | |||
| #define LB_TAG_EXTRA_VERSION 0x0005 | |||
| #define LB_TAG_BUILD 0x0006 | |||
| #define LB_TAG_COMPILE_TIME 0x0007 | |||
| #define LB_TAG_COMPILE_BY 0x0008 | |||
| #define LB_TAG_COMPILE_HOST 0x0009 | |||
| #define LB_TAG_COMPILE_DOMAIN 0x000a | |||
| #define LB_TAG_COMPILER 0x000b | |||
| #define LB_TAG_LINKER 0x000c | |||
| #define LB_TAG_ASSEMBLER 0x000d | |||
| struct lb_string { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| uint8_t string[0]; | |||
| }; | |||
| #define LB_TAG_VERSION_TIMESTAMP 0x0026 | |||
| struct lb_timestamp { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| uint32_t timestamp; | |||
| }; | |||
| /* 0xe is taken by v3 */ | |||
| #define LB_TAG_SERIAL 0x000f | |||
| struct lb_serial { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| #define LB_SERIAL_TYPE_IO_MAPPED 1 | |||
| #define LB_SERIAL_TYPE_MEMORY_MAPPED 2 | |||
| uint32_t type; | |||
| uint32_t baseaddr; | |||
| uint32_t baud; | |||
| uint32_t regwidth; | |||
| /* Crystal or input frequency to the chip containing the UART. | |||
| * Provide the board specific details to allow the payload to | |||
| * initialize the chip containing the UART and make independent | |||
| * decisions as to which dividers to select and their values | |||
| * to eventually arrive at the desired console baud-rate. */ | |||
| uint32_t input_hertz; | |||
| /* UART PCI address: bus, device, function | |||
| * 1 << 31 - Valid bit, PCI UART in use | |||
| * Bus << 20 | |||
| * Device << 15 | |||
| * Function << 12 | |||
| */ | |||
| uint32_t uart_pci_addr; | |||
| }; | |||
| #define LB_TAG_CONSOLE 0x0010 | |||
| struct lb_console { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| uint16_t type; | |||
| }; | |||
| #define LB_TAG_CONSOLE_SERIAL8250 0 | |||
| #define LB_TAG_CONSOLE_VGA 1 // OBSOLETE | |||
| #define LB_TAG_CONSOLE_BTEXT 2 // OBSOLETE | |||
| #define LB_TAG_CONSOLE_LOGBUF 3 // OBSOLETE | |||
| #define LB_TAG_CONSOLE_SROM 4 // OBSOLETE | |||
| #define LB_TAG_CONSOLE_EHCI 5 | |||
| #define LB_TAG_CONSOLE_SERIAL8250MEM 6 | |||
| #define LB_TAG_FORWARD 0x0011 | |||
| struct lb_forward { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| uint64_t forward; | |||
| }; | |||
| /** | |||
| * coreboot framebuffer | |||
| * | |||
| * The coreboot framebuffer uses a very common format usually referred | |||
| * to as "linear framebuffer": | |||
| * | |||
| * The first pixel of the framebuffer is the upper left corner, its | |||
| * address is given by `physical_address`. | |||
| * | |||
| * Each pixel is represented by exactly `bits_per_pixel` bits. If a | |||
| * pixel (or a color component therein) doesn't fill a whole byte or | |||
| * doesn't start on a byte boundary, it starts at the least signifi- | |||
| * cant bit not occupied by the previous pixel (or color component). | |||
| * Pixels (or color components) that span multiple bytes always start | |||
| * in the byte with the lowest address. | |||
| * | |||
| * The framebuffer provides a visible rectangle of `x_resolution` * | |||
| * `y_resolution` pixels. However, the lines always start at a byte | |||
| * boundary given by `bytes_per_line`, which may leave a gap after | |||
| * each line of pixels. Thus, the data for a pixel with the coordi- | |||
| * nates (x, y) from the upper left corner always starts at | |||
| * | |||
| * physical_address + y * bytes_per_line + x * bits_per_pixel / 8 | |||
| * | |||
| * `bytes_per_line` is always big enough to hold `x_resolution` | |||
| * pixels. It can, however, be arbitrarily higher (e.g. to fulfill | |||
| * hardware constraints or for optimization purposes). The size of | |||
| * the framebuffer is always `y_resolution * bytes_per_line`. | |||
| * | |||
| * The coreboot framebuffer only supports RGB color formats. The | |||
| * position and size of each color component are specified indivi- | |||
| * dually by <color>_mask_pos and <color>_mask_size. To allow byte | |||
| * or word aligned pixels, a fourth (padding) component may be | |||
| * specified by `reserved_mask_pos` and `reserved_mask_size`. | |||
| * | |||
| * Software utilizing the coreboot framebuffer shall consider all | |||
| * fields described above. It may, however, only implement a subset | |||
| * of the possible color formats. | |||
| */ | |||
| #define LB_TAG_FRAMEBUFFER 0x0012 | |||
| struct lb_framebuffer { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| uint64_t physical_address; | |||
| uint32_t x_resolution; | |||
| uint32_t y_resolution; | |||
| uint32_t bytes_per_line; | |||
| uint8_t bits_per_pixel; | |||
| uint8_t red_mask_pos; | |||
| uint8_t red_mask_size; | |||
| uint8_t green_mask_pos; | |||
| uint8_t green_mask_size; | |||
| uint8_t blue_mask_pos; | |||
| uint8_t blue_mask_size; | |||
| uint8_t reserved_mask_pos; | |||
| uint8_t reserved_mask_size; | |||
| }; | |||
| #define LB_TAG_GPIO 0x0013 | |||
| struct lb_gpio { | |||
| uint32_t port; | |||
| uint32_t polarity; | |||
| #define ACTIVE_LOW 0 | |||
| #define ACTIVE_HIGH 1 | |||
| uint32_t value; | |||
| #define GPIO_MAX_NAME_LENGTH 16 | |||
| uint8_t name[GPIO_MAX_NAME_LENGTH]; | |||
| }; | |||
| struct lb_gpios { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| uint32_t count; | |||
| struct lb_gpio gpios[0]; | |||
| }; | |||
| #define LB_TAG_VDAT 0x0015 | |||
| #define LB_TAG_VBNV 0x0019 | |||
| #define LB_TAB_VBOOT_HANDOFF 0x0020 | |||
| #define LB_TAB_DMA 0x0022 | |||
| #define LB_TAG_RAM_OOPS 0x0023 | |||
| #define LB_TAG_MTC 0x002b | |||
| struct lb_range { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| uint64_t range_start; | |||
| uint32_t range_size; | |||
| }; | |||
| void lb_ramoops(struct lb_header *header); | |||
| #define LB_TAG_TIMESTAMPS 0x0016 | |||
| #define LB_TAG_CBMEM_CONSOLE 0x0017 | |||
| #define LB_TAG_MRC_CACHE 0x0018 | |||
| #define LB_TAG_ACPI_GNVS 0x0024 | |||
| #define LB_TAG_WIFI_CALIBRATION 0x0027 | |||
| #define LB_TAG_VPD 0x002c | |||
| struct lb_cbmem_ref { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| uint64_t cbmem_addr; | |||
| }; | |||
| #define LB_TAG_X86_ROM_MTRR 0x0021 | |||
| struct lb_x86_rom_mtrr { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| /* The variable range MTRR index covering the ROM. */ | |||
| uint32_t index; | |||
| }; | |||
| #define LB_TAG_BOARD_ID 0x0025 | |||
| #define LB_TAG_RAM_CODE 0x0028 | |||
| #define LB_TAG_SKU_ID 0x002d | |||
| struct lb_strapping_id { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| uint32_t id_code; | |||
| }; | |||
| #define LB_TAG_SPI_FLASH 0x0029 | |||
| struct lb_spi_flash { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| uint32_t flash_size; | |||
| uint32_t sector_size; | |||
| uint32_t erase_cmd; | |||
| }; | |||
| #define LB_TAG_BOOT_MEDIA_PARAMS 0x0030 | |||
| struct lb_boot_media_params { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| /* offsets are relative to start of boot media */ | |||
| uint64_t fmap_offset; | |||
| uint64_t cbfs_offset; | |||
| uint64_t cbfs_size; | |||
| uint64_t boot_media_size; | |||
| }; | |||
| /* | |||
| * There can be more than one of these records as there is one per cbmem entry. | |||
| */ | |||
| #define LB_TAG_CBMEM_ENTRY 0x0031 | |||
| struct lb_cbmem_entry { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| uint64_t address; | |||
| uint32_t entry_size; | |||
| uint32_t id; | |||
| }; | |||
| #define LB_TAG_TSC_INFO 0x0032 | |||
| struct lb_tsc_info { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| uint32_t freq_khz; | |||
| }; | |||
| #define LB_TAG_MAC_ADDRS 0x0033 | |||
| struct mac_address { | |||
| uint8_t mac_addr[6]; | |||
| uint8_t pad[2]; /* Pad it to 8 bytes to keep it simple. */ | |||
| }; | |||
| struct lb_macs { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| uint32_t count; | |||
| struct mac_address mac_addrs[0]; | |||
| }; | |||
| #define LB_TAG_SERIALNO 0x002a | |||
| #define MAX_SERIALNO_LENGTH 32 | |||
| /* The following structures are for the cmos definitions table */ | |||
| #define LB_TAG_CMOS_OPTION_TABLE 200 | |||
| /* cmos header record */ | |||
| struct cmos_option_table { | |||
| uint32_t tag; /* CMOS definitions table type */ | |||
| uint32_t size; /* size of the entire table */ | |||
| uint32_t header_length; /* length of header */ | |||
| }; | |||
| /* cmos entry record | |||
| * This record is variable length. The name field may be | |||
| * shorter than CMOS_MAX_NAME_LENGTH. The entry may start | |||
| * anywhere in the byte, but can not span bytes unless it | |||
| * starts at the beginning of the byte and the length is | |||
| * fills complete bytes. | |||
| */ | |||
| #define LB_TAG_OPTION 201 | |||
| struct cmos_entries { | |||
| uint32_t tag; /* entry type */ | |||
| uint32_t size; /* length of this record */ | |||
| uint32_t bit; /* starting bit from start of image */ | |||
| uint32_t length; /* length of field in bits */ | |||
| uint32_t config; /* e=enumeration, h=hex, r=reserved */ | |||
| uint32_t config_id; /* a number linking to an enumeration record */ | |||
| #define CMOS_MAX_NAME_LENGTH 32 | |||
| uint8_t name[CMOS_MAX_NAME_LENGTH]; /* name of entry in ascii, | |||
| variable length int aligned */ | |||
| }; | |||
| /* cmos enumerations record | |||
| * This record is variable length. The text field may be | |||
| * shorter than CMOS_MAX_TEXT_LENGTH. | |||
| */ | |||
| #define LB_TAG_OPTION_ENUM 202 | |||
| struct cmos_enums { | |||
| uint32_t tag; /* enumeration type */ | |||
| uint32_t size; /* length of this record */ | |||
| uint32_t config_id; /* a number identifying the config id */ | |||
| uint32_t value; /* the value associated with the text */ | |||
| #define CMOS_MAX_TEXT_LENGTH 32 | |||
| uint8_t text[CMOS_MAX_TEXT_LENGTH]; /* enum description in ascii, | |||
| variable length int aligned */ | |||
| }; | |||
| /* cmos defaults record | |||
| * This record contains default settings for the cmos ram. | |||
| */ | |||
| #define LB_TAG_OPTION_DEFAULTS 203 | |||
| struct cmos_defaults { | |||
| uint32_t tag; /* default type */ | |||
| uint32_t size; /* length of this record */ | |||
| uint32_t name_length; /* length of the following name field */ | |||
| uint8_t name[CMOS_MAX_NAME_LENGTH]; /* name identifying the default */ | |||
| #define CMOS_IMAGE_BUFFER_SIZE 256 | |||
| uint8_t default_set[CMOS_IMAGE_BUFFER_SIZE]; /* default settings */ | |||
| }; | |||
| #define LB_TAG_OPTION_CHECKSUM 204 | |||
| struct cmos_checksum { | |||
| uint32_t tag; | |||
| uint32_t size; | |||
| /* In practice everything is byte aligned, but things are measured | |||
| * in bits to be consistent. | |||
| */ | |||
| uint32_t range_start; /* First bit that is checksummed (byte aligned) */ | |||
| uint32_t range_end; /* Last bit that is checksummed (byte aligned) */ | |||
| uint32_t location; /* First bit of the checksum (byte aligned) */ | |||
| uint32_t type; /* Checksum algorithm that is used */ | |||
| #define CHECKSUM_NONE 0 | |||
| #define CHECKSUM_PCBIOS 1 | |||
| }; | |||
| #endif | |||
+ 263
- 0
t430/util/commonlib/include/commonlib/endian.h
View File
| @ -0,0 +1,263 @@ | |||
| /* | |||
| * This file is part of the coreboot project. | |||
| * | |||
| * Copyright 2015 Google Inc. | |||
| * | |||
| * This program is free software; you can redistribute it and/or modify | |||
| * it under the terms of the GNU General Public License as published by | |||
| * the Free Software Foundation; version 2 of the License. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| */ | |||
| #ifndef _COMMONLIB_ENDIAN_H_ | |||
| #define _COMMONLIB_ENDIAN_H_ | |||
| #include <stddef.h> | |||
| #include <stdint.h> | |||
| #include <string.h> | |||
| /* Endian agnostic functions working on single byte. */ | |||
| static inline uint8_t read_ble8(const void *src) | |||
| { | |||
| const uint8_t *s = src; | |||
| return *s; | |||
| } | |||
| static inline uint8_t read_at_ble8(const void *src, size_t offset) | |||
| { | |||
| const uint8_t *s = src; | |||
| s += offset; | |||
| return read_ble8(s); | |||
| } | |||
| static inline void write_ble8(void *dest, uint8_t val) | |||
| { | |||
| *(uint8_t *)dest = val; | |||
| } | |||
| static inline void write_at_ble8(void *dest, uint8_t val, size_t offset) | |||
| { | |||
| uint8_t *d = dest; | |||
| d += offset; | |||
| write_ble8(d, val); | |||
| } | |||
| /* Big Endian functions. */ | |||
| static inline uint8_t read_be8(const void *src) | |||
| { | |||
| return read_ble8(src); | |||
| } | |||
| static inline uint8_t read_at_be8(const void *src, size_t offset) | |||
| { | |||
| return read_at_ble8(src, offset); | |||
| } | |||
| static inline void write_be8(void *dest, uint8_t val) | |||
| { | |||
| write_ble8(dest, val); | |||
| } | |||
| static inline void write_at_be8(void *dest, uint8_t val, size_t offset) | |||
| { | |||
| write_at_ble8(dest, val, offset); | |||
| } | |||
| static inline uint16_t read_be16(const void *src) | |||
| { | |||
| const uint8_t *s = src; | |||
| return (((uint16_t)s[0]) << 8) | (((uint16_t)s[1]) << 0); | |||
| } | |||
| static inline uint16_t read_at_be16(const void *src, size_t offset) | |||
| { | |||
| const uint8_t *s = src; | |||
| s += offset; | |||
| return read_be16(s); | |||
| } | |||
| static inline void write_be16(void *dest, uint16_t val) | |||
| { | |||
| write_be8(dest, val >> 8); | |||
| write_at_be8(dest, val >> 0, sizeof(uint8_t)); | |||
| } | |||
| static inline void write_at_be16(void *dest, uint16_t val, size_t offset) | |||
| { | |||
| uint8_t *d = dest; | |||
| d += offset; | |||
| write_be16(d, val); | |||
| } | |||
| static inline uint32_t read_be32(const void *src) | |||
| { | |||
| const uint8_t *s = src; | |||
| return (((uint32_t)s[0]) << 24) | (((uint32_t)s[1]) << 16) | | |||
| (((uint32_t)s[2]) << 8) | (((uint32_t)s[3]) << 0); | |||
| } | |||
| static inline uint32_t read_at_be32(const void *src, size_t offset) | |||
| { | |||
| const uint8_t *s = src; | |||
| s += offset; | |||
| return read_be32(s); | |||
| } | |||
| static inline void write_be32(void *dest, uint32_t val) | |||
| { | |||
| write_be16(dest, val >> 16); | |||
| write_at_be16(dest, val >> 0, sizeof(uint16_t)); | |||
| } | |||
| static inline void write_at_be32(void *dest, uint32_t val, size_t offset) | |||
| { | |||
| uint8_t *d = dest; | |||
| d += offset; | |||
| write_be32(d, val); | |||
| } | |||
| static inline uint64_t read_be64(const void *src) | |||
| { | |||
| uint64_t val; | |||
| val = read_be32(src); | |||
| val <<= 32; | |||
| val |= read_at_be32(src, sizeof(uint32_t)); | |||
| return val; | |||
| } | |||
| static inline uint64_t read_at_be64(const void *src, size_t offset) | |||
| { | |||
| const uint8_t *s = src; | |||
| s += offset; | |||
| return read_be64(s); | |||
| } | |||
| static inline void write_be64(void *dest, uint64_t val) | |||
| { | |||
| write_be32(dest, val >> 32); | |||
| write_at_be32(dest, val >> 0, sizeof(uint32_t)); | |||
| } | |||
| static inline void write_at_be64(void *dest, uint64_t val, size_t offset) | |||
| { | |||
| uint8_t *d = dest; | |||
| d += offset; | |||
| write_be64(d, val); | |||
| } | |||
| /* Little Endian functions. */ | |||
| static inline uint8_t read_le8(const void *src) | |||
| { | |||
| return read_ble8(src); | |||
| } | |||
| static inline uint8_t read_at_le8(const void *src, size_t offset) | |||
| { | |||
| return read_at_ble8(src, offset); | |||
| } | |||
| static inline void write_le8(void *dest, uint8_t val) | |||
| { | |||
| write_ble8(dest, val); | |||
| } | |||
| static inline void write_at_le8(void *dest, uint8_t val, size_t offset) | |||
| { | |||
| write_at_ble8(dest, val, offset); | |||
| } | |||
| static inline uint16_t read_le16(const void *src) | |||
| { | |||
| const uint8_t *s = src; | |||
| return (((uint16_t)s[1]) << 8) | (((uint16_t)s[0]) << 0); | |||
| } | |||
| static inline uint16_t read_at_le16(const void *src, size_t offset) | |||
| { | |||
| const uint8_t *s = src; | |||
| s += offset; | |||
| return read_le16(s); | |||
| } | |||
| static inline void write_le16(void *dest, uint16_t val) | |||
| { | |||
| write_le8(dest, val >> 0); | |||
| write_at_le8(dest, val >> 8, sizeof(uint8_t)); | |||
| } | |||
| static inline void write_at_le16(void *dest, uint16_t val, size_t offset) | |||
| { | |||
| uint8_t *d = dest; | |||
| d += offset; | |||
| write_le16(d, val); | |||
| } | |||
| static inline uint32_t read_le32(const void *src) | |||
| { | |||
| const uint8_t *s = src; | |||
| return (((uint32_t)s[3]) << 24) | (((uint32_t)s[2]) << 16) | | |||
| (((uint32_t)s[1]) << 8) | (((uint32_t)s[0]) << 0); | |||
| } | |||
| static inline uint32_t read_at_le32(const void *src, size_t offset) | |||
| { | |||
| const uint8_t *s = src; | |||
| s += offset; | |||
| return read_le32(s); | |||
| } | |||
| static inline void write_le32(void *dest, uint32_t val) | |||
| { | |||
| write_le16(dest, val >> 0); | |||
| write_at_le16(dest, val >> 16, sizeof(uint16_t)); | |||
| } | |||
| static inline void write_at_le32(void *dest, uint32_t val, size_t offset) | |||
| { | |||
| uint8_t *d = dest; | |||
| d += offset; | |||
| write_le32(d, val); | |||
| } | |||
| static inline uint64_t read_le64(const void *src) | |||
| { | |||
| uint64_t val; | |||
| val = read_at_le32(src, sizeof(uint32_t)); | |||
| val <<= 32; | |||
| val |= read_le32(src); | |||
| return val; | |||
| } | |||
| static inline uint64_t read_at_le64(const void *src, size_t offset) | |||
| { | |||
| const uint8_t *s = src; | |||
| s += offset; | |||
| return read_le64(s); | |||
| } | |||
| static inline void write_le64(void *dest, uint64_t val) | |||
| { | |||
| write_le32(dest, val >> 0); | |||
| write_at_le32(dest, val >> 32, sizeof(uint32_t)); | |||
| } | |||
| static inline void write_at_le64(void *dest, uint64_t val, size_t offset) | |||
| { | |||
| uint8_t *d = dest; | |||
| d += offset; | |||
| write_le64(d, val); | |||
| } | |||
| static inline void zero_n(void *dest, size_t n) | |||
| { | |||
| memset(dest, 0, n); | |||
| } | |||
| #endif | |||
+ 74
- 0
t430/util/commonlib/include/commonlib/fmap_serialized.h
View File
| @ -0,0 +1,74 @@ | |||
| /* | |||
| * Copyright 2010, Google Inc. | |||
| * All rights reserved. | |||
| * | |||
| * Redistribution and use in source and binary forms, with or without | |||
| * modification, are permitted provided that the following conditions are | |||
| * met: | |||
| * | |||
| * * Redistributions of source code must retain the above copyright | |||
| * notice, this list of conditions and the following disclaimer. | |||
| * * Redistributions in binary form must reproduce the above | |||
| * copyright notice, this list of conditions and the following disclaimer | |||
| * in the documentation and/or other materials provided with the | |||
| * distribution. | |||
| * * Neither the name of Google Inc. nor the names of its | |||
| * contributors may be used to endorse or promote products derived from | |||
| * this software without specific prior written permission. | |||
| * | |||
| * THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS | |||
| * "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT | |||
| * LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR | |||
| * A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT | |||
| * OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, | |||
| * SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT | |||
| * LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, | |||
| * DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY | |||
| * THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT | |||
| * (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE | |||
| * OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. | |||
| * | |||
| * Alternatively, this software may be distributed under the terms of the | |||
| * GNU General Public License ("GPL") version 2 as published by the Free | |||
| * Software Foundation. | |||
| */ | |||
| #ifndef FLASHMAP_SERIALIZED_H__ | |||
| #define FLASHMAP_SERIALIZED_H__ | |||
| #include <stdint.h> | |||
| #include <compiler.h> | |||
| #define FMAP_SIGNATURE "__FMAP__" | |||
| #define FMAP_VER_MAJOR 1 /* this header's FMAP minor version */ | |||
| #define FMAP_VER_MINOR 1 /* this header's FMAP minor version */ | |||
| #define FMAP_STRLEN 32 /* maximum length for strings, */ | |||
| /* including null-terminator */ | |||
| enum fmap_flags { | |||
| FMAP_AREA_STATIC = 1 << 0, | |||
| FMAP_AREA_COMPRESSED = 1 << 1, | |||
| FMAP_AREA_RO = 1 << 2, | |||
| }; | |||
| /* Mapping of volatile and static regions in firmware binary */ | |||
| struct fmap_area { | |||
| uint32_t offset; /* offset relative to base */ | |||
| uint32_t size; /* size in bytes */ | |||
| uint8_t name[FMAP_STRLEN]; /* descriptive name */ | |||
| uint16_t flags; /* flags for this area */ | |||
| } __packed; | |||
| struct fmap { | |||
| uint8_t signature[8]; /* "__FMAP__" (0x5F5F464D41505F5F) */ | |||
| uint8_t ver_major; /* major version */ | |||
| uint8_t ver_minor; /* minor version */ | |||
| uint64_t base; /* address of the firmware binary */ | |||
| uint32_t size; /* size of firmware binary in bytes */ | |||
| uint8_t name[FMAP_STRLEN]; /* name of this firmware binary */ | |||
| uint16_t nareas; /* number of areas described by | |||
| fmap_areas[] below */ | |||
| struct fmap_area areas[]; | |||
| } __packed; | |||
| #endif /* FLASHMAP_SERIALIZED_H__ */ | |||
+ 32
- 0
t430/util/commonlib/include/commonlib/fsp.h
View File
| @ -0,0 +1,32 @@ | |||
| /* | |||
| * This file is part of the coreboot project. | |||
| * | |||
| * Copyright 2016 Google Inc. | |||
| * | |||
| * This program is free software; you can redistribute it and/or modify | |||
| * it under the terms of the GNU General Public License as published by | |||
| * the Free Software Foundation; version 2 of the License. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| */ | |||
| #ifndef _COMMONLIB_FSP_H_ | |||
| #define _COMMONLIB_FSP_H_ | |||
| #include <stddef.h> | |||
| #include <stdint.h> | |||
| #include <sys/types.h> | |||
| /* | |||
| * Relocate FSP held within buffer defined by size to new_addr. Returns < 0 | |||
| * on error, offset to FSP_INFO_HEADER on success. | |||
| */ | |||
| ssize_t fsp_component_relocate(uintptr_t new_addr, void *fsp, size_t size); | |||
| /* API to relocate fsp 1.1 component. */ | |||
| ssize_t fsp1_1_relocate(uintptr_t new_addr, void *fsp, size_t size); | |||
| #endif | |||
+ 99
- 0
t430/util/commonlib/include/commonlib/helpers.h
View File
| @ -0,0 +1,99 @@ | |||
| /* | |||
| * This file is part of the coreboot project. | |||
| * | |||
| * This program is free software; you can redistribute it and/or modify | |||
| * it under the terms of the GNU General Public License as published by | |||
| * the Free Software Foundation; version 2 of the License. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| */ | |||
| #ifndef COMMONLIB_HELPERS_H | |||
| #define COMMONLIB_HELPERS_H | |||
| /* This file is for helpers for both coreboot firmware and its utilities. */ | |||
| #ifndef __ASSEMBLER__ | |||
| #include <stddef.h> | |||
| #endif | |||
| #ifndef ARRAY_SIZE | |||
| #define ARRAY_SIZE(a) (sizeof(a) / sizeof((a)[0])) | |||
| #endif | |||
| #define ALIGN(x, a) __ALIGN_MASK(x, (__typeof__(x))(a)-1UL) | |||
| #define __ALIGN_MASK(x, mask) (((x)+(mask))&~(mask)) | |||
| #define ALIGN_UP(x, a) ALIGN((x), (a)) | |||
| #define ALIGN_DOWN(x, a) ((x) & ~((__typeof__(x))(a)-1UL)) | |||
| #define IS_ALIGNED(x, a) (((x) & ((__typeof__(x))(a)-1UL)) == 0) | |||
| #ifndef MIN | |||
| #define MIN(a, b) ((a) < (b) ? (a) : (b)) | |||
| #endif | |||
| #ifndef MAX | |||
| #define MAX(a, b) ((a) > (b) ? (a) : (b)) | |||
| #endif | |||
| #define ABS(a) (((a) < 0) ? (-(a)) : (a)) | |||
| #define CEIL_DIV(a, b) (((a) + (b) - 1) / (b)) | |||
| #define IS_POWER_OF_2(x) (((x) & ((x) - 1)) == 0) | |||
| #define DIV_ROUND_UP(x, y) (((x) + (y) - 1) / (y)) | |||
| /* | |||
| * Divide positive or negative dividend by positive divisor and round | |||
| * to closest integer. Result is undefined for negative divisors and | |||
| * for negative dividends if the divisor variable type is unsigned. | |||
| */ | |||
| #define DIV_ROUND_CLOSEST(x, divisor)( \ | |||
| { \ | |||
| typeof(x) __x = x; \ | |||
| typeof(divisor) __d = divisor; \ | |||
| (((typeof(x))-1) > 0 || \ | |||
| ((typeof(divisor))-1) > 0 || (__x) > 0) ? \ | |||
| (((__x) + ((__d) / 2)) / (__d)) : \ | |||
| (((__x) - ((__d) / 2)) / (__d)); \ | |||
| } \ | |||
| ) | |||
| /* Standard units. */ | |||
| #define KiB (1<<10) | |||
| #define MiB (1<<20) | |||
| #define GiB (1<<30) | |||
| /* Could we ever run into this one? I hope we get this much memory! */ | |||
| #define TiB (1<<40) | |||
| #define KHz (1000) | |||
| #define MHz (1000 * KHz) | |||
| #define GHz (1000 * MHz) | |||
| #ifndef offsetof | |||
| #define offsetof(TYPE, MEMBER) ((size_t) &((TYPE *)0)->MEMBER) | |||
| #endif | |||
| #if !defined(__clang__) | |||
| #define check_member(structure, member, offset) _Static_assert( \ | |||
| offsetof(struct structure, member) == offset, \ | |||
| "`struct " #structure "` offset for `" #member "` is not " #offset) | |||
| #else | |||
| #define check_member(structure, member, offset) | |||
| #endif | |||
| /** | |||
| * container_of - cast a member of a structure out to the containing structure | |||
| * @param ptr: the pointer to the member. | |||
| * @param type: the type of the container struct this is embedded in. | |||
| * @param member: the name of the member within the struct. | |||
| * | |||
| */ | |||
| #define container_of(ptr, type, member) ({ \ | |||
| const __typeof__(((type *)0)->member) *__mptr = (ptr); \ | |||
| (type *)((char *)__mptr - offsetof(type, member)); }) | |||
| /* Calculate size of structure member. */ | |||
| #define member_size(type, member) (sizeof(((type *)0)->member)) | |||
| #ifndef __unused | |||
| #define __unused __attribute__((unused)) | |||
| #endif | |||
| #endif /* COMMONLIB_HELPERS_H */ | |||
+ 162
- 0
t430/util/commonlib/include/commonlib/iobuf.h
View File
| @ -0,0 +1,162 @@ | |||
| /* | |||
| * This file is part of the coreboot project. | |||
| * | |||
| * Copyright 2017 Google Inc. | |||
| * | |||
| * This program is free software; you can redistribute it and/or modify | |||
| * it under the terms of the GNU General Public License as published by | |||
| * the Free Software Foundation; version 2 of the License. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| */ | |||
| #ifndef COMMONLIB_IOBUF_H | |||
| #define COMMONLIB_IOBUF_H | |||
| #include <stdint.h> | |||
| #include <sys/types.h> | |||
| /* | |||
| * Two types are provided to aid in dealing with automatic buffer management | |||
| * for code that deals with serializing and deserializing data structures. | |||
| * The ibuf (input buffer) is read from while the obuf (output buffer) is | |||
| * written to. Both keep track of capacity of the buffer as well as current | |||
| * read or write cursor. | |||
| * | |||
| * When splicing or splitting ibufs of obufs the source object doesn't track | |||
| * reads or writes through the newly created objects back to the source object. | |||
| * | |||
| * Any function returning an int encodes the return values as < 0 on error | |||
| * and 0 on success. Any function returning a pointer returns NULL on error | |||
| * and non-NULL on success. | |||
| */ | |||
| struct ibuf { | |||
| const uint8_t *b; | |||
| size_t n_read; | |||
| size_t capacity; | |||
| }; | |||
| struct obuf { | |||
| uint8_t *b; | |||
| size_t n_written; | |||
| size_t capacity; | |||
| }; | |||
| /* Helper functions. */ | |||
| static inline size_t ibuf_capacity(const struct ibuf *ib) | |||
| { | |||
| return ib->capacity; | |||
| } | |||
| static inline size_t ibuf_nr_read(const struct ibuf *ib) | |||
| { | |||
| return ib->n_read; | |||
| } | |||
| static inline size_t ibuf_remaining(const struct ibuf *ib) | |||
| { | |||
| return ibuf_capacity(ib) - ibuf_nr_read(ib); | |||
| } | |||
| static inline size_t obuf_capacity(const struct obuf *ob) | |||
| { | |||
| return ob->capacity; | |||
| } | |||
| static inline size_t obuf_nr_written(const struct obuf *ob) | |||
| { | |||
| return ob->n_written; | |||
| } | |||
| static inline size_t obuf_remaining(const struct obuf *ob) | |||
| { | |||
| return obuf_capacity(ob) - obuf_nr_written(ob); | |||
| } | |||
| /* Initialize an ibuf with buffer and size of data. */ | |||
| void ibuf_init(struct ibuf *ib, const void *b, size_t sz); | |||
| /* Create a new ibuf based on a subregion of the src ibuf. */ | |||
| int ibuf_splice(const struct ibuf *src, struct ibuf *dst, size_t off, | |||
| size_t sz); | |||
| /* Same as ibuf_splice(), but start from last read byte offset. */ | |||
| int ibuf_splice_current(const struct ibuf *src, struct ibuf *dst, size_t sz); | |||
| /* Split an ibuf into 2 new ibufs at provided boundary. */ | |||
| int ibuf_split(const struct ibuf *src, struct ibuf *a, struct ibuf *b, | |||
| size_t boundary); | |||
| /* Out-of-band drain of ibuf by returning pointer to data of specified size. */ | |||
| const void *ibuf_oob_drain(struct ibuf *ib, size_t sz); | |||
| /* Read arbitray data from input buffer. */ | |||
| int ibuf_read(struct ibuf *ib, void *data, size_t sz); | |||
| /* Read big endian fixed size values. */ | |||
| int ibuf_read_be8(struct ibuf *ib, uint8_t *v); | |||
| int ibuf_read_be16(struct ibuf *ib, uint16_t *v); | |||
| int ibuf_read_be32(struct ibuf *ib, uint32_t *v); | |||
| int ibuf_read_be64(struct ibuf *ib, uint64_t *v); | |||
| /* Read little endian fixed size values. */ | |||
| int ibuf_read_le8(struct ibuf *ib, uint8_t *v); | |||
| int ibuf_read_le16(struct ibuf *ib, uint16_t *v); | |||
| int ibuf_read_le32(struct ibuf *ib, uint32_t *v); | |||
| int ibuf_read_le64(struct ibuf *ib, uint64_t *v); | |||
| /* Read native endian fixed size values. */ | |||
| int ibuf_read_n8(struct ibuf *ib, uint8_t *v); | |||
| int ibuf_read_n16(struct ibuf *ib, uint16_t *v); | |||
| int ibuf_read_n32(struct ibuf *ib, uint32_t *v); | |||
| int ibuf_read_n64(struct ibuf *ib, uint64_t *v); | |||
| /* Helper to create an ibuf from an obuf after an entity has written data. */ | |||
| void ibuf_from_obuf(struct ibuf *ib, const struct obuf *ob); | |||
| /* Initialize an obuf with buffer and maximum capacity. */ | |||
| void obuf_init(struct obuf *ob, void *b, size_t sz); | |||
| /* Provide the buffer and size of the written contents. */ | |||
| const void *obuf_contents(const struct obuf *ob, size_t *sz); | |||
| /* Create a new obuf based on a subregion of the src obuf. */ | |||
| int obuf_splice(const struct obuf *src, struct obuf *dst, size_t off, | |||
| size_t sz); | |||
| /* Same as obuf_splice(), but start from last written byte offset. */ | |||
| int obuf_splice_current(const struct obuf *src, struct obuf *dst, size_t sz); | |||
| /* Split an obuf into 2 new obufs at provided boundary. */ | |||
| int obuf_split(const struct obuf *src, struct obuf *a, struct obuf *b, | |||
| size_t boundary); | |||
| /* Fill the buffer out-of-band. The size is accounted for. */ | |||
| void *obuf_oob_fill(struct obuf *ob, size_t sz); | |||
| /* Write arbitray data to output buffer. */ | |||
| int obuf_write(struct obuf *ob, const void *data, size_t sz); | |||
| /* Write big endian fixed size values. */ | |||
| int obuf_write_be8(struct obuf *ob, uint8_t v); | |||
| int obuf_write_be16(struct obuf *ob, uint16_t v); | |||
| int obuf_write_be32(struct obuf *ob, uint32_t v); | |||
| int obuf_write_be64(struct obuf *ob, uint64_t v); | |||
| /* Write little endian fixed size values. */ | |||
| int obuf_write_le8(struct obuf *ob, uint8_t v); | |||
| int obuf_write_le16(struct obuf *ob, uint16_t v); | |||
| int obuf_write_le32(struct obuf *ob, uint32_t v); | |||
| int obuf_write_le64(struct obuf *ob, uint64_t v); | |||
| /* Write native endian fixed size values. */ | |||
| int obuf_write_n8(struct obuf *ob, uint8_t v); | |||
| int obuf_write_n16(struct obuf *ob, uint16_t v); | |||
| int obuf_write_n32(struct obuf *ob, uint32_t v); | |||
| int obuf_write_n64(struct obuf *ob, uint64_t v); | |||
| #endif | |||
+ 174
- 0
t430/util/commonlib/include/commonlib/loglevel.h
View File
| @ -0,0 +1,174 @@ | |||
| /* | |||
| * This file is part of the coreboot project. | |||
| * | |||
| * Copyright (C) 2015 Nicholas Sielicki <sielicki@nicky.io> | |||
| * | |||
| * This program is free software; you can redistribute it and/or modify | |||
| * it under the terms of the GNU General Public License as published by | |||
| * the Free Software Foundation; either version 2 of the License, or | |||
| * (at your option) any later version. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| */ | |||
| #ifndef LOGLEVEL_H | |||
| #define LOGLEVEL_H | |||
| /** | |||
| * @file loglevel.h | |||
| * | |||
| * \brief Definitions of the log levels to be used in printk calls. | |||
| * | |||
| * Safe for inclusion in assembly. | |||
| * | |||
| */ | |||
| /** | |||
| * \brief BIOS_EMERG - Emergency / Fatal | |||
| * | |||
| * Log level for when the system is entirely unusable. To be used when execution | |||
| * is halting as a result of the failure. No further instructions should run. | |||
| * | |||
| * Example - End of all debug output / death notice. | |||
| * | |||
| * @{ | |||
| */ | |||
| #define BIOS_EMERG 0 | |||
| /** @} */ | |||
| /** | |||
| * \brief BIOS_ALERT - Dying / Unrecoverable | |||
| * | |||
| * Log level for when the system is certainly in the process of dying. | |||
| * To be used when execution will eventually halt as a result of the | |||
| * failure, but the system can still output valuable debugging | |||
| * information. | |||
| * | |||
| * Example - Ram initialization fails, dumping relevant POST codes and | |||
| * information | |||
| * | |||
| * @{ | |||
| */ | |||
| #define BIOS_ALERT 1 | |||
| /** @} */ | |||
| /** | |||
| * \brief BIOS_CRIT - Recovery unlikely | |||
| * | |||
| * Log level for when the system has experienced a dire issue in essential | |||
| * components. To be used when boot will probably be unsuccessful as a | |||
| * result of the failure, but recovery/retry can be attempted. | |||
| * | |||
| * Example - MSR failures, SMM/SMI failures. | |||
| * or | |||
| * | |||
| * @{ | |||
| */ | |||
| #define BIOS_CRIT 2 | |||
| /** @} */ | |||
| /** | |||
| * \brief BIOS_ERR - System in incomplete state. | |||
| * | |||
| * Log level for when the system has experienced an issue that may not preclude | |||
| * a successful boot. To be used when coreboot execution may still succeed, | |||
| * but the error places some non-essential portion of the machine in a broken | |||
| * state that will be noticed downstream. | |||
| * | |||
| * Example - Payload could still load, but will be missing access to integral | |||
| * components such as drives. | |||
| * | |||
| * @{ | |||
| */ | |||
| #define BIOS_ERR 3 | |||
| /** @} */ | |||
| /** | |||
| * \brief BIOS_WARNING - Bad configuration | |||
| * | |||
| * Log level for when the system has noticed an issue that most likely will | |||
| * not preclude a successful boot. To be used when something is wrong, and | |||
| * would likely be noticed by an end user. | |||
| * | |||
| * Example - Bad ME firmware, bad microcode, mis-clocked CPU | |||
| * | |||
| * @{ | |||
| */ | |||
| #define BIOS_WARNING 4 | |||
| /** @} */ | |||
| /** | |||
| * \brief BIOS_NOTICE - Unexpected but relatively insignificant | |||
| * | |||
| * Log level for when the system has noticed an issue that is an edge case, | |||
| * but is handled and is recoverable. To be used when an end-user would likely | |||
| * not notice. | |||
| * | |||
| * Example - Hardware was misconfigured, but is promptly fixed. | |||
| * | |||
| * @{ | |||
| */ | |||
| #define BIOS_NOTICE 5 | |||
| /** @} */ | |||
| /** | |||
| * \brief BIOS_INFO - Expected events. | |||
| * | |||
| * Log level for when the system has experienced some typical event. | |||
| * Messages should be superficial in nature. | |||
| * | |||
| * Example - Success messages. Status messages. | |||
| * | |||
| * @{ | |||
| */ | |||
| #define BIOS_INFO 6 | |||
| /** @} */ | |||
| /** | |||
| * \brief BIOS_DEBUG - Verbose output | |||
| * | |||
| * Log level for details of a method. Messages may be dense, | |||
| * but should not be excessive. Messages should be detailed enough | |||
| * that this level provides sufficient details to diagnose a problem, | |||
| * but not necessarily enough to fix it. | |||
| * | |||
| * Example - Printing of important variables. | |||
| * | |||
| * @{ | |||
| */ | |||
| #define BIOS_DEBUG 7 | |||
| /** @} */ | |||
| /** | |||
| * \brief BIOS_SPEW - Excessively verbose output | |||
| * | |||
| * Log level for intricacies of a method. Messages might contain raw | |||
| * data and will produce large logs. Developers should try to make sure | |||
| * that this level is not useful to anyone besides developers. | |||
| * | |||
| * Example - Data dumps. | |||
| * | |||
| * @{ | |||
| */ | |||
| #define BIOS_SPEW 8 | |||
| /** @} */ | |||
| /** | |||
| * \brief BIOS_NEVER - Muted log level. | |||
| * | |||
| * Roughly equal to commenting out a printk statement. Because a user | |||
| * should not set their log level higher than 8, these statements | |||
| * are never printed. | |||
| * | |||
| * Example - A developer might locally define MY_LOGLEVEL to BIOS_SPEW, | |||
| * and later replace it with BIOS_NEVER as to mute their debug output. | |||
| * | |||
| * @{ | |||
| */ | |||
| #define BIOS_NEVER 9 | |||
| /** @} */ | |||
| #endif /* LOGLEVEL_H */ | |||
+ 69
- 0
t430/util/commonlib/include/commonlib/mem_pool.h
View File
| @ -0,0 +1,69 @@ | |||
| /* | |||
| * This file is part of the coreboot project. | |||
| * | |||
| * Copyright 2015 Google Inc. | |||
| * | |||
| * This program is free software; you can redistribute it and/or modify | |||
| * it under the terms of the GNU General Public License as published by | |||
| * the Free Software Foundation; version 2 of the License. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| */ | |||
| #ifndef _MEM_POOL_H_ | |||
| #define _MEM_POOL_H_ | |||
| #include <stddef.h> | |||
| #include <stdint.h> | |||
| /* | |||
| * The memory pool allows one to allocate memory from a fixed size buffer | |||
| * that also allows freeing semantics for reuse. However, the current | |||
| * limitation is that the most recent allocation is the only one that | |||
| * can be freed. If one tries to free any allocation that isn't the | |||
| * most recently allocated it will result in a leak within the memory pool. | |||
| * | |||
| * The memory returned by allocations are at least 8 byte aligned. Note | |||
| * that this requires the backing buffer to start on at least an 8 byte | |||
| * alignment. | |||
| */ | |||
| struct mem_pool { | |||
| uint8_t *buf; | |||
| size_t size; | |||
| uint8_t *last_alloc; | |||
| size_t free_offset; | |||
| }; | |||
| #define MEM_POOL_INIT(buf_, size_) \ | |||
| { \ | |||
| .buf = (buf_), \ | |||
| .size = (size_), \ | |||
| .last_alloc = NULL, \ | |||
| .free_offset = 0, \ | |||
| } | |||
| static inline void mem_pool_reset(struct mem_pool *mp) | |||
| { | |||
| mp->last_alloc = NULL; | |||
| mp->free_offset = 0; | |||
| } | |||
| /* Initialize a memory pool. */ | |||
| static inline void mem_pool_init(struct mem_pool *mp, void *buf, size_t sz) | |||
| { | |||
| mp->buf = buf; | |||
| mp->size = sz; | |||
| mem_pool_reset(mp); | |||
| } | |||
| /* Allocate requested size from the memory pool. NULL returned on error. */ | |||
| void *mem_pool_alloc(struct mem_pool *mp, size_t sz); | |||
| /* Free allocation from memory pool. */ | |||
| void mem_pool_free(struct mem_pool *mp, void *alloc); | |||
| #endif /* _MEM_POOL_H_ */ | |||
+ 274
- 0
t430/util/commonlib/include/commonlib/region.h
View File
| @ -0,0 +1,274 @@ | |||
| /* | |||
| * This file is part of the coreboot project. | |||
| * | |||
| * Copyright 2015 Google Inc. | |||
| * | |||
| * This program is free software; you can redistribute it and/or modify | |||
| * it under the terms of the GNU General Public License as published by | |||
| * the Free Software Foundation; version 2 of the License. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| */ | |||
| #ifndef _REGION_H_ | |||
| #define _REGION_H_ | |||
| #include <sys/types.h> | |||
| #include <stdint.h> | |||
| #include <stddef.h> | |||
| #include <commonlib/mem_pool.h> | |||
| /* | |||
| * Region support. | |||
| * | |||
| * Regions are intended to abstract away the access mechanisms for blocks of | |||
| * data. This could be SPI, eMMC, or a memory region as the backing store. | |||
| * They are accessed through a region_device. Subregions can be made by | |||
| * chaining together multiple region_devices. | |||
| */ | |||
| struct region_device; | |||
| /* | |||
| * Returns NULL on error otherwise a buffer is returned with the conents of | |||
| * the requested data at offset of size. | |||
| */ | |||
| void *rdev_mmap(const struct region_device *rd, size_t offset, size_t size); | |||
| /* Unmap a previously mapped area. Returns 0 on success, < 0 on error. */ | |||
| int rdev_munmap(const struct region_device *rd, void *mapping); | |||
| /* | |||
| * Returns < 0 on error otherwise returns size of data read at provided | |||
| * offset filling in the buffer passed. | |||
| */ | |||
| ssize_t rdev_readat(const struct region_device *rd, void *b, size_t offset, | |||
| size_t size); | |||
| /* | |||
| * Returns < 0 on error otherwise returns size of data wrote at provided | |||
| * offset from the buffer passed. | |||
| */ | |||
| ssize_t rdev_writeat(const struct region_device *rd, const void *b, | |||
| size_t offset, size_t size); | |||
| /* | |||
| * Returns < 0 on error otherwise returns size of data erased. | |||
| * If eraseat ops is not defined it returns size which indicates | |||
| * that operation was successful. | |||
| */ | |||
| ssize_t rdev_eraseat(const struct region_device *rd, size_t offset, | |||
| size_t size); | |||
| /**************************************** | |||
| * Implementation of a region device * | |||
| ****************************************/ | |||
| /* | |||
| * Create a child region of the parent provided the sub-region is within | |||
| * the parent's region. Returns < 0 on error otherwise 0 on success. Note | |||
| * that the child device only calls through the parent's operations. | |||
| */ | |||
| int rdev_chain(struct region_device *child, const struct region_device *parent, | |||
| size_t offset, size_t size); | |||
| /* A region_device operations. */ | |||
| struct region_device_ops { | |||
| void *(*mmap)(const struct region_device *, size_t, size_t); | |||
| int (*munmap)(const struct region_device *, void *); | |||
| ssize_t (*readat)(const struct region_device *, void *, size_t, size_t); | |||
| ssize_t (*writeat)(const struct region_device *, const void *, size_t, | |||
| size_t); | |||
| ssize_t (*eraseat)(const struct region_device *, size_t, size_t); | |||
| }; | |||
| struct region { | |||
| size_t offset; | |||
| size_t size; | |||
| }; | |||
| struct region_device { | |||
| const struct region_device *root; | |||
| const struct region_device_ops *ops; | |||
| struct region region; | |||
| }; | |||
| #define REGION_DEV_INIT(ops_, offset_, size_) \ | |||
| { \ | |||
| .root = NULL, \ | |||
| .ops = (ops_), \ | |||
| .region = { \ | |||
| .offset = (offset_), \ | |||
| .size = (size_), \ | |||
| }, \ | |||
| } | |||
| /* Helper to dynamically initialize region device. */ | |||
| void region_device_init(struct region_device *rdev, | |||
| const struct region_device_ops *ops, size_t offset, | |||
| size_t size); | |||
| /* Return 1 if child is subregion of parent, else 0. */ | |||
| int region_is_subregion(const struct region *p, const struct region *c); | |||
| static inline size_t region_offset(const struct region *r) | |||
| { | |||
| return r->offset; | |||
| } | |||
| static inline size_t region_sz(const struct region *r) | |||
| { | |||
| return r->size; | |||
| } | |||
| static inline const struct region *region_device_region( | |||
| const struct region_device *rdev) | |||
| { | |||
| return &rdev->region; | |||
| } | |||
| static inline size_t region_device_sz(const struct region_device *rdev) | |||
| { | |||
| return region_sz(region_device_region(rdev)); | |||
| } | |||
| static inline size_t region_device_offset(const struct region_device *rdev) | |||
| { | |||
| return region_offset(region_device_region(rdev)); | |||
| } | |||
| /* Memory map entire region device. Same semantics as rdev_mmap() above. */ | |||
| static inline void *rdev_mmap_full(const struct region_device *rd) | |||
| { | |||
| return rdev_mmap(rd, 0, region_device_sz(rd)); | |||
| } | |||
| /* | |||
| * Compute relative offset of the child (c) w.r.t. the parent (p). Returns < 0 | |||
| * when child is not within the parent's region. | |||
| */ | |||
| ssize_t rdev_relative_offset(const struct region_device *p, | |||
| const struct region_device *c); | |||
| struct mem_region_device { | |||
| char *base; | |||
| struct region_device rdev; | |||
| }; | |||
| /* Inititalize at runtime a mem_region_device. This would be used when | |||
| * the base and size are dynamic or can't be known during linking. | |||
| * There are two variants: read-only and read-write. */ | |||
| void mem_region_device_ro_init(struct mem_region_device *mdev, void *base, | |||
| size_t size); | |||
| void mem_region_device_rw_init(struct mem_region_device *mdev, void *base, | |||
| size_t size); | |||
| extern const struct region_device_ops mem_rdev_ro_ops; | |||
| extern const struct region_device_ops mem_rdev_rw_ops; | |||
| /* Statically initialize mem_region_device. */ | |||
| #define MEM_REGION_DEV_INIT(base_, size_, ops_) \ | |||
| { \ | |||
| .base = (void *)(base_), \ | |||
| .rdev = REGION_DEV_INIT((ops_), 0, (size_)), \ | |||
| } | |||
| #define MEM_REGION_DEV_RO_INIT(base_, size_) \ | |||
| MEM_REGION_DEV_INIT(base_, size_, &mem_rdev_ro_ops) \ | |||
| #define MEM_REGION_DEV_RW_INIT(base_, size_) \ | |||
| MEM_REGION_DEV_INIT(base_, size_, &mem_rdev_rw_ops) \ | |||
| struct mmap_helper_region_device { | |||
| struct mem_pool pool; | |||
| struct region_device rdev; | |||
| }; | |||
| #define MMAP_HELPER_REGION_INIT(ops_, offset_, size_) \ | |||
| { \ | |||
| .rdev = REGION_DEV_INIT((ops_), (offset_), (size_)), \ | |||
| } | |||
| void mmap_helper_device_init(struct mmap_helper_region_device *mdev, | |||
| void *cache, size_t cache_size); | |||
| void *mmap_helper_rdev_mmap(const struct region_device *, size_t, size_t); | |||
| int mmap_helper_rdev_munmap(const struct region_device *, void *); | |||
| /* A translated region device provides the ability to publish a region device | |||
| * in one address space and use an access mechanism within another address | |||
| * space. The sub region is the window within the 1st address space and | |||
| * the request is modified prior to accessing the second address space | |||
| * provided by access_dev. */ | |||
| struct xlate_region_device { | |||
| const struct region_device *access_dev; | |||
| struct region sub_region; | |||
| struct region_device rdev; | |||
| }; | |||
| extern const struct region_device_ops xlate_rdev_ro_ops; | |||
| extern const struct region_device_ops xlate_rdev_rw_ops; | |||
| #define XLATE_REGION_DEV_INIT(access_dev_, sub_offset_, sub_size_, \ | |||
| parent_sz_, ops_) \ | |||
| { \ | |||
| .access_dev = access_dev_, \ | |||
| .sub_region = { \ | |||
| .offset = (sub_offset_), \ | |||
| .size = (sub_size_), \ | |||
| }, \ | |||
| .rdev = REGION_DEV_INIT((ops_), 0, (parent_sz_)), \ | |||
| } | |||
| #define XLATE_REGION_DEV_RO_INIT(access_dev_, sub_offset_, sub_size_, \ | |||
| parent_sz_) \ | |||
| XLATE_REGION_DEV_INIT(access_dev_, sub_offset_, \ | |||
| sub_size_, parent_sz_, &xlate_rdev_ro_ops), \ | |||
| #define XLATE_REGION_DEV_RW_INIT(access_dev_, sub_offset_, sub_size_, \ | |||
| parent_sz_) \ | |||
| XLATE_REGION_DEV_INIT(access_dev_, sub_offset_, \ | |||
| sub_size_, parent_sz_, &xlate_rdev_rw_ops), \ | |||
| /* Helper to dynamically initialize xlate region device. */ | |||
| void xlate_region_device_ro_init(struct xlate_region_device *xdev, | |||
| const struct region_device *access_dev, | |||
| size_t sub_offset, size_t sub_size, | |||
| size_t parent_size); | |||
| void xlate_region_device_rw_init(struct xlate_region_device *xdev, | |||
| const struct region_device *access_dev, | |||
| size_t sub_offset, size_t sub_size, | |||
| size_t parent_size); | |||
| /* This type can be used for incoherent access where the read and write | |||
| * operations are backed by separate drivers. An example is x86 systems | |||
| * with memory mapped media for reading but use a spi flash driver for | |||
| * writing. One needs to ensure using this object is appropriate in context. */ | |||
| struct incoherent_rdev { | |||
| struct region_device rdev; | |||
| const struct region_device *read; | |||
| const struct region_device *write; | |||
| }; | |||
| /* Initialize an incoherent_rdev based on the region as well as the read and | |||
| * write rdevs. The read and write rdevs should match in size to the passed | |||
| * in region. If not the initialization will fail returning NULL. Otherwise | |||
| * the function will return a pointer to the containing region_device to | |||
| * be used for region operations. Therefore, the lifetime of the returned | |||
| * pointer matches the lifetime of the incoherent_rdev object. Likewise, | |||
| * the lifetime of the read and write rdev need to match the lifetime of | |||
| * the incoherent_rdev object. */ | |||
| const struct region_device *incoherent_rdev_init(struct incoherent_rdev *irdev, | |||
| const struct region *r, | |||
| const struct region_device *read, | |||
| const struct region_device *write); | |||
| #endif /* _REGION_H_ */ | |||
+ 60
- 0
t430/util/commonlib/include/commonlib/rmodule-defs.h
View File
| @ -0,0 +1,60 @@ | |||
| /* | |||
| * This file is part of the coreboot project. | |||
| * | |||
| * Copyright (C) 2014 Google Inc | |||
| * | |||
| * This program is free software; you can redistribute it and/or modify | |||
| * it under the terms of the GNU General Public License as published by | |||
| * the Free Software Foundation; version 2 of the License. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| */ | |||
| #ifndef RMODULE_DEFS_H | |||
| #define RMODULE_DEFS_H | |||
| #include <stdint.h> | |||
| #include <stddef.h> | |||
| #include <compiler.h> | |||
| #define RMODULE_MAGIC 0xf8fe | |||
| #define RMODULE_VERSION_1 1 | |||
| /* All fields with '_offset' in the name are byte offsets into the flat blob. | |||
| * The linker and the linker script takes are of assigning the values. */ | |||
| struct rmodule_header { | |||
| uint16_t magic; | |||
| uint8_t version; | |||
| uint8_t type; | |||
| /* The payload represents the program's loadable code and data. */ | |||
| uint32_t payload_begin_offset; | |||
| uint32_t payload_end_offset; | |||
| /* Begin and of relocation information about the program module. */ | |||
| uint32_t relocations_begin_offset; | |||
| uint32_t relocations_end_offset; | |||
| /* The starting address of the linked program. This address is vital | |||
| * for determining relocation offsets as the relocation info and other | |||
| * symbols (bss, entry point) need this value as a basis to calculate | |||
| * the offsets. | |||
| */ | |||
| uint32_t module_link_start_address; | |||
| /* The module_program_size is the size of memory used while running | |||
| * the program. The program is assumed to consume a contiguous amount | |||
| * of memory. */ | |||
| uint32_t module_program_size; | |||
| /* This is program's execution entry point. */ | |||
| uint32_t module_entry_point; | |||
| /* Optional parameter structure that can be used to pass data into | |||
| * the module. */ | |||
| uint32_t parameters_begin; | |||
| uint32_t parameters_end; | |||
| /* BSS section information so the loader can clear the bss. */ | |||
| uint32_t bss_begin; | |||
| uint32_t bss_end; | |||
| /* Add some room for growth. */ | |||
| uint32_t padding[4]; | |||
| } __packed; | |||
| #endif /* RMODULE_DEFS_H */ | |||
+ 228
- 0
t430/util/commonlib/include/commonlib/sd_mmc_ctrlr.h
View File
| @ -0,0 +1,228 @@ | |||
| /* | |||
| * Copyright 2011, Marvell Semiconductor Inc. | |||
| * Lei Wen <leiwen@marvell.com> | |||
| * | |||
| * Copyright 2017 Intel Corporation | |||
| * | |||
| * Controller independent definitions | |||
| * | |||
| * This program is free software; you can redistribute it and/or | |||
| * modify it under the terms of the GNU General Public License as | |||
| * published by the Free Software Foundation; either version 2 of | |||
| * the License, or (at your option) any later version. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| */ | |||
| #ifndef __COMMONLIB_SD_MMC_CTRLR_H__ | |||
| #define __COMMONLIB_SD_MMC_CTRLR_H__ | |||
| #include <stdint.h> | |||
| /* Error values returned by the storage drivers */ | |||
| #define CARD_UNUSABLE_ERR -17 /* Unusable Card */ | |||
| #define CARD_COMM_ERR -18 /* Communications Error */ | |||
| #define CARD_TIMEOUT -19 | |||
| #define CARD_IN_PROGRESS -20 /* operation is in progress */ | |||
| struct mmc_command { | |||
| uint16_t cmdidx; | |||
| /* Common commands */ | |||
| #define MMC_CMD_GO_IDLE_STATE 0 | |||
| #define MMC_CMD_SEND_OP_COND 1 | |||
| #define MMC_CMD_ALL_SEND_CID 2 | |||
| #define MMC_CMD_SET_DSR 4 | |||
| #define MMC_CMD_SELECT_CARD 7 | |||
| #define MMC_CMD_SEND_CSD 9 | |||
| #define MMC_CMD_SEND_CID 10 | |||
| #define MMC_CMD_STOP_TRANSMISSION 12 | |||
| #define MMC_CMD_SEND_STATUS 13 | |||
| #define MMC_CMD_SET_BLOCKLEN 16 | |||
| #define MMC_CMD_READ_SINGLE_BLOCK 17 | |||
| #define MMC_CMD_READ_MULTIPLE_BLOCK 18 | |||
| #define MMC_CMD_WRITE_SINGLE_BLOCK 24 | |||
| #define MMC_CMD_WRITE_MULTIPLE_BLOCK 25 | |||
| #define MMC_CMD_APP_CMD 55 | |||
| /* MMC specific commands */ | |||
| #define MMC_CMD_SET_RELATIVE_ADDR 3 | |||
| #define MMC_CMD_SWITCH 6 | |||
| #define MMC_CMD_SEND_EXT_CSD 8 | |||
| #define MMC_CMD_AUTO_TUNING_SEQUENCE 21 | |||
| #define MMC_CMD_ERASE_GROUP_START 35 | |||
| #define MMC_CMD_ERASE_GROUP_END 36 | |||
| #define MMC_CMD_ERASE 38 | |||
| #define MMC_CMD_SPI_READ_OCR 58 | |||
| #define MMC_CMD_SPI_CRC_ON_OFF 59 | |||
| /* SD specific commands */ | |||
| #define SD_CMD_SEND_RELATIVE_ADDR 3 | |||
| #define SD_CMD_SWITCH_FUNC 6 | |||
| #define SD_CMD_SEND_IF_COND 8 | |||
| #define SD_CMD_ERASE_WR_BLK_START 32 | |||
| #define SD_CMD_ERASE_WR_BLK_END 33 | |||
| /* SD specific APP commands */ | |||
| #define SD_CMD_APP_SET_BUS_WIDTH 6 | |||
| #define SD_CMD_APP_SEND_OP_COND 41 | |||
| #define SD_CMD_APP_SEND_SCR 51 | |||
| uint32_t resp_type; | |||
| #define CARD_RSP_PRESENT (1 << 0) | |||
| #define CARD_RSP_136 (1 << 1) /* 136 bit response */ | |||
| #define CARD_RSP_CRC (1 << 2) /* expect valid crc */ | |||
| #define CARD_RSP_BUSY (1 << 3) /* card may send busy */ | |||
| #define CARD_RSP_OPCODE (1 << 4) /* response contains opcode */ | |||
| #define CARD_RSP_NONE (0) | |||
| #define CARD_RSP_R1 (CARD_RSP_PRESENT|CARD_RSP_CRC|CARD_RSP_OPCODE) | |||
| #define CARD_RSP_R1b (CARD_RSP_PRESENT|CARD_RSP_CRC|CARD_RSP_OPCODE| \ | |||
| CARD_RSP_BUSY) | |||
| #define CARD_RSP_R2 (CARD_RSP_PRESENT|CARD_RSP_136|CARD_RSP_CRC) | |||
| #define CARD_RSP_R3 (CARD_RSP_PRESENT) | |||
| #define CARD_RSP_R4 (CARD_RSP_PRESENT) | |||
| #define CARD_RSP_R5 (CARD_RSP_PRESENT|CARD_RSP_CRC|CARD_RSP_OPCODE) | |||
| #define CARD_RSP_R6 (CARD_RSP_PRESENT|CARD_RSP_CRC|CARD_RSP_OPCODE) | |||
| #define CARD_RSP_R7 (CARD_RSP_PRESENT|CARD_RSP_CRC|CARD_RSP_OPCODE) | |||
| uint32_t cmdarg; | |||
| #define MMC_TRIM_ARG 0x1 | |||
| #define MMC_SECURE_ERASE_ARG 0x80000000 | |||
| uint32_t response[4]; | |||
| uint32_t flags; | |||
| #define CMD_FLAG_IGNORE_INHIBIT 1 | |||
| }; | |||
| #define SD_SWITCH_CHECK 0 | |||
| #define SD_SWITCH_SWITCH 1 | |||
| #define SD_DATA_4BIT 0x00040000 | |||
| /* SCR definitions in different words */ | |||
| #define SD_HIGHSPEED_BUSY 0x00020000 | |||
| #define SD_HIGHSPEED_SUPPORTED 0x00020000 | |||
| struct mmc_data { | |||
| union { | |||
| char *dest; | |||
| const char *src; | |||
| }; | |||
| uint32_t flags; | |||
| #define DATA_FLAG_READ 1 | |||
| #define DATA_FLAG_WRITE 2 | |||
| uint32_t blocks; | |||
| uint32_t blocksize; | |||
| }; | |||
| struct sd_mmc_ctrlr { | |||
| int (*send_cmd)(struct sd_mmc_ctrlr *ctrlr, | |||
| struct mmc_command *cmd, struct mmc_data *data); | |||
| void (*set_ios)(struct sd_mmc_ctrlr *ctrlr); | |||
| void (*tuning_start)(struct sd_mmc_ctrlr *ctrlr, int retune); | |||
| int (*is_tuning_complete)(struct sd_mmc_ctrlr *ctrlr, int *successful); | |||
| int initialized; | |||
| unsigned int version; | |||
| uint32_t voltages; | |||
| #define MMC_VDD_165_195 0x00000080 /* VDD voltage 1.65 - 1.95 */ | |||
| #define MMC_VDD_20_21 0x00000100 /* VDD voltage 2.0 ~ 2.1 */ | |||
| #define MMC_VDD_21_22 0x00000200 /* VDD voltage 2.1 ~ 2.2 */ | |||
| #define MMC_VDD_22_23 0x00000400 /* VDD voltage 2.2 ~ 2.3 */ | |||
| #define MMC_VDD_23_24 0x00000800 /* VDD voltage 2.3 ~ 2.4 */ | |||
| #define MMC_VDD_24_25 0x00001000 /* VDD voltage 2.4 ~ 2.5 */ | |||
| #define MMC_VDD_25_26 0x00002000 /* VDD voltage 2.5 ~ 2.6 */ | |||
| #define MMC_VDD_26_27 0x00004000 /* VDD voltage 2.6 ~ 2.7 */ | |||
| #define MMC_VDD_27_28 0x00008000 /* VDD voltage 2.7 ~ 2.8 */ | |||
| #define MMC_VDD_28_29 0x00010000 /* VDD voltage 2.8 ~ 2.9 */ | |||
| #define MMC_VDD_29_30 0x00020000 /* VDD voltage 2.9 ~ 3.0 */ | |||
| #define MMC_VDD_30_31 0x00040000 /* VDD voltage 3.0 ~ 3.1 */ | |||
| #define MMC_VDD_31_32 0x00080000 /* VDD voltage 3.1 ~ 3.2 */ | |||
| #define MMC_VDD_32_33 0x00100000 /* VDD voltage 3.2 ~ 3.3 */ | |||
| #define MMC_VDD_33_34 0x00200000 /* VDD voltage 3.3 ~ 3.4 */ | |||
| #define MMC_VDD_34_35 0x00400000 /* VDD voltage 3.4 ~ 3.5 */ | |||
| #define MMC_VDD_35_36 0x00800000 /* VDD voltage 3.5 ~ 3.6 */ | |||
| #define MMC_VDD_165_195_SHIFT 7 | |||
| uint32_t clock_base; /* Controller's base clock */ | |||
| uint32_t f_min; | |||
| uint32_t f_max; | |||
| uint32_t request_hz; /* Desired clock frequency */ | |||
| uint32_t bus_hz; /* Actual bus clock frequency */ | |||
| #define CLOCK_KHZ 1000 | |||
| #define CLOCK_MHZ (1000 * CLOCK_KHZ) | |||
| #define CLOCK_20MHZ (20 * CLOCK_MHZ) | |||
| #define CLOCK_25MHZ (25 * CLOCK_MHZ) | |||
| #define CLOCK_26MHZ (26 * CLOCK_MHZ) | |||
| #define CLOCK_50MHZ (50 * CLOCK_MHZ) | |||
| #define CLOCK_52MHZ (52 * CLOCK_MHZ) | |||
| #define CLOCK_200MHZ (200 * CLOCK_MHZ) | |||
| uint32_t bus_width; | |||
| uint32_t caps; | |||
| /* Generic controller & driver capabilities. Controller specific capabilities | |||
| * start at 0x00010000 | |||
| */ | |||
| #define DRVR_CAP_4BIT 0x00000001 | |||
| #define DRVR_CAP_8BIT 0x00000002 | |||
| #define DRVR_CAP_AUTO_CMD12 0x00000004 | |||
| #define DRVR_CAP_HC 0x00000008 | |||
| #define DRVR_CAP_HS 0x00000010 | |||
| #define DRVR_CAP_HS52 0x00000020 | |||
| #define DRVR_CAP_HS200 0x00000040 | |||
| #define DRVR_CAP_HS400 0x00000080 | |||
| #define DRVR_CAP_ENHANCED_STROBE 0x00000100 | |||
| #define DRVR_CAP_REMOVABLE 0x00000200 | |||
| #define DRVR_CAP_DMA_64BIT 0x00000400 | |||
| #define DRVR_CAP_HS200_TUNING 0x00000800 | |||
| uint32_t b_max; | |||
| uint32_t timing; | |||
| #define BUS_TIMING_LEGACY 0 | |||
| #define BUS_TIMING_MMC_HS 1 | |||
| #define BUS_TIMING_SD_HS 2 | |||
| #define BUS_TIMING_UHS_SDR12 3 | |||
| #define BUS_TIMING_UHS_SDR25 4 | |||
| #define BUS_TIMING_UHS_SDR50 5 | |||
| #define BUS_TIMING_UHS_SDR104 6 | |||
| #define BUS_TIMING_UHS_DDR50 7 | |||
| #define BUS_TIMING_MMC_DDR52 8 | |||
| #define BUS_TIMING_MMC_HS200 9 | |||
| #define BUS_TIMING_MMC_HS400 10 | |||
| #define BUS_TIMING_MMC_HS400ES 11 | |||
| uint32_t mdelay_before_cmd0; | |||
| uint32_t mdelay_after_cmd0; | |||
| uint32_t udelay_wait_after_cmd; | |||
| }; | |||
| /* SOC specific routine to override ctrlr->caps and .voltages | |||
| * | |||
| * Set/clear the necessary DRVR_CAP_xxx bits in ctrlr->caps to specify the | |||
| * controllers capabilities and driver workarounds. | |||
| * | |||
| * Set/clear the necessary MMC_VDD_xxx bits in ctrlr->voltages to specify the | |||
| * controllers power support. | |||
| */ | |||
| void soc_sd_mmc_controller_quirks(struct sd_mmc_ctrlr *ctrlr); | |||
| /* Optional routines to support logging */ | |||
| void sdhc_log_command(struct mmc_command *cmd); | |||
| void sdhc_log_command_issued(void); | |||
| void sdhc_log_response(uint32_t entries, uint32_t *response); | |||
| void sdhc_log_ret(int ret); | |||
| #endif /* __COMMONLIB_SD_MMC_CTRLR_H__ */ | |||
+ 76
- 0
t430/util/commonlib/include/commonlib/sdhci.h
View File
| @ -0,0 +1,76 @@ | |||
| /* | |||
| * Copyright 2011, Marvell Semiconductor Inc. | |||
| * Lei Wen <leiwen@marvell.com> | |||
| * | |||
| * Copyright 2017 Intel Corporation | |||
| * | |||
| * SD host controller specific definitions | |||
| * | |||
| * This program is free software; you can redistribute it and/or | |||
| * modify it under the terms of the GNU General Public License as | |||
| * published by the Free Software Foundation; either version 2 of | |||
| * the License, or (at your option) any later version. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| */ | |||
| #ifndef __COMMONLIB_SDHCI_H__ | |||
| #define __COMMONLIB_SDHCI_H__ | |||
| #include <commonlib/sd_mmc_ctrlr.h> | |||
| /* Driver specific capabilities */ | |||
| #define DRVR_CAP_1V8_VDD 0x00010000 | |||
| #define DRVR_CAP_32BIT_DMA_ADDR 0x00020000 | |||
| #define DRVR_CAP_BROKEN_R1B 0x00040000 | |||
| #define DRVR_CAP_NO_CD 0x00080000 | |||
| #define DRVR_CAP_NO_HISPD_BIT 0x00100000 | |||
| #define DRVR_CAP_NO_SIMULT_VDD_AND_POWER 0x00200000 | |||
| #define DRVR_CAP_REG32_RW 0x00400000 | |||
| #define DRVR_CAP_SPI 0x00800000 | |||
| #define DRVR_CAP_WAIT_SEND_CMD 0x01000000 | |||
| /* ADMA packet descriptor */ | |||
| struct sdhci_adma { | |||
| u16 attributes; | |||
| u16 length; | |||
| u32 addr; | |||
| }; | |||
| struct sdhci_adma64 { | |||
| u16 attributes; | |||
| u16 length; | |||
| u32 addr; | |||
| u32 addr_hi; | |||
| }; | |||
| struct sdhci_ctrlr { | |||
| struct sd_mmc_ctrlr sd_mmc_ctrlr; | |||
| void *ioaddr; | |||
| uint32_t b_max; | |||
| /* | |||
| * Dynamically allocated array of ADMA descriptors to use for data | |||
| * transfers | |||
| */ | |||
| struct sdhci_adma *adma_descs; | |||
| struct sdhci_adma64 *adma64_descs; | |||
| /* Number of ADMA descriptors currently in the array. */ | |||
| int adma_desc_count; | |||
| }; | |||
| int add_sdhci(struct sdhci_ctrlr *sdhci_ctrlr); | |||
| int sdhci_controller_init(struct sdhci_ctrlr *sdhci_ctrlr, void *ioaddr); | |||
| void sdhci_update_pointers(struct sdhci_ctrlr *sdhci_ctrlr); | |||
| void sdhci_display_setup(struct sdhci_ctrlr *sdhci_ctrlr); | |||
| /* Add SDHCI controller from PCI */ | |||
| struct sd_mmc_ctrlr *new_pci_sdhci_controller(uint32_t dev); | |||
| /* Add SDHCI controller with memory address */ | |||
| struct sd_mmc_ctrlr *new_mem_sdhci_controller(void *ioaddr); | |||
| #endif /* __COMMONLIB_SDHCI_H__ */ | |||
+ 74
- 0
t430/util/commonlib/include/commonlib/stdlib.h
View File
| @ -0,0 +1,74 @@ | |||
| /* | |||
| * This file is part of the libpayload project. | |||
| * | |||
| * Copyright (C) 2008 Advanced Micro Devices, Inc. | |||
| * Copyright 2013 Google Inc. | |||
| * | |||
| * Redistribution and use in source and binary forms, with or without | |||
| * modification, are permitted provided that the following conditions | |||
| * are met: | |||
| * 1. Redistributions of source code must retain the above copyright | |||
| * notice, this list of conditions and the following disclaimer. | |||
| * 2. Redistributions in binary form must reproduce the above copyright | |||
| * notice, this list of conditions and the following disclaimer in the | |||
| * documentation and/or other materials provided with the distribution. | |||
| * 3. The name of the author may not be used to endorse or promote products | |||
| * derived from this software without specific prior written permission. | |||
| * | |||
| * THIS SOFTWARE IS PROVIDED BY THE AUTHOR AND CONTRIBUTORS ``AS IS'' AND | |||
| * ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE | |||
| * IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE | |||
| * ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE | |||
| * FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL | |||
| * DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS | |||
| * OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) | |||
| * HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT | |||
| * LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY | |||
| * OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF | |||
| * SUCH DAMAGE. | |||
| */ | |||
| #ifndef __COMMONLIB_STDLIB_H__ | |||
| #define __COMMONLIB_STDLIB_H__ | |||
| #include <stddef.h> | |||
| #include <stdlib.h> | |||
| #include <string.h> | |||
| #if IS_ENABLED(CONFIG_COREBOOT_BUILD) | |||
| #include <console/console.h> | |||
| #include <halt.h> | |||
| #define printf(...) printk(BIOS_ERR, __VA_ARGS__) | |||
| #define HALT(x) halt() | |||
| #else | |||
| #include <stdio.h> | |||
| #define HALT(x) | |||
| #endif | |||
| static inline void *xmalloc_work(size_t size, const char *file, | |||
| const char *func, int line) | |||
| { | |||
| void *ret = malloc(size); | |||
| if (!ret && size) { | |||
| printf("%s/%s/line %d: Failed to malloc %zu bytes\n", | |||
| file, func, line, size); | |||
| while (1) | |||
| HALT(1); | |||
| } | |||
| return ret; | |||
| } | |||
| #define xmalloc(size) xmalloc_work((size), __FILE__, __FUNCTION__, __LINE__) | |||
| static inline void *xzalloc_work(size_t size, const char *file, | |||
| const char *func, int line) | |||
| { | |||
| void *ret = xmalloc_work(size, file, func, line); | |||
| memset(ret, 0, size); | |||
| return ret; | |||
| } | |||
| #define xzalloc(size) xzalloc_work((size), __FILE__, __FUNCTION__, __LINE__) | |||
| void *dma_malloc(size_t size); | |||
| int dma_coherent(void *ptr); | |||
| #endif /* __COMMONLIB_STDLIB_H__ */ | |||
+ 151
- 0
t430/util/commonlib/include/commonlib/storage.h
View File
| @ -0,0 +1,151 @@ | |||
| /* | |||
| * Copyright 2008,2010 Freescale Semiconductor, Inc | |||
| * Andy Fleming | |||
| * | |||
| * Copyright 2013 Google Inc. All rights reserved. | |||
| * Copyright 2017 Intel Corporation | |||
| * | |||
| * This program is free software; you can redistribute it and/or | |||
| * modify it under the terms of the GNU General Public License as | |||
| * published by the Free Software Foundation; either version 2 of | |||
| * the License, or (at your option) any later version. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| */ | |||
| #ifndef __COMMONLIB_STORAGE_H__ | |||
| #define __COMMONLIB_STORAGE_H__ | |||
| #include <commonlib/sd_mmc_ctrlr.h> | |||
| /* | |||
| * EXT_CSD fields | |||
| */ | |||
| #define EXT_CSD_GP_SIZE_MULT_GP0 143 /* RO */ | |||
| #define EXT_CSD_GP_SIZE_MULT_GP1 146 /* RO */ | |||
| #define EXT_CSD_GP_SIZE_MULT_GP2 149 /* RO */ | |||
| #define EXT_CSD_GP_SIZE_MULT_GP3 152 /* RO */ | |||
| #define EXT_CSD_PARTITIONING_SUPPORT 160 /* RO */ | |||
| #define EXT_CSD_RPMB_SIZE_MULT 168 /* RO */ | |||
| #define EXT_CSD_ERASE_GROUP_DEF 175 /* R/W */ | |||
| #define EXT_CSD_PART_CONF 179 /* R/W */ | |||
| #define EXT_CSD_BUS_WIDTH 183 /* R/W */ | |||
| #define EXT_CSD_STROBE_SUPPORT 184 /* RO */ | |||
| #define EXT_CSD_HS_TIMING 185 /* R/W */ | |||
| #define EXT_CSD_REV 192 /* RO */ | |||
| #define EXT_CSD_CARD_TYPE 196 /* RO */ | |||
| #define EXT_CSD_SEC_CNT 212 /* RO, 4 bytes */ | |||
| #define EXT_CSD_HC_WP_GRP_SIZE 221 /* RO */ | |||
| #define EXT_CSD_HC_ERASE_GRP_SIZE 224 /* RO */ | |||
| #define EXT_CSD_BOOT_SIZE_MULT 226 /* RO */ | |||
| #define EXT_CSD_TRIM_MULT 232 /* RO */ | |||
| /* | |||
| * EXT_CSD field definitions | |||
| */ | |||
| #define EXT_CSD_CMD_SET_NORMAL (1 << 0) | |||
| #define EXT_CSD_CMD_SET_SECURE (1 << 1) | |||
| #define EXT_CSD_CMD_SET_CPSECURE (1 << 2) | |||
| #define EXT_CSD_CARD_TYPE_26 (1 << 0) /* Card can run at 26MHz */ | |||
| #define EXT_CSD_CARD_TYPE_52 (1 << 1) /* Card can run at 52MHz */ | |||
| #define EXT_CSD_BUS_WIDTH_1 0 /* Card is in 1 bit mode */ | |||
| #define EXT_CSD_BUS_WIDTH_4 1 /* Card is in 4 bit mode */ | |||
| #define EXT_CSD_BUS_WIDTH_8 2 /* Card is in 8 bit mode */ | |||
| #define EXT_CSD_DDR_BUS_WIDTH_4 5 /* Card is in 4 bit DDR mode */ | |||
| #define EXT_CSD_DDR_BUS_WIDTH_8 6 /* Card is in 8 bit DDR mode */ | |||
| #define EXT_CSD_BUS_WIDTH_STROBE (1<<7) /* Enhanced strobe mode */ | |||
| #define EXT_CSD_TIMING_BC 0 /* Backwards compatility */ | |||
| #define EXT_CSD_TIMING_HS 1 /* High speed */ | |||
| #define EXT_CSD_TIMING_HS200 2 /* HS200 */ | |||
| #define EXT_CSD_TIMING_HS400 3 /* HS400 */ | |||
| #define EXT_CSD_SIZE 512 | |||
| /* 179: EXT_CSD_PART_CONF */ | |||
| #define EXT_CSD_PART_ACCESS_MASK 7 /* Partition access mask */ | |||
| /* 175: EXT_CSD_ERASE_GROUP_DEF */ | |||
| #define EXT_CSD_PARTITION_ENABLE 1 /* Enable partition access */ | |||
| struct storage_media { | |||
| uint64_t capacity[8]; /* Partition capacity in bytes */ | |||
| struct sd_mmc_ctrlr *ctrlr; | |||
| #define MMC_PARTITION_USER 0 | |||
| #define MMC_PARTITION_BOOT_1 1 | |||
| #define MMC_PARTITION_BOOT_2 2 | |||
| #define MMC_PARTITION_RPMB 3 | |||
| #define MMC_PARTITION_GP1 4 | |||
| #define MMC_PARTITION_GP2 5 | |||
| #define MMC_PARTITION_GP3 6 | |||
| #define MMC_PARTITION_GP4 7 | |||
| uint32_t caps; | |||
| uint32_t version; | |||
| #define SD_VERSION_SD 0x20000 | |||
| #define SD_VERSION_2 (SD_VERSION_SD | 0x20) | |||
| #define SD_VERSION_1_0 (SD_VERSION_SD | 0x10) | |||
| #define SD_VERSION_1_10 (SD_VERSION_SD | 0x1a) | |||
| #define MMC_VERSION_MMC 0x10000 | |||
| #define MMC_VERSION_UNKNOWN (MMC_VERSION_MMC) | |||
| #define MMC_VERSION_1_2 (MMC_VERSION_MMC | 0x12) | |||
| #define MMC_VERSION_1_4 (MMC_VERSION_MMC | 0x14) | |||
| #define MMC_VERSION_2_2 (MMC_VERSION_MMC | 0x22) | |||
| #define MMC_VERSION_3 (MMC_VERSION_MMC | 0x30) | |||
| #define MMC_VERSION_4 (MMC_VERSION_MMC | 0x40) | |||
| uint32_t read_bl_len; | |||
| uint32_t write_bl_len; | |||
| int high_capacity; | |||
| uint32_t tran_speed; | |||
| /* Erase size in terms of block length. */ | |||
| uint32_t erase_blocks; | |||
| /* Trim operation multiplier for determining timeout. */ | |||
| uint32_t trim_mult; | |||
| uint32_t ocr; | |||
| #define OCR_BUSY 0x80000000 | |||
| #define OCR_HCS 0x40000000 | |||
| #define OCR_VOLTAGE_MASK 0x00FFFF80 | |||
| #define OCR_ACCESS_MODE 0x60000000 | |||
| uint32_t op_cond_response; // The response byte from the last op_cond | |||
| uint32_t scr[2]; | |||
| uint32_t csd[4]; | |||
| uint32_t cid[4]; | |||
| uint16_t rca; | |||
| uint8_t partition_config; /* Duplicate of EXT_CSD_PART_CONF */ | |||
| }; | |||
| uint64_t storage_block_erase(struct storage_media *media, uint64_t start, | |||
| uint64_t count); | |||
| uint64_t storage_block_fill_write(struct storage_media *media, uint64_t start, | |||
| uint64_t count, uint32_t fill_pattern); | |||
| uint64_t storage_block_read(struct storage_media *media, uint64_t start, | |||
| uint64_t count, void *buffer); | |||
| uint64_t storage_block_write(struct storage_media *media, uint64_t start, | |||
| uint64_t count, const void *buffer); | |||
| unsigned int storage_get_current_partition(struct storage_media *media); | |||
| const char *storage_partition_name(struct storage_media *media, | |||
| unsigned int partition_number); | |||
| int storage_setup_media(struct storage_media *media, | |||
| struct sd_mmc_ctrlr *ctrlr); | |||
| int storage_set_partition(struct storage_media *media, | |||
| unsigned int partition_number); | |||
| void storage_display_setup(struct storage_media *media); | |||
| #endif /* __COMMONLIB_STORAGE_H__ */ | |||
+ 263
- 0
t430/util/commonlib/include/commonlib/timestamp_serialized.h
View File
| @ -0,0 +1,263 @@ | |||
| /* | |||
| * This file is part of the coreboot project. | |||
| * | |||
| * Copyright (C) 2011 The ChromiumOS Authors. All rights reserved. | |||
| * | |||
| * This program is free software; you can redistribute it and/or modify | |||
| * it under the terms of the GNU General Public License as published by | |||
| * the Free Software Foundation; version 2 of the License. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| */ | |||
| #ifndef __TIMESTAMP_SERIALIZED_H__ | |||
| #define __TIMESTAMP_SERIALIZED_H__ | |||
| #include <stdint.h> | |||
| #include <compiler.h> | |||
| struct timestamp_entry { | |||
| uint32_t entry_id; | |||
| uint64_t entry_stamp; | |||
| } __packed; | |||
| struct timestamp_table { | |||
| uint64_t base_time; | |||
| uint16_t max_entries; | |||
| uint16_t tick_freq_mhz; | |||
| uint32_t num_entries; | |||
| struct timestamp_entry entries[0]; /* Variable number of entries */ | |||
| } __packed; | |||
| enum timestamp_id { | |||
| TS_START_ROMSTAGE = 1, | |||
| TS_BEFORE_INITRAM = 2, | |||
| TS_AFTER_INITRAM = 3, | |||
| TS_END_ROMSTAGE = 4, | |||
| TS_START_VBOOT = 5, | |||
| TS_END_VBOOT = 6, | |||
| TS_START_COPYRAM = 8, | |||
| TS_END_COPYRAM = 9, | |||
| TS_START_RAMSTAGE = 10, | |||
| TS_START_BOOTBLOCK = 11, | |||
| TS_END_BOOTBLOCK = 12, | |||
| TS_START_COPYROM = 13, | |||
| TS_END_COPYROM = 14, | |||
| TS_START_ULZMA = 15, | |||
| TS_END_ULZMA = 16, | |||
| TS_START_ULZ4F = 17, | |||
| TS_END_ULZ4F = 18, | |||
| TS_DEVICE_ENUMERATE = 30, | |||
| TS_DEVICE_CONFIGURE = 40, | |||
| TS_DEVICE_ENABLE = 50, | |||
| TS_DEVICE_INITIALIZE = 60, | |||
| TS_OPROM_INITIALIZE = 65, | |||
| TS_OPROM_COPY_END = 66, | |||
| TS_OPROM_END = 67, | |||
| TS_DEVICE_DONE = 70, | |||
| TS_CBMEM_POST = 75, | |||
| TS_WRITE_TABLES = 80, | |||
| TS_FINALIZE_CHIPS = 85, | |||
| TS_LOAD_PAYLOAD = 90, | |||
| TS_ACPI_WAKE_JUMP = 98, | |||
| TS_SELFBOOT_JUMP = 99, | |||
| /* 500+ reserved for vendorcode extensions (500-600: google/chromeos) */ | |||
| TS_START_COPYVER = 501, | |||
| TS_END_COPYVER = 502, | |||
| TS_START_TPMINIT = 503, | |||
| TS_END_TPMINIT = 504, | |||
| TS_START_VERIFY_SLOT = 505, | |||
| TS_END_VERIFY_SLOT = 506, | |||
| TS_START_HASH_BODY = 507, | |||
| TS_DONE_LOADING = 508, | |||
| TS_DONE_HASHING = 509, | |||
| TS_END_HASH_BODY = 510, | |||
| TS_START_TPMPCR = 511, | |||
| TS_END_TPMPCR = 512, | |||
| TS_START_TPMLOCK = 513, | |||
| TS_END_TPMLOCK = 514, | |||
| TS_START_COPYVPD = 550, | |||
| TS_END_COPYVPD_RO = 551, | |||
| TS_END_COPYVPD_RW = 552, | |||
| /* 900-920 reserved for vendorcode extensions (900-940: AMD AGESA) */ | |||
| TS_AGESA_INIT_RESET_START = 900, | |||
| TS_AGESA_INIT_RESET_DONE = 901, | |||
| TS_AGESA_INIT_EARLY_START = 902, | |||
| TS_AGESA_INIT_EARLY_DONE = 903, | |||
| TS_AGESA_INIT_POST_START = 904, | |||
| TS_AGESA_INIT_POST_DONE = 905, | |||
| TS_AGESA_INIT_ENV_START = 906, | |||
| TS_AGESA_INIT_ENV_DONE = 907, | |||
| TS_AGESA_INIT_MID_START = 908, | |||
| TS_AGESA_INIT_MID_DONE = 909, | |||
| TS_AGESA_INIT_LATE_START = 910, | |||
| TS_AGESA_INIT_LATE_DONE = 911, | |||
| TS_AGESA_INIT_RTB_START = 912, | |||
| TS_AGESA_INIT_RTB_DONE = 913, | |||
| TS_AGESA_INIT_RESUME_START = 914, | |||
| TS_AGESA_INIT_RESUME_DONE = 915, | |||
| TS_AGESA_S3_LATE_START = 916, | |||
| TS_AGESA_S3_LATE_DONE = 917, | |||
| TS_AGESA_S3_FINAL_START = 918, | |||
| TS_AGESA_S3_FINAL_DONE = 919, | |||
| /* 940-950 reserved for vendorcode extensions (940-950: Intel ME) */ | |||
| TS_ME_INFORM_DRAM_WAIT = 940, | |||
| TS_ME_INFORM_DRAM_DONE = 941, | |||
| /* 950+ reserved for vendorcode extensions (950-999: intel/fsp) */ | |||
| TS_FSP_MEMORY_INIT_START = 950, | |||
| TS_FSP_MEMORY_INIT_END = 951, | |||
| TS_FSP_TEMP_RAM_EXIT_START = 952, | |||
| TS_FSP_TEMP_RAM_EXIT_END = 953, | |||
| TS_FSP_SILICON_INIT_START = 954, | |||
| TS_FSP_SILICON_INIT_END = 955, | |||
| TS_FSP_BEFORE_ENUMERATE = 956, | |||
| TS_FSP_AFTER_ENUMERATE = 957, | |||
| TS_FSP_BEFORE_FINALIZE = 958, | |||
| TS_FSP_AFTER_FINALIZE = 959, | |||
| TS_FSP_BEFORE_END_OF_FIRMWARE = 960, | |||
| TS_FSP_AFTER_END_OF_FIRMWARE = 961, | |||
| /* 1000+ reserved for payloads (1000-1200: ChromeOS depthcharge) */ | |||
| /* Depthcharge entry IDs start at 1000 */ | |||
| TS_DC_START = 1000, | |||
| TS_RO_PARAMS_INIT = 1001, | |||
| TS_RO_VB_INIT = 1002, | |||
| TS_RO_VB_SELECT_FIRMWARE = 1003, | |||
| TS_RO_VB_SELECT_AND_LOAD_KERNEL = 1004, | |||
| TS_RW_VB_SELECT_AND_LOAD_KERNEL = 1010, | |||
| TS_VB_SELECT_AND_LOAD_KERNEL = 1020, | |||
| TS_VB_EC_VBOOT_DONE = 1030, | |||
| TS_VB_STORAGE_INIT_DONE = 1040, | |||
| TS_VB_READ_KERNEL_DONE = 1050, | |||
| TS_VB_VBOOT_DONE = 1100, | |||
| TS_START_KERNEL = 1101, | |||
| TS_KERNEL_DECOMPRESSION = 1102, | |||
| }; | |||
| static const struct timestamp_id_to_name { | |||
| uint32_t id; | |||
| const char *name; | |||
| } timestamp_ids[] = { | |||
| /* Marker to report base_time. */ | |||
| { 0, "1st timestamp" }, | |||
| { TS_START_ROMSTAGE, "start of romstage" }, | |||
| { TS_BEFORE_INITRAM, "before ram initialization" }, | |||
| { TS_AFTER_INITRAM, "after ram initialization" }, | |||
| { TS_END_ROMSTAGE, "end of romstage" }, | |||
| { TS_START_VBOOT, "start of verified boot" }, | |||
| { TS_END_VBOOT, "end of verified boot" }, | |||
| { TS_START_COPYRAM, "starting to load ramstage" }, | |||
| { TS_END_COPYRAM, "finished loading ramstage" }, | |||
| { TS_START_RAMSTAGE, "start of ramstage" }, | |||
| { TS_START_BOOTBLOCK, "start of bootblock" }, | |||
| { TS_END_BOOTBLOCK, "end of bootblock" }, | |||
| { TS_START_COPYROM, "starting to load romstage" }, | |||
| { TS_END_COPYROM, "finished loading romstage" }, | |||
| { TS_START_ULZMA, "starting LZMA decompress (ignore for x86)" }, | |||
| { TS_END_ULZMA, "finished LZMA decompress (ignore for x86)" }, | |||
| { TS_START_ULZ4F, "starting LZ4 decompress (ignore for x86)" }, | |||
| { TS_END_ULZ4F, "finished LZ4 decompress (ignore for x86)" }, | |||
| { TS_DEVICE_ENUMERATE, "device enumeration" }, | |||
| { TS_DEVICE_CONFIGURE, "device configuration" }, | |||
| { TS_DEVICE_ENABLE, "device enable" }, | |||
| { TS_DEVICE_INITIALIZE, "device initialization" }, | |||
| { TS_OPROM_INITIALIZE, "Option ROM initialization" }, | |||
| { TS_OPROM_COPY_END, "Option ROM copy done" }, | |||
| { TS_OPROM_END, "Option ROM run done" }, | |||
| { TS_DEVICE_DONE, "device setup done" }, | |||
| { TS_CBMEM_POST, "cbmem post" }, | |||
| { TS_WRITE_TABLES, "write tables" }, | |||
| { TS_FINALIZE_CHIPS, "finalize chips" }, | |||
| { TS_LOAD_PAYLOAD, "load payload" }, | |||
| { TS_ACPI_WAKE_JUMP, "ACPI wake jump" }, | |||
| { TS_SELFBOOT_JUMP, "selfboot jump" }, | |||
| { TS_START_COPYVER, "starting to load verstage" }, | |||
| { TS_END_COPYVER, "finished loading verstage" }, | |||
| { TS_START_TPMINIT, "starting to initialize TPM" }, | |||
| { TS_END_TPMINIT, "finished TPM initialization" }, | |||
| { TS_START_VERIFY_SLOT, "starting to verify keyblock/preamble (RSA)" }, | |||
| { TS_END_VERIFY_SLOT, "finished verifying keyblock/preamble (RSA)" }, | |||
| { TS_START_HASH_BODY, "starting to verify body (load+SHA2+RSA) " }, | |||
| { TS_DONE_LOADING, "finished loading body (ignore for x86)" }, | |||
| { TS_DONE_HASHING, "finished calculating body hash (SHA2)" }, | |||
| { TS_END_HASH_BODY, "finished verifying body signature (RSA)" }, | |||
| { TS_START_TPMPCR, "starting TPM PCR extend" }, | |||
| { TS_END_TPMPCR, "finished TPM PCR extend" }, | |||
| { TS_START_TPMLOCK, "starting locking TPM" }, | |||
| { TS_END_TPMLOCK, "finished locking TPM" }, | |||
| { TS_START_COPYVPD, "starting to load Chrome OS VPD" }, | |||
| { TS_END_COPYVPD_RO, "finished loading Chrome OS VPD (RO)" }, | |||
| { TS_END_COPYVPD_RW, "finished loading Chrome OS VPD (RW)" }, | |||
| { TS_DC_START, "depthcharge start" }, | |||
| { TS_RO_PARAMS_INIT, "RO parameter init" }, | |||
| { TS_RO_VB_INIT, "RO vboot init" }, | |||
| { TS_RO_VB_SELECT_FIRMWARE, "RO vboot select firmware" }, | |||
| { TS_RO_VB_SELECT_AND_LOAD_KERNEL, "RO vboot select&load kernel" }, | |||
| { TS_RW_VB_SELECT_AND_LOAD_KERNEL, "RW vboot select&load kernel" }, | |||
| { TS_VB_SELECT_AND_LOAD_KERNEL, "vboot select&load kernel" }, | |||
| { TS_VB_EC_VBOOT_DONE, "finished EC verification" }, | |||
| { TS_VB_STORAGE_INIT_DONE, "finished storage device initialization" }, | |||
| { TS_VB_READ_KERNEL_DONE, "finished reading kernel from disk" }, | |||
| { TS_VB_VBOOT_DONE, "finished vboot kernel verification" }, | |||
| { TS_KERNEL_DECOMPRESSION, "starting kernel decompression/relocation" }, | |||
| { TS_START_KERNEL, "jumping to kernel" }, | |||
| /* AMD AGESA related timestamps */ | |||
| { TS_AGESA_INIT_RESET_START, "calling AmdInitReset" }, | |||
| { TS_AGESA_INIT_RESET_DONE, "back from AmdInitReset" }, | |||
| { TS_AGESA_INIT_EARLY_START, "calling AmdInitEarly" }, | |||
| { TS_AGESA_INIT_EARLY_DONE, "back from AmdInitEarly" }, | |||
| { TS_AGESA_INIT_POST_START, "calling AmdInitPost" }, | |||
| { TS_AGESA_INIT_POST_DONE, "back from AmdInitPost" }, | |||
| { TS_AGESA_INIT_ENV_START, "calling AmdInitEnv" }, | |||
| { TS_AGESA_INIT_ENV_DONE, "back from AmdInitEnv" }, | |||
| { TS_AGESA_INIT_MID_START, "calling AmdInitMid" }, | |||
| { TS_AGESA_INIT_MID_DONE, "back from AmdInitMid" }, | |||
| { TS_AGESA_INIT_LATE_START, "calling AmdInitLate" }, | |||
| { TS_AGESA_INIT_LATE_DONE, "back from AmdInitLate" }, | |||
| { TS_AGESA_INIT_RTB_START, "calling AmdInitRtb/AmdS3Save" }, | |||
| { TS_AGESA_INIT_RTB_DONE, "back from AmdInitRtb/AmdS3Save" }, | |||
| { TS_AGESA_INIT_RESUME_START, "calling AmdInitResume" }, | |||
| { TS_AGESA_INIT_RESUME_DONE, "back from AmdInitResume" }, | |||
| { TS_AGESA_S3_LATE_START, "calling AmdS3LateRestore" }, | |||
| { TS_AGESA_S3_LATE_DONE, "back from AmdS3LateRestore" }, | |||
| { TS_AGESA_S3_FINAL_START, "calling AmdS3FinalRestore" }, | |||
| { TS_AGESA_S3_FINAL_DONE, "back from AmdS3FinalRestore" }, | |||
| /* Intel ME related timestamps */ | |||
| { TS_ME_INFORM_DRAM_WAIT, "waiting for ME acknowledgement of raminit"}, | |||
| { TS_ME_INFORM_DRAM_DONE, "finished waiting for ME response"}, | |||
| /* FSP related timestamps */ | |||
| { TS_FSP_MEMORY_INIT_START, "calling FspMemoryInit" }, | |||
| { TS_FSP_MEMORY_INIT_END, "returning from FspMemoryInit" }, | |||
| { TS_FSP_TEMP_RAM_EXIT_START, "calling FspTempRamExit" }, | |||
| { TS_FSP_TEMP_RAM_EXIT_END, "returning from FspTempRamExit" }, | |||
| { TS_FSP_SILICON_INIT_START, "calling FspSiliconInit" }, | |||
| { TS_FSP_SILICON_INIT_END, "returning from FspSiliconInit" }, | |||
| { TS_FSP_BEFORE_ENUMERATE, "calling FspNotify(AfterPciEnumeration)" }, | |||
| { TS_FSP_AFTER_ENUMERATE, | |||
| "returning from FspNotify(AfterPciEnumeration)" }, | |||
| { TS_FSP_BEFORE_FINALIZE, "calling FspNotify(ReadyToBoot)" }, | |||
| { TS_FSP_AFTER_FINALIZE, "returning from FspNotify(ReadyToBoot)" }, | |||
| { TS_FSP_BEFORE_END_OF_FIRMWARE, "calling FspNotify(EndOfFirmware)" }, | |||
| { TS_FSP_AFTER_END_OF_FIRMWARE, | |||
| "returning from FspNotify(EndOfFirmware)" }, | |||
| }; | |||
| #endif | |||
+ 50
- 0
t430/util/functions.sh
View File
| @ -0,0 +1,50 @@ | |||
| #!/bin/bash | |||
| # SPDX-License-Identifier: GPL-3.0+ | |||
| # Copyright (C) 2018, Martin Kepplinger <martink@posteo.de> | |||
| RED='\033[0;31m' | |||
| GREEN='\033[0;32m' | |||
| YELLOW='\033[0;33m' | |||
| NC='\033[0m' | |||
| force_t430_and_root() | |||
| { | |||
| command -v dmidecode >/dev/null 2>&1 || { echo -e >&2 "${RED}Please install dmidecode and run as root.${NC}"; exit 1; } | |||
| local LAPTOP=$(dmidecode | grep -i t430 | sort -u) | |||
| if [ -z "$LAPTOP" ] ; then | |||
| echo "This is no Thinkpad T430. This script is useless then." | |||
| exit 0 | |||
| fi | |||
| } | |||
| check_battery() { | |||
| local capacity=$(cat /sys/class/power_supply/BAT*/capacity 2>/dev/null || echo -ne "0") | |||
| local online=$(cat /sys/class/power_supply/AC/online 2>/dev/null || cat /sys/class/power_supply/ADP*/online 2>/dev/null || echo -ne "0") | |||
| local failed=0 | |||
| if [ "${online}" == "0" ] ; then | |||
| failed=1 | |||
| fi | |||
| if [ "${capacity}" -lt 25 ]; then | |||
| failed=1 | |||
| fi | |||
| if [ $failed == "1" ]; then | |||
| echo -e "${YELLOW}WARNING:${NC} To prevent shutdowns, we recommend to only run this script when" | |||
| echo " your laptop is plugged in to the power supply AND" | |||
| echo " the battery is present and sufficiently charged (over 25%)." | |||
| while true; do | |||
| read -r -p "Continue anyways? (please do NOT!) y/N: " yn | |||
| case $yn in | |||
| [Yy]* ) break;; | |||
| [Nn]* ) exit;; | |||
| * ) exit;; | |||
| esac | |||
| done | |||
| fi | |||
| } | |||
| warn_not_root() { | |||
| if [[ $EUID -eq 0 ]]; then | |||
| echo -e "${YELLOW}WARNING:${NC} This should not be executed as root!" | |||
| fi | |||
| } | |||
+ 1
- 0
t430/util/ifdtool/.dependencies
View File
| @ -0,0 +1 @@ | |||
| ifdtool.o: ifdtool.c ../commonlib/include/commonlib/helpers.h ifdtool.h | |||
+ 45
- 0
t430/util/ifdtool/Makefile
View File
| @ -0,0 +1,45 @@ | |||
| # | |||
| # ifdtool - dump Intel Firmware Descriptor information | |||
| # | |||
| # Copyright (C) 2011 The ChromiumOS Authors. All rights reserved. | |||
| # | |||
| # This program is free software; you can redistribute it and/or modify | |||
| # it under the terms of the GNU General Public License as published by | |||
| # the Free Software Foundation; version 2 of the License. | |||
| # | |||
| # This program is distributed in the hope that it will be useful, | |||
| # but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| # MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| # GNU General Public License for more details. | |||
| # | |||
| PROGRAM = ifdtool | |||
| CC = gcc | |||
| INSTALL = /usr/bin/install | |||
| PREFIX = /usr/local | |||
| CFLAGS = -O2 -g -Wall -W -Werror -I../commonlib/include | |||
| LDFLAGS = | |||
| OBJS = ifdtool.o | |||
| all: dep $(PROGRAM) | |||
| $(PROGRAM): $(OBJS) | |||
| $(CC) -o $(PROGRAM) $(OBJS) $(LDFLAGS) | |||
| clean: | |||
| rm -f $(PROGRAM) *.o *~ .dependencies | |||
| distclean: clean | |||
| dep: | |||
| @$(CC) $(CFLAGS) -MM *.c > .dependencies | |||
| %.o: %.c | |||
| $(CC) $(CFLAGS) -c -o $@ $< | |||
| install: $(PROGRAM) | |||
| mkdir -p $(DESTDIR)$(PREFIX)/bin | |||
| $(INSTALL) $(PROGRAM) $(DESTDIR)$(PREFIX)/bin | |||
| .PHONY: all clean distclean dep | |||
BIN
t430/util/ifdtool/ifdtool
View File
+ 1491
- 0
t430/util/ifdtool/ifdtool.c
File diff suppressed because it is too large
View File
+ 127
- 0
t430/util/ifdtool/ifdtool.h
View File
| @ -0,0 +1,127 @@ | |||
| /* | |||
| * ifdtool - dump Intel Firmware Descriptor information | |||
| * | |||
| * Copyright (C) 2011 The ChromiumOS Authors. All rights reserved. | |||
| * | |||
| * This program is free software; you can redistribute it and/or modify | |||
| * it under the terms of the GNU General Public License as published by | |||
| * the Free Software Foundation; version 2 of the License. | |||
| * | |||
| * This program is distributed in the hope that it will be useful, | |||
| * but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| * GNU General Public License for more details. | |||
| */ | |||
| #include <stdint.h> | |||
| #define IFDTOOL_VERSION "1.2" | |||
| enum ifd_version { | |||
| IFD_VERSION_1, | |||
| IFD_VERSION_2, | |||
| }; | |||
| enum platform { | |||
| PLATFORM_APL, | |||
| PLATFORM_CNL, | |||
| PLATFORM_GLK, | |||
| PLATFORM_SKLKBL, | |||
| }; | |||
| #define LAYOUT_LINELEN 80 | |||
| enum spi_frequency { | |||
| SPI_FREQUENCY_20MHZ = 0, | |||
| SPI_FREQUENCY_33MHZ = 1, | |||
| SPI_FREQUENCY_48MHZ = 2, | |||
| SPI_FREQUENCY_50MHZ_30MHZ = 4, | |||
| SPI_FREQUENCY_17MHZ = 6, | |||
| }; | |||
| enum component_density { | |||
| COMPONENT_DENSITY_512KB = 0, | |||
| COMPONENT_DENSITY_1MB = 1, | |||
| COMPONENT_DENSITY_2MB = 2, | |||
| COMPONENT_DENSITY_4MB = 3, | |||
| COMPONENT_DENSITY_8MB = 4, | |||
| COMPONENT_DENSITY_16MB = 5, | |||
| COMPONENT_DENSITY_32MB = 6, | |||
| COMPONENT_DENSITY_64MB = 7, | |||
| COMPONENT_DENSITY_UNUSED = 0xf | |||
| }; | |||
| // flash descriptor | |||
| typedef struct { | |||
| uint32_t flvalsig; | |||
| uint32_t flmap0; | |||
| uint32_t flmap1; | |||
| uint32_t flmap2; | |||
| uint8_t reserved[0xefc - 0x20]; | |||
| uint32_t flumap1; | |||
| } __attribute__((packed)) fdbar_t; | |||
| // regions | |||
| #define MAX_REGIONS 9 | |||
| #define MAX_REGIONS_OLD 5 | |||
| typedef struct { | |||
| uint32_t flreg[MAX_REGIONS]; | |||
| } __attribute__((packed)) frba_t; | |||
| // component section | |||
| typedef struct { | |||
| uint32_t flcomp; | |||
| uint32_t flill; | |||
| uint32_t flpb; | |||
| } __attribute__((packed)) fcba_t; | |||
| // pch strap | |||
| #define MAX_PCHSTRP 18 | |||
| typedef struct { | |||
| uint32_t pchstrp[MAX_PCHSTRP]; | |||
| } __attribute__((packed)) fpsba_t; | |||
| /* | |||
| * WR / RD bits start at different locations within the flmstr regs, but | |||
| * otherwise have identical meaning. | |||
| */ | |||
| #define FLMSTR_WR_SHIFT_V1 24 | |||
| #define FLMSTR_WR_SHIFT_V2 20 | |||
| #define FLMSTR_RD_SHIFT_V1 16 | |||
| #define FLMSTR_RD_SHIFT_V2 8 | |||
| // master | |||
| typedef struct { | |||
| uint32_t flmstr1; | |||
| uint32_t flmstr2; | |||
| uint32_t flmstr3; | |||
| uint32_t flmstr4; | |||
| uint32_t flmstr5; | |||
| } __attribute__((packed)) fmba_t; | |||
| // processor strap | |||
| typedef struct { | |||
| uint32_t data[8]; | |||
| } __attribute__((packed)) fmsba_t; | |||
| // ME VSCC | |||
| typedef struct { | |||
| uint32_t jid; | |||
| uint32_t vscc; | |||
| } vscc_t; | |||
| typedef struct { | |||
| // Actual number of entries specified in vtl | |||
| vscc_t entry[8]; | |||
| } vtba_t; | |||
| typedef struct { | |||
| int base, limit, size; | |||
| } region_t; | |||
| struct region_name { | |||
| const char *pretty; | |||
| const char *terse; | |||
| const char *filename; | |||
| }; | |||
BIN
t430/util/ifdtool/ifdtool.o
View File
+ 674
- 0
t430/util/me_cleaner/COPYING
View File
| @ -0,0 +1,674 @@ | |||
| GNU GENERAL PUBLIC LICENSE | |||
| Version 3, 29 June 2007 | |||
| Copyright (C) 2007 Free Software Foundation, Inc. <http://fsf.org/> | |||
| Everyone is permitted to copy and distribute verbatim copies | |||
| of this license document, but changing it is not allowed. | |||
| Preamble | |||
| The GNU General Public License is a free, copyleft license for | |||
| software and other kinds of works. | |||
| The licenses for most software and other practical works are designed | |||
| to take away your freedom to share and change the works. By contrast, | |||
| the GNU General Public License is intended to guarantee your freedom to | |||
| share and change all versions of a program--to make sure it remains free | |||
| software for all its users. We, the Free Software Foundation, use the | |||
| GNU General Public License for most of our software; it applies also to | |||
| any other work released this way by its authors. You can apply it to | |||
| your programs, too. | |||
| When we speak of free software, we are referring to freedom, not | |||
| price. Our General Public Licenses are designed to make sure that you | |||
| have the freedom to distribute copies of free software (and charge for | |||
| them if you wish), that you receive source code or can get it if you | |||
| want it, that you can change the software or use pieces of it in new | |||
| free programs, and that you know you can do these things. | |||
| To protect your rights, we need to prevent others from denying you | |||
| these rights or asking you to surrender the rights. Therefore, you have | |||
| certain responsibilities if you distribute copies of the software, or if | |||
| you modify it: responsibilities to respect the freedom of others. | |||
| For example, if you distribute copies of such a program, whether | |||
| gratis or for a fee, you must pass on to the recipients the same | |||
| freedoms that you received. You must make sure that they, too, receive | |||
| or can get the source code. And you must show them these terms so they | |||
| know their rights. | |||
| Developers that use the GNU GPL protect your rights with two steps: | |||
| (1) assert copyright on the software, and (2) offer you this License | |||
| giving you legal permission to copy, distribute and/or modify it. | |||
| For the developers' and authors' protection, the GPL clearly explains | |||
| that there is no warranty for this free software. For both users' and | |||
| authors' sake, the GPL requires that modified versions be marked as | |||
| changed, so that their problems will not be attributed erroneously to | |||
| authors of previous versions. | |||
| Some devices are designed to deny users access to install or run | |||
| modified versions of the software inside them, although the manufacturer | |||
| can do so. This is fundamentally incompatible with the aim of | |||
| protecting users' freedom to change the software. The systematic | |||
| pattern of such abuse occurs in the area of products for individuals to | |||
| use, which is precisely where it is most unacceptable. Therefore, we | |||
| have designed this version of the GPL to prohibit the practice for those | |||
| products. If such problems arise substantially in other domains, we | |||
| stand ready to extend this provision to those domains in future versions | |||
| of the GPL, as needed to protect the freedom of users. | |||
| Finally, every program is threatened constantly by software patents. | |||
| States should not allow patents to restrict development and use of | |||
| software on general-purpose computers, but in those that do, we wish to | |||
| avoid the special danger that patents applied to a free program could | |||
| make it effectively proprietary. To prevent this, the GPL assures that | |||
| patents cannot be used to render the program non-free. | |||
| The precise terms and conditions for copying, distribution and | |||
| modification follow. | |||
| TERMS AND CONDITIONS | |||
| 0. Definitions. | |||
| "This License" refers to version 3 of the GNU General Public License. | |||
| "Copyright" also means copyright-like laws that apply to other kinds of | |||
| works, such as semiconductor masks. | |||
| "The Program" refers to any copyrightable work licensed under this | |||
| License. Each licensee is addressed as "you". "Licensees" and | |||
| "recipients" may be individuals or organizations. | |||
| To "modify" a work means to copy from or adapt all or part of the work | |||
| in a fashion requiring copyright permission, other than the making of an | |||
| exact copy. The resulting work is called a "modified version" of the | |||
| earlier work or a work "based on" the earlier work. | |||
| A "covered work" means either the unmodified Program or a work based | |||
| on the Program. | |||
| To "propagate" a work means to do anything with it that, without | |||
| permission, would make you directly or secondarily liable for | |||
| infringement under applicable copyright law, except executing it on a | |||
| computer or modifying a private copy. Propagation includes copying, | |||
| distribution (with or without modification), making available to the | |||
| public, and in some countries other activities as well. | |||
| To "convey" a work means any kind of propagation that enables other | |||
| parties to make or receive copies. Mere interaction with a user through | |||
| a computer network, with no transfer of a copy, is not conveying. | |||
| An interactive user interface displays "Appropriate Legal Notices" | |||
| to the extent that it includes a convenient and prominently visible | |||
| feature that (1) displays an appropriate copyright notice, and (2) | |||
| tells the user that there is no warranty for the work (except to the | |||
| extent that warranties are provided), that licensees may convey the | |||
| work under this License, and how to view a copy of this License. If | |||
| the interface presents a list of user commands or options, such as a | |||
| menu, a prominent item in the list meets this criterion. | |||
| 1. Source Code. | |||
| The "source code" for a work means the preferred form of the work | |||
| for making modifications to it. "Object code" means any non-source | |||
| form of a work. | |||
| A "Standard Interface" means an interface that either is an official | |||
| standard defined by a recognized standards body, or, in the case of | |||
| interfaces specified for a particular programming language, one that | |||
| is widely used among developers working in that language. | |||
| The "System Libraries" of an executable work include anything, other | |||
| than the work as a whole, that (a) is included in the normal form of | |||
| packaging a Major Component, but which is not part of that Major | |||
| Component, and (b) serves only to enable use of the work with that | |||
| Major Component, or to implement a Standard Interface for which an | |||
| implementation is available to the public in source code form. A | |||
| "Major Component", in this context, means a major essential component | |||
| (kernel, window system, and so on) of the specific operating system | |||
| (if any) on which the executable work runs, or a compiler used to | |||
| produce the work, or an object code interpreter used to run it. | |||
| The "Corresponding Source" for a work in object code form means all | |||
| the source code needed to generate, install, and (for an executable | |||
| work) run the object code and to modify the work, including scripts to | |||
| control those activities. However, it does not include the work's | |||
| System Libraries, or general-purpose tools or generally available free | |||
| programs which are used unmodified in performing those activities but | |||
| which are not part of the work. For example, Corresponding Source | |||
| includes interface definition files associated with source files for | |||
| the work, and the source code for shared libraries and dynamically | |||
| linked subprograms that the work is specifically designed to require, | |||
| such as by intimate data communication or control flow between those | |||
| subprograms and other parts of the work. | |||
| The Corresponding Source need not include anything that users | |||
| can regenerate automatically from other parts of the Corresponding | |||
| Source. | |||
| The Corresponding Source for a work in source code form is that | |||
| same work. | |||
| 2. Basic Permissions. | |||
| All rights granted under this License are granted for the term of | |||
| copyright on the Program, and are irrevocable provided the stated | |||
| conditions are met. This License explicitly affirms your unlimited | |||
| permission to run the unmodified Program. The output from running a | |||
| covered work is covered by this License only if the output, given its | |||
| content, constitutes a covered work. This License acknowledges your | |||
| rights of fair use or other equivalent, as provided by copyright law. | |||
| You may make, run and propagate covered works that you do not | |||
| convey, without conditions so long as your license otherwise remains | |||
| in force. You may convey covered works to others for the sole purpose | |||
| of having them make modifications exclusively for you, or provide you | |||
| with facilities for running those works, provided that you comply with | |||
| the terms of this License in conveying all material for which you do | |||
| not control copyright. Those thus making or running the covered works | |||
| for you must do so exclusively on your behalf, under your direction | |||
| and control, on terms that prohibit them from making any copies of | |||
| your copyrighted material outside their relationship with you. | |||
| Conveying under any other circumstances is permitted solely under | |||
| the conditions stated below. Sublicensing is not allowed; section 10 | |||
| makes it unnecessary. | |||
| 3. Protecting Users' Legal Rights From Anti-Circumvention Law. | |||
| No covered work shall be deemed part of an effective technological | |||
| measure under any applicable law fulfilling obligations under article | |||
| 11 of the WIPO copyright treaty adopted on 20 December 1996, or | |||
| similar laws prohibiting or restricting circumvention of such | |||
| measures. | |||
| When you convey a covered work, you waive any legal power to forbid | |||
| circumvention of technological measures to the extent such circumvention | |||
| is effected by exercising rights under this License with respect to | |||
| the covered work, and you disclaim any intention to limit operation or | |||
| modification of the work as a means of enforcing, against the work's | |||
| users, your or third parties' legal rights to forbid circumvention of | |||
| technological measures. | |||
| 4. Conveying Verbatim Copies. | |||
| You may convey verbatim copies of the Program's source code as you | |||
| receive it, in any medium, provided that you conspicuously and | |||
| appropriately publish on each copy an appropriate copyright notice; | |||
| keep intact all notices stating that this License and any | |||
| non-permissive terms added in accord with section 7 apply to the code; | |||
| keep intact all notices of the absence of any warranty; and give all | |||
| recipients a copy of this License along with the Program. | |||
| You may charge any price or no price for each copy that you convey, | |||
| and you may offer support or warranty protection for a fee. | |||
| 5. Conveying Modified Source Versions. | |||
| You may convey a work based on the Program, or the modifications to | |||
| produce it from the Program, in the form of source code under the | |||
| terms of section 4, provided that you also meet all of these conditions: | |||
| a) The work must carry prominent notices stating that you modified | |||
| it, and giving a relevant date. | |||
| b) The work must carry prominent notices stating that it is | |||
| released under this License and any conditions added under section | |||
| 7. This requirement modifies the requirement in section 4 to | |||
| "keep intact all notices". | |||
| c) You must license the entire work, as a whole, under this | |||
| License to anyone who comes into possession of a copy. This | |||
| License will therefore apply, along with any applicable section 7 | |||
| additional terms, to the whole of the work, and all its parts, | |||
| regardless of how they are packaged. This License gives no | |||
| permission to license the work in any other way, but it does not | |||
| invalidate such permission if you have separately received it. | |||
| d) If the work has interactive user interfaces, each must display | |||
| Appropriate Legal Notices; however, if the Program has interactive | |||
| interfaces that do not display Appropriate Legal Notices, your | |||
| work need not make them do so. | |||
| A compilation of a covered work with other separate and independent | |||
| works, which are not by their nature extensions of the covered work, | |||
| and which are not combined with it such as to form a larger program, | |||
| in or on a volume of a storage or distribution medium, is called an | |||
| "aggregate" if the compilation and its resulting copyright are not | |||
| used to limit the access or legal rights of the compilation's users | |||
| beyond what the individual works permit. Inclusion of a covered work | |||
| in an aggregate does not cause this License to apply to the other | |||
| parts of the aggregate. | |||
| 6. Conveying Non-Source Forms. | |||
| You may convey a covered work in object code form under the terms | |||
| of sections 4 and 5, provided that you also convey the | |||
| machine-readable Corresponding Source under the terms of this License, | |||
| in one of these ways: | |||
| a) Convey the object code in, or embodied in, a physical product | |||
| (including a physical distribution medium), accompanied by the | |||
| Corresponding Source fixed on a durable physical medium | |||
| customarily used for software interchange. | |||
| b) Convey the object code in, or embodied in, a physical product | |||
| (including a physical distribution medium), accompanied by a | |||
| written offer, valid for at least three years and valid for as | |||
| long as you offer spare parts or customer support for that product | |||
| model, to give anyone who possesses the object code either (1) a | |||
| copy of the Corresponding Source for all the software in the | |||
| product that is covered by this License, on a durable physical | |||
| medium customarily used for software interchange, for a price no | |||
| more than your reasonable cost of physically performing this | |||
| conveying of source, or (2) access to copy the | |||
| Corresponding Source from a network server at no charge. | |||
| c) Convey individual copies of the object code with a copy of the | |||
| written offer to provide the Corresponding Source. This | |||
| alternative is allowed only occasionally and noncommercially, and | |||
| only if you received the object code with such an offer, in accord | |||
| with subsection 6b. | |||
| d) Convey the object code by offering access from a designated | |||
| place (gratis or for a charge), and offer equivalent access to the | |||
| Corresponding Source in the same way through the same place at no | |||
| further charge. You need not require recipients to copy the | |||
| Corresponding Source along with the object code. If the place to | |||
| copy the object code is a network server, the Corresponding Source | |||
| may be on a different server (operated by you or a third party) | |||
| that supports equivalent copying facilities, provided you maintain | |||
| clear directions next to the object code saying where to find the | |||
| Corresponding Source. Regardless of what server hosts the | |||
| Corresponding Source, you remain obligated to ensure that it is | |||
| available for as long as needed to satisfy these requirements. | |||
| e) Convey the object code using peer-to-peer transmission, provided | |||
| you inform other peers where the object code and Corresponding | |||
| Source of the work are being offered to the general public at no | |||
| charge under subsection 6d. | |||
| A separable portion of the object code, whose source code is excluded | |||
| from the Corresponding Source as a System Library, need not be | |||
| included in conveying the object code work. | |||
| A "User Product" is either (1) a "consumer product", which means any | |||
| tangible personal property which is normally used for personal, family, | |||
| or household purposes, or (2) anything designed or sold for incorporation | |||
| into a dwelling. In determining whether a product is a consumer product, | |||
| doubtful cases shall be resolved in favor of coverage. For a particular | |||
| product received by a particular user, "normally used" refers to a | |||
| typical or common use of that class of product, regardless of the status | |||
| of the particular user or of the way in which the particular user | |||
| actually uses, or expects or is expected to use, the product. A product | |||
| is a consumer product regardless of whether the product has substantial | |||
| commercial, industrial or non-consumer uses, unless such uses represent | |||
| the only significant mode of use of the product. | |||
| "Installation Information" for a User Product means any methods, | |||
| procedures, authorization keys, or other information required to install | |||
| and execute modified versions of a covered work in that User Product from | |||
| a modified version of its Corresponding Source. The information must | |||
| suffice to ensure that the continued functioning of the modified object | |||
| code is in no case prevented or interfered with solely because | |||
| modification has been made. | |||
| If you convey an object code work under this section in, or with, or | |||
| specifically for use in, a User Product, and the conveying occurs as | |||
| part of a transaction in which the right of possession and use of the | |||
| User Product is transferred to the recipient in perpetuity or for a | |||
| fixed term (regardless of how the transaction is characterized), the | |||
| Corresponding Source conveyed under this section must be accompanied | |||
| by the Installation Information. But this requirement does not apply | |||
| if neither you nor any third party retains the ability to install | |||
| modified object code on the User Product (for example, the work has | |||
| been installed in ROM). | |||
| The requirement to provide Installation Information does not include a | |||
| requirement to continue to provide support service, warranty, or updates | |||
| for a work that has been modified or installed by the recipient, or for | |||
| the User Product in which it has been modified or installed. Access to a | |||
| network may be denied when the modification itself materially and | |||
| adversely affects the operation of the network or violates the rules and | |||
| protocols for communication across the network. | |||
| Corresponding Source conveyed, and Installation Information provided, | |||
| in accord with this section must be in a format that is publicly | |||
| documented (and with an implementation available to the public in | |||
| source code form), and must require no special password or key for | |||
| unpacking, reading or copying. | |||
| 7. Additional Terms. | |||
| "Additional permissions" are terms that supplement the terms of this | |||
| License by making exceptions from one or more of its conditions. | |||
| Additional permissions that are applicable to the entire Program shall | |||
| be treated as though they were included in this License, to the extent | |||
| that they are valid under applicable law. If additional permissions | |||
| apply only to part of the Program, that part may be used separately | |||
| under those permissions, but the entire Program remains governed by | |||
| this License without regard to the additional permissions. | |||
| When you convey a copy of a covered work, you may at your option | |||
| remove any additional permissions from that copy, or from any part of | |||
| it. (Additional permissions may be written to require their own | |||
| removal in certain cases when you modify the work.) You may place | |||
| additional permissions on material, added by you to a covered work, | |||
| for which you have or can give appropriate copyright permission. | |||
| Notwithstanding any other provision of this License, for material you | |||
| add to a covered work, you may (if authorized by the copyright holders of | |||
| that material) supplement the terms of this License with terms: | |||
| a) Disclaiming warranty or limiting liability differently from the | |||
| terms of sections 15 and 16 of this License; or | |||
| b) Requiring preservation of specified reasonable legal notices or | |||
| author attributions in that material or in the Appropriate Legal | |||
| Notices displayed by works containing it; or | |||
| c) Prohibiting misrepresentation of the origin of that material, or | |||
| requiring that modified versions of such material be marked in | |||
| reasonable ways as different from the original version; or | |||
| d) Limiting the use for publicity purposes of names of licensors or | |||
| authors of the material; or | |||
| e) Declining to grant rights under trademark law for use of some | |||
| trade names, trademarks, or service marks; or | |||
| f) Requiring indemnification of licensors and authors of that | |||
| material by anyone who conveys the material (or modified versions of | |||
| it) with contractual assumptions of liability to the recipient, for | |||
| any liability that these contractual assumptions directly impose on | |||
| those licensors and authors. | |||
| All other non-permissive additional terms are considered "further | |||
| restrictions" within the meaning of section 10. If the Program as you | |||
| received it, or any part of it, contains a notice stating that it is | |||
| governed by this License along with a term that is a further | |||
| restriction, you may remove that term. If a license document contains | |||
| a further restriction but permits relicensing or conveying under this | |||
| License, you may add to a covered work material governed by the terms | |||
| of that license document, provided that the further restriction does | |||
| not survive such relicensing or conveying. | |||
| If you add terms to a covered work in accord with this section, you | |||
| must place, in the relevant source files, a statement of the | |||
| additional terms that apply to those files, or a notice indicating | |||
| where to find the applicable terms. | |||
| Additional terms, permissive or non-permissive, may be stated in the | |||
| form of a separately written license, or stated as exceptions; | |||
| the above requirements apply either way. | |||
| 8. Termination. | |||
| You may not propagate or modify a covered work except as expressly | |||
| provided under this License. Any attempt otherwise to propagate or | |||
| modify it is void, and will automatically terminate your rights under | |||
| this License (including any patent licenses granted under the third | |||
| paragraph of section 11). | |||
| However, if you cease all violation of this License, then your | |||
| license from a particular copyright holder is reinstated (a) | |||
| provisionally, unless and until the copyright holder explicitly and | |||
| finally terminates your license, and (b) permanently, if the copyright | |||
| holder fails to notify you of the violation by some reasonable means | |||
| prior to 60 days after the cessation. | |||
| Moreover, your license from a particular copyright holder is | |||
| reinstated permanently if the copyright holder notifies you of the | |||
| violation by some reasonable means, this is the first time you have | |||
| received notice of violation of this License (for any work) from that | |||
| copyright holder, and you cure the violation prior to 30 days after | |||
| your receipt of the notice. | |||
| Termination of your rights under this section does not terminate the | |||
| licenses of parties who have received copies or rights from you under | |||
| this License. If your rights have been terminated and not permanently | |||
| reinstated, you do not qualify to receive new licenses for the same | |||
| material under section 10. | |||
| 9. Acceptance Not Required for Having Copies. | |||
| You are not required to accept this License in order to receive or | |||
| run a copy of the Program. Ancillary propagation of a covered work | |||
| occurring solely as a consequence of using peer-to-peer transmission | |||
| to receive a copy likewise does not require acceptance. However, | |||
| nothing other than this License grants you permission to propagate or | |||
| modify any covered work. These actions infringe copyright if you do | |||
| not accept this License. Therefore, by modifying or propagating a | |||
| covered work, you indicate your acceptance of this License to do so. | |||
| 10. Automatic Licensing of Downstream Recipients. | |||
| Each time you convey a covered work, the recipient automatically | |||
| receives a license from the original licensors, to run, modify and | |||
| propagate that work, subject to this License. You are not responsible | |||
| for enforcing compliance by third parties with this License. | |||
| An "entity transaction" is a transaction transferring control of an | |||
| organization, or substantially all assets of one, or subdividing an | |||
| organization, or merging organizations. If propagation of a covered | |||
| work results from an entity transaction, each party to that | |||
| transaction who receives a copy of the work also receives whatever | |||
| licenses to the work the party's predecessor in interest had or could | |||
| give under the previous paragraph, plus a right to possession of the | |||
| Corresponding Source of the work from the predecessor in interest, if | |||
| the predecessor has it or can get it with reasonable efforts. | |||
| You may not impose any further restrictions on the exercise of the | |||
| rights granted or affirmed under this License. For example, you may | |||
| not impose a license fee, royalty, or other charge for exercise of | |||
| rights granted under this License, and you may not initiate litigation | |||
| (including a cross-claim or counterclaim in a lawsuit) alleging that | |||
| any patent claim is infringed by making, using, selling, offering for | |||
| sale, or importing the Program or any portion of it. | |||
| 11. Patents. | |||
| A "contributor" is a copyright holder who authorizes use under this | |||
| License of the Program or a work on which the Program is based. The | |||
| work thus licensed is called the contributor's "contributor version". | |||
| A contributor's "essential patent claims" are all patent claims | |||
| owned or controlled by the contributor, whether already acquired or | |||
| hereafter acquired, that would be infringed by some manner, permitted | |||
| by this License, of making, using, or selling its contributor version, | |||
| but do not include claims that would be infringed only as a | |||
| consequence of further modification of the contributor version. For | |||
| purposes of this definition, "control" includes the right to grant | |||
| patent sublicenses in a manner consistent with the requirements of | |||
| this License. | |||
| Each contributor grants you a non-exclusive, worldwide, royalty-free | |||
| patent license under the contributor's essential patent claims, to | |||
| make, use, sell, offer for sale, import and otherwise run, modify and | |||
| propagate the contents of its contributor version. | |||
| In the following three paragraphs, a "patent license" is any express | |||
| agreement or commitment, however denominated, not to enforce a patent | |||
| (such as an express permission to practice a patent or covenant not to | |||
| sue for patent infringement). To "grant" such a patent license to a | |||
| party means to make such an agreement or commitment not to enforce a | |||
| patent against the party. | |||
| If you convey a covered work, knowingly relying on a patent license, | |||
| and the Corresponding Source of the work is not available for anyone | |||
| to copy, free of charge and under the terms of this License, through a | |||
| publicly available network server or other readily accessible means, | |||
| then you must either (1) cause the Corresponding Source to be so | |||
| available, or (2) arrange to deprive yourself of the benefit of the | |||
| patent license for this particular work, or (3) arrange, in a manner | |||
| consistent with the requirements of this License, to extend the patent | |||
| license to downstream recipients. "Knowingly relying" means you have | |||
| actual knowledge that, but for the patent license, your conveying the | |||
| covered work in a country, or your recipient's use of the covered work | |||
| in a country, would infringe one or more identifiable patents in that | |||
| country that you have reason to believe are valid. | |||
| If, pursuant to or in connection with a single transaction or | |||
| arrangement, you convey, or propagate by procuring conveyance of, a | |||
| covered work, and grant a patent license to some of the parties | |||
| receiving the covered work authorizing them to use, propagate, modify | |||
| or convey a specific copy of the covered work, then the patent license | |||
| you grant is automatically extended to all recipients of the covered | |||
| work and works based on it. | |||
| A patent license is "discriminatory" if it does not include within | |||
| the scope of its coverage, prohibits the exercise of, or is | |||
| conditioned on the non-exercise of one or more of the rights that are | |||
| specifically granted under this License. You may not convey a covered | |||
| work if you are a party to an arrangement with a third party that is | |||
| in the business of distributing software, under which you make payment | |||
| to the third party based on the extent of your activity of conveying | |||
| the work, and under which the third party grants, to any of the | |||
| parties who would receive the covered work from you, a discriminatory | |||
| patent license (a) in connection with copies of the covered work | |||
| conveyed by you (or copies made from those copies), or (b) primarily | |||
| for and in connection with specific products or compilations that | |||
| contain the covered work, unless you entered into that arrangement, | |||
| or that patent license was granted, prior to 28 March 2007. | |||
| Nothing in this License shall be construed as excluding or limiting | |||
| any implied license or other defenses to infringement that may | |||
| otherwise be available to you under applicable patent law. | |||
| 12. No Surrender of Others' Freedom. | |||
| If conditions are imposed on you (whether by court order, agreement or | |||
| otherwise) that contradict the conditions of this License, they do not | |||
| excuse you from the conditions of this License. If you cannot convey a | |||
| covered work so as to satisfy simultaneously your obligations under this | |||
| License and any other pertinent obligations, then as a consequence you may | |||
| not convey it at all. For example, if you agree to terms that obligate you | |||
| to collect a royalty for further conveying from those to whom you convey | |||
| the Program, the only way you could satisfy both those terms and this | |||
| License would be to refrain entirely from conveying the Program. | |||
| 13. Use with the GNU Affero General Public License. | |||
| Notwithstanding any other provision of this License, you have | |||
| permission to link or combine any covered work with a work licensed | |||
| under version 3 of the GNU Affero General Public License into a single | |||
| combined work, and to convey the resulting work. The terms of this | |||
| License will continue to apply to the part which is the covered work, | |||
| but the special requirements of the GNU Affero General Public License, | |||
| section 13, concerning interaction through a network will apply to the | |||
| combination as such. | |||
| 14. Revised Versions of this License. | |||
| The Free Software Foundation may publish revised and/or new versions of | |||
| the GNU General Public License from time to time. Such new versions will | |||
| be similar in spirit to the present version, but may differ in detail to | |||
| address new problems or concerns. | |||
| Each version is given a distinguishing version number. If the | |||
| Program specifies that a certain numbered version of the GNU General | |||
| Public License "or any later version" applies to it, you have the | |||
| option of following the terms and conditions either of that numbered | |||
| version or of any later version published by the Free Software | |||
| Foundation. If the Program does not specify a version number of the | |||
| GNU General Public License, you may choose any version ever published | |||
| by the Free Software Foundation. | |||
| If the Program specifies that a proxy can decide which future | |||
| versions of the GNU General Public License can be used, that proxy's | |||
| public statement of acceptance of a version permanently authorizes you | |||
| to choose that version for the Program. | |||
| Later license versions may give you additional or different | |||
| permissions. However, no additional obligations are imposed on any | |||
| author or copyright holder as a result of your choosing to follow a | |||
| later version. | |||
| 15. Disclaimer of Warranty. | |||
| THERE IS NO WARRANTY FOR THE PROGRAM, TO THE EXTENT PERMITTED BY | |||
| APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED IN WRITING THE COPYRIGHT | |||
| HOLDERS AND/OR OTHER PARTIES PROVIDE THE PROGRAM "AS IS" WITHOUT WARRANTY | |||
| OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, | |||
| THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR | |||
| PURPOSE. THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE PROGRAM | |||
| IS WITH YOU. SHOULD THE PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF | |||
| ALL NECESSARY SERVICING, REPAIR OR CORRECTION. | |||
| 16. Limitation of Liability. | |||
| IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING | |||
| WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MODIFIES AND/OR CONVEYS | |||
| THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY | |||
| GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE | |||
| USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED TO LOSS OF | |||
| DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD | |||
| PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER PROGRAMS), | |||
| EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF | |||
| SUCH DAMAGES. | |||
| 17. Interpretation of Sections 15 and 16. | |||
| If the disclaimer of warranty and limitation of liability provided | |||
| above cannot be given local legal effect according to their terms, | |||
| reviewing courts shall apply local law that most closely approximates | |||
| an absolute waiver of all civil liability in connection with the | |||
| Program, unless a warranty or assumption of liability accompanies a | |||
| copy of the Program in return for a fee. | |||
| END OF TERMS AND CONDITIONS | |||
| How to Apply These Terms to Your New Programs | |||
| If you develop a new program, and you want it to be of the greatest | |||
| possible use to the public, the best way to achieve this is to make it | |||
| free software which everyone can redistribute and change under these terms. | |||
| To do so, attach the following notices to the program. It is safest | |||
| to attach them to the start of each source file to most effectively | |||
| state the exclusion of warranty; and each file should have at least | |||
| the "copyright" line and a pointer to where the full notice is found. | |||
| <one line to give the program's name and a brief idea of what it does.> | |||
| Copyright (C) <year> <name of author> | |||
| This program is free software: you can redistribute it and/or modify | |||
| it under the terms of the GNU General Public License as published by | |||
| the Free Software Foundation, either version 3 of the License, or | |||
| (at your option) any later version. | |||
| This program is distributed in the hope that it will be useful, | |||
| but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| GNU General Public License for more details. | |||
| You should have received a copy of the GNU General Public License | |||
| along with this program. If not, see <http://www.gnu.org/licenses/>. | |||
| Also add information on how to contact you by electronic and paper mail. | |||
| If the program does terminal interaction, make it output a short | |||
| notice like this when it starts in an interactive mode: | |||
| <program> Copyright (C) <year> <name of author> | |||
| This program comes with ABSOLUTELY NO WARRANTY; for details type `show w'. | |||
| This is free software, and you are welcome to redistribute it | |||
| under certain conditions; type `show c' for details. | |||
| The hypothetical commands `show w' and `show c' should show the appropriate | |||
| parts of the General Public License. Of course, your program's commands | |||
| might be different; for a GUI interface, you would use an "about box". | |||
| You should also get your employer (if you work as a programmer) or school, | |||
| if any, to sign a "copyright disclaimer" for the program, if necessary. | |||
| For more information on this, and how to apply and follow the GNU GPL, see | |||
| <http://www.gnu.org/licenses/>. | |||
| The GNU General Public License does not permit incorporating your program | |||
| into proprietary programs. If your program is a subroutine library, you | |||
| may consider it more useful to permit linking proprietary applications with | |||
| the library. If this is what you want to do, use the GNU Lesser General | |||
| Public License instead of this License. But first, please read | |||
| <http://www.gnu.org/philosophy/why-not-lgpl.html>. | |||
+ 86
- 0
t430/util/me_cleaner/README.md
View File
| @ -0,0 +1,86 @@ | |||
| # me\_cleaner [](https://www.paypal.com/cgi-bin/webscr?cmd=_s-xclick&hosted_button_id=B5HCXCLZVCVZ8) | |||
| _me\_cleaner_ is a Python script able to modify an Intel ME firmware image with | |||
| the final purpose of reducing its ability to interact with the system. | |||
| ## Intel ME | |||
| Intel ME is a co-processor integrated in all post-2006 Intel boards, which is | |||
| the base hardware for many Intel features like Intel AMT, Intel Boot Guard, | |||
| Intel PAVP and many others. To provide such features, it requires full access to | |||
| the system, including memory (through DMA) and network access (transparent to | |||
| the user). | |||
| Unlike many other firmware components, the Intel ME firmware can't be neither | |||
| disabled nor reimplemented, as it is tightly integrated in the boot process and | |||
| it is signed. | |||
| This poses an issue both to the free firmware implementations like [coreboot]( | |||
| https://www.coreboot.org/), which are forced to rely on a proprietary, obscure | |||
| and always-on blob, and to the privacy-aware users, who are reasonably worried | |||
| about such firmware, running on the lowest privilege ring on x86. | |||
| ## What can be done | |||
| Before Nehalem (ME version 6, 2008/2009) the ME firmware could be removed | |||
| completely from the flash chip by setting a couple of bits inside the flash | |||
| descriptor, effectively disabling it. | |||
| Starting from Nehalem the Intel ME firmware can't be removed anymore: without a | |||
| valid firmware the PC shuts off forcefully after 30 minutes, probably as an | |||
| attempt to enforce the Intel Anti-Theft policies. | |||
| However, while Intel ME can't be turned off completely, it is still possible to | |||
| modify its firmware up to a point where Intel ME is active only during the boot | |||
| process, effectively disabling it during the normal operation, which is what | |||
| _me\_cleaner_ tries to accomplish. | |||
| ## Platform support | |||
| _me\_cleaner_ currently works on [most of the Intel platforms]( | |||
| https://github.com/corna/me_cleaner/wiki/me_cleaner-status); while this doesn't | |||
| mean it works on all the boards (due to the different firmware implementations), | |||
| it has been proven quite reliable on a great number of them. | |||
| ## Usage | |||
| _me\_cleaner_ should handle all the steps necessary to the modification of an | |||
| Intel ME firmware with the command: | |||
| $ python me_cleaner.py -S -O modified_image.bin original_dump.bin | |||
| However, obtaining the original firmware and flashing back the modified one is | |||
| usually not trivial, as the Intel ME firmware region is often non-writable from | |||
| the OS (and it's not a safe option anyways), requiring the use of an external | |||
| SPI programmer. | |||
| ## Results | |||
| For pre-Skylake firmware (ME version < 11) this tool removes almost everything, | |||
| leaving only the two fundamental modules needed for the correct boot, `ROMP` and | |||
| `BUP`. The code size is reduced from 1.5 MB (non-AMT firmware) or 5 MB (AMT | |||
| firmware) to ~90 kB of compressed code. | |||
| Starting from Skylake (ME version >= 11) the ME subsystem and the firmware | |||
| structure have changed, requiring substantial changes in _me\_cleaner_. | |||
| The fundamental modules required for the correct boot are now four (`rbe`, | |||
| `kernel`, `syslib` and `bup`) and the minimum code size is ~300 kB of compressed | |||
| code (from the 2 MB of the non-AMT firmware and the 7 MB of the AMT one). | |||
| On some boards the OEM firmware fails to boot without a valid Intel ME firmware; | |||
| in the other cases the system should work with minor inconveniences (like longer | |||
| boot times or warning messages) or without issues at all. | |||
| Obviously, the features provided by Intel ME won't be functional anymore after | |||
| the modifications. | |||
| ## Documentation | |||
| The detailed documentation about the working of _me\_cleaner_ can be found on | |||
| the page ["How does it work?" page]( | |||
| https://github.com/corna/me_cleaner/wiki/How-does-it-work%3F). | |||
| Various guides and tutorials are available on the Internet, however a good | |||
| starting point is the ["How to apply me_cleaner" guide]( | |||
| https://github.com/corna/me_cleaner/wiki/How-to-apply-me_cleaner). | |||
+ 159
- 0
t430/util/me_cleaner/man/me_cleaner.1
View File
| @ -0,0 +1,159 @@ | |||
| .TH me_cleaner 1 "MARCH 2018" | |||
| .SH me_cleaner | |||
| .PP | |||
| me_cleaner \- Tool for partial deblobbing of Intel ME/TXE firmware images | |||
| .SH SYNOPSIS | |||
| .PP | |||
| \fB\fCme_cleaner.py\fR [\-h] [\-v] [\-O output_file] [\-S | \-s] [\-r] [\-k] | |||
| [\-w whitelist | \-b blacklist] [\-d] [\-t] [\-c] [\-D output_descriptor] | |||
| [\-M output_me_image] \fIfile\fP | |||
| .SH DESCRIPTION | |||
| .PP | |||
| \fB\fCme_cleaner\fR is a tool able to disable parts of Intel ME/TXE by: | |||
| .RS | |||
| .IP \(bu 2 | |||
| removing most of the code from its firmware | |||
| .IP \(bu 2 | |||
| setting a special bit to force it to disable itself after the hardware | |||
| initialization | |||
| .RE | |||
| .PP | |||
| Using both the modes seems to be the most reliable way on many platforms. | |||
| .PP | |||
| The resulting modified firmware needs to be flashed (in most of the cases) with | |||
| an external programmer, often a dedicated SPI programmer or a Linux board with | |||
| a SPI master interface. | |||
| .PP | |||
| \fB\fCme_cleaner\fR works at least from Nehalem to Coffee Lake (for Intel ME) and on | |||
| Braswell/Cherry Trail (for Intel TXE), but may work as well on newer or | |||
| different architectures. | |||
| .PP | |||
| While \fB\fCme_cleaner\fR have been tested on a great number of platforms, fiddling | |||
| with the Intel ME/TXE firmware is \fIvery dangerous\fP and can easily lead to a | |||
| dead PC. | |||
| .PP | |||
| \fIYOU HAVE BEEN WARNED.\fP | |||
| .SH POSITIONAL ARGUMENTS | |||
| .TP | |||
| \fB\fCfile\fR | |||
| ME/TXE image or full dump. | |||
| .SH OPTIONAL ARGUMENTS | |||
| .TP | |||
| \fB\fC\-h\fR, \fB\fC\-\-help\fR | |||
| Show the help message and exit. | |||
| .TP | |||
| \fB\fC\-v\fR, \fB\fC\-\-version\fR | |||
| Show program's version number and exit. | |||
| .TP | |||
| \fB\fC\-O\fR, \fB\fC\-\-output\fR | |||
| Save the modified image in a separate file, instead of modifying the | |||
| original file. | |||
| .TP | |||
| \fB\fC\-S\fR, \fB\fC\-\-soft\-disable\fR | |||
| In addition to the usual operations on the ME/TXE firmware, set the | |||
| MeAltDisable bit or the HAP bit to ask Intel ME/TXE to disable itself after | |||
| the hardware initialization (requires a full dump). | |||
| .TP | |||
| \fB\fC\-s\fR, \fB\fC\-\-soft\-disable\-only\fR | |||
| Instead of the usual operations on the ME/TXE firmware, just set the | |||
| MeAltDisable bit or the HAP bit to ask Intel ME/TXE to disable itself after | |||
| the hardware initialization (requires a full dump). | |||
| .TP | |||
| \fB\fC\-r\fR, \fB\fC\-\-relocate\fR | |||
| Relocate the FTPR partition to the top of the ME region to save even more | |||
| space. | |||
| .TP | |||
| \fB\fC\-t\fR, \fB\fC\-\-truncate\fR | |||
| Truncate the empty part of the firmware (requires a separated ME/TXE image or | |||
| \fB\fC\-\-extract\-me\fR). | |||
| .TP | |||
| \fB\fC\-k\fR, \fB\fC\-\-keep\-modules\fR | |||
| Don't remove the FTPR modules, even when possible. | |||
| .TP | |||
| \fB\fC\-w\fR, \fB\fC\-\-whitelist\fR | |||
| Comma separated list of additional partitions to keep in the final image. | |||
| This can be used to specify the MFS partition for example, which stores PCIe | |||
| and clock settings. | |||
| .TP | |||
| \fB\fC\-b\fR, \fB\fC\-\-blacklist\fR | |||
| Comma separated list of partitions to remove from the image. This option | |||
| overrides the default removal list. | |||
| .TP | |||
| \fB\fC\-d\fR, \fB\fC\-\-descriptor\fR | |||
| Remove the ME/TXE Read/Write permissions to the other regions on the flash | |||
| from the Intel Flash Descriptor (requires a full dump). | |||
| .TP | |||
| \fB\fC\-D\fR, \fB\fC\-\-extract\-descriptor\fR | |||
| Extract the flash descriptor from a full dump; when used with \fB\fC\-\-truncate\fR | |||
| save a descriptor with adjusted regions start and end. | |||
| .TP | |||
| \fB\fC\-M\fR, \fB\fC\-\-extract\-me\fR | |||
| Extract the ME firmware from a full dump; when used with \fB\fC\-\-truncate\fR save a | |||
| truncated ME/TXE image. | |||
| .TP | |||
| \fB\fC\-c\fR, \fB\fC\-\-check\fR | |||
| Verify the integrity of the fundamental parts of the firmware and exit. | |||
| .SH SUPPORTED PLATFORMS | |||
| .PP | |||
| Currently \fB\fCme_cleaner\fR has been tested on the following platforms: | |||
| .TS | |||
| allbox; | |||
| cb cb cb cb | |||
| c c c c | |||
| c c c c | |||
| c c c c | |||
| c c c c | |||
| c c c c | |||
| c c c c | |||
| c c c c | |||
| c c c c | |||
| . | |||
| PCH CPU ME SKU | |||
| Ibex Peak * Nehalem/Westmere 6.0 Ignition | |||
| Ibex Peak * Nehalem/Westmere 6.x 1.5/5 MB | |||
| Cougar Point Sandy Bridge 7.x 1.5/5 MB | |||
| Panther Point Ivy Bridge 8.x 1.5/5 MB | |||
| Lynx/Wildcat Point Haswell/Broadwell 9.x 1.5/5 MB | |||
| Wildcat Point LP Broadwell Mobile 10.0 1.5/5 MB | |||
| Sunrise Point Skylake/Kabylake 11.x CON/COR | |||
| Union Point Kabylake 11.x CON/COR | |||
| .TE | |||
| .TS | |||
| allbox; | |||
| cb cb cb | |||
| c c c | |||
| . | |||
| SoC TXE SKU | |||
| Braswell/Cherry Trail 2.x 1.375 MB | |||
| .TE | |||
| .PP | |||
| * Not working on coreboot | |||
| .PP | |||
| All the reports are available on the project's GitHub page \[la]https://github.com/corna/me_cleaner/issues/3\[ra]\&. | |||
| .SH EXAMPLES | |||
| .PP | |||
| Check whether the provided image has a valid structure and signature: | |||
| .IP | |||
| \fB\fCme_cleaner.py \-c dumped_firmware.bin\fR | |||
| .PP | |||
| Remove most of the Intel ME firmware modules but don't set the HAP/AltMeDisable | |||
| bit: | |||
| .IP | |||
| \fB\fCme_cleaner.py \-S \-O modified_me_firmware.bin dumped_firmware.bin\fR | |||
| .PP | |||
| Remove most of the Intel ME firmware modules and set the HAP/AltMeDisable bit, | |||
| disable the Read/Write access of Intel ME to the other flash region, then | |||
| relocate the code to the top of the image and truncate it, extracting a modified | |||
| descriptor and ME image: | |||
| .IP | |||
| \fB\fCme_cleaner.py \-S \-r \-t \-d \-D ifd_shrinked.bin \-M me_shrinked.bin \-O modified_firmware.bin full_dumped_firmware.bin\fR | |||
| .SH BUGS | |||
| .PP | |||
| Bugs should be reported on the project's GitHub page \[la]https://github.com/corna/me_cleaner\[ra]\&. | |||
| .SH AUTHOR | |||
| .PP | |||
| Nicola Corna \[la]nicola@corna.info\[ra] | |||
| .SH SEE ALSO | |||
| .PP | |||
| .BR flashrom (8), | |||
| me_cleaner's Wiki \[la]https://github.com/corna/me_cleaner/wiki\[ra] | |||
+ 166
- 0
t430/util/me_cleaner/man/me_cleaner.md
View File
| @ -0,0 +1,166 @@ | |||
| [//]: # (Use md2man to generate the man page from this Markdown) | |||
| [//]: # (https://github.com/sunaku/md2man) | |||
| me_cleaner 1 "MARCH 2018" | |||
| ======================================= | |||
| me\_cleaner | |||
| ---- | |||
| me\_cleaner - Tool for partial deblobbing of Intel ME/TXE firmware images | |||
| SYNOPSIS | |||
| -------- | |||
| `me_cleaner.py` [-h] [-v] [-O output\_file] [-S | -s] [-r] [-k] | |||
| [-w whitelist | -b blacklist] [-d] [-t] [-c] [-D output\_descriptor] | |||
| [-M output\_me\_image] *file* | |||
| DESCRIPTION | |||
| ----------- | |||
| `me_cleaner` is a tool able to disable parts of Intel ME/TXE by: | |||
| * removing most of the code from its firmware | |||
| * setting a special bit to force it to disable itself after the hardware | |||
| initialization | |||
| Using both the modes seems to be the most reliable way on many platforms. | |||
| The resulting modified firmware needs to be flashed (in most of the cases) with | |||
| an external programmer, often a dedicated SPI programmer or a Linux board with | |||
| a SPI master interface. | |||
| `me_cleaner` works at least from Nehalem to Coffee Lake (for Intel ME) and on | |||
| Braswell/Cherry Trail (for Intel TXE), but may work as well on newer or | |||
| different architectures. | |||
| While `me_cleaner` have been tested on a great number of platforms, fiddling | |||
| with the Intel ME/TXE firmware is *very dangerous* and can easily lead to a | |||
| dead PC. | |||
| *YOU HAVE BEEN WARNED.* | |||
| POSITIONAL ARGUMENTS | |||
| -------------------- | |||
| `file` | |||
| ME/TXE image or full dump. | |||
| OPTIONAL ARGUMENTS | |||
| ------------------ | |||
| `-h`, `--help` | |||
| Show the help message and exit. | |||
| `-v`, `--version` | |||
| Show program's version number and exit. | |||
| `-O`, `--output` | |||
| Save the modified image in a separate file, instead of modifying the | |||
| original file. | |||
| `-S`, `--soft-disable` | |||
| In addition to the usual operations on the ME/TXE firmware, set the | |||
| MeAltDisable bit or the HAP bit to ask Intel ME/TXE to disable itself after | |||
| the hardware initialization (requires a full dump). | |||
| `-s`, `--soft-disable-only` | |||
| Instead of the usual operations on the ME/TXE firmware, just set the | |||
| MeAltDisable bit or the HAP bit to ask Intel ME/TXE to disable itself after | |||
| the hardware initialization (requires a full dump). | |||
| `-r`, `--relocate` | |||
| Relocate the FTPR partition to the top of the ME region to save even more | |||
| space. | |||
| `-t`, `--truncate` | |||
| Truncate the empty part of the firmware (requires a separated ME/TXE image or | |||
| `--extract-me`). | |||
| `-k`, `--keep-modules` | |||
| Don't remove the FTPR modules, even when possible. | |||
| `-w`, `--whitelist` | |||
| Comma separated list of additional partitions to keep in the final image. | |||
| This can be used to specify the MFS partition for example, which stores PCIe | |||
| and clock settings. | |||
| `-b`, `--blacklist` | |||
| Comma separated list of partitions to remove from the image. This option | |||
| overrides the default removal list. | |||
| `-d`, `--descriptor` | |||
| Remove the ME/TXE Read/Write permissions to the other regions on the flash | |||
| from the Intel Flash Descriptor (requires a full dump). | |||
| `-D`, `--extract-descriptor` | |||
| Extract the flash descriptor from a full dump; when used with `--truncate` | |||
| save a descriptor with adjusted regions start and end. | |||
| `-M`, `--extract-me` | |||
| Extract the ME firmware from a full dump; when used with `--truncate` save a | |||
| truncated ME/TXE image. | |||
| `-c`, `--check` | |||
| Verify the integrity of the fundamental parts of the firmware and exit. | |||
| SUPPORTED PLATFORMS | |||
| ------------------- | |||
| Currently `me_cleaner` has been tested on the following platforms: | |||
| | PCH | CPU | ME | SKU | | |||
| |:-----------------:|:-----------------:|:----:|:--------:| | |||
| | Ibex Peak * | Nehalem/Westmere | 6.0 | Ignition | | |||
| | Ibex Peak * | Nehalem/Westmere | 6.x | 1.5/5 MB | | |||
| | Cougar Point | Sandy Bridge | 7.x | 1.5/5 MB | | |||
| | Panther Point | Ivy Bridge | 8.x | 1.5/5 MB | | |||
| | Lynx/Wildcat Point| Haswell/Broadwell | 9.x | 1.5/5 MB | | |||
| | Wildcat Point LP | Broadwell Mobile | 10.0 | 1.5/5 MB | | |||
| | Sunrise Point | Skylake/Kabylake | 11.x | CON/COR | | |||
| | Union Point | Kabylake | 11.x | CON/COR | | |||
| | SoC | TXE | SKU | | |||
| |:---------------------:|:---:|:--------:| | |||
| | Braswell/Cherry Trail | 2.x | 1.375 MB | | |||
| \* Not working on coreboot | |||
| All the reports are available on the [project's GitHub page]( | |||
| https://github.com/corna/me_cleaner/issues/3). | |||
| EXAMPLES | |||
| -------- | |||
| Check whether the provided image has a valid structure and signature: | |||
| `me_cleaner.py -c dumped_firmware.bin` | |||
| Remove most of the Intel ME firmware modules but don't set the HAP/AltMeDisable | |||
| bit: | |||
| `me_cleaner.py -S -O modified_me_firmware.bin dumped_firmware.bin` | |||
| Remove most of the Intel ME firmware modules and set the HAP/AltMeDisable bit, | |||
| disable the Read/Write access of Intel ME to the other flash region, then | |||
| relocate the code to the top of the image and truncate it, extracting a modified | |||
| descriptor and ME image: | |||
| `me_cleaner.py -S -r -t -d -D ifd_shrinked.bin -M me_shrinked.bin -O modified_firmware.bin full_dumped_firmware.bin` | |||
| BUGS | |||
| ---- | |||
| Bugs should be reported on the [project's GitHub page]( | |||
| https://github.com/corna/me_cleaner). | |||
| AUTHOR | |||
| ------ | |||
| Nicola Corna <nicola@corna.info> | |||
| SEE ALSO | |||
| -------- | |||
| flashrom(8), [me\_cleaner's Wiki](https://github.com/corna/me_cleaner/wiki) | |||
+ 897
- 0
t430/util/me_cleaner/me_cleaner.py
View File
| @ -0,0 +1,897 @@ | |||
| #!/usr/bin/python | |||
| # me_cleaner - Tool for partial deblobbing of Intel ME/TXE firmware images | |||
| # Copyright (C) 2016-2018 Nicola Corna <nicola@corna.info> | |||
| # | |||
| # This program is free software; you can redistribute it and/or modify | |||
| # it under the terms of the GNU General Public License as published by | |||
| # the Free Software Foundation; either version 3 of the License, or | |||
| # (at your option) any later version. | |||
| # | |||
| # This program is distributed in the hope that it will be useful, | |||
| # but WITHOUT ANY WARRANTY; without even the implied warranty of | |||
| # MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |||
| # GNU General Public License for more details. | |||
| # | |||
| from __future__ import division, print_function | |||
| import argparse | |||
| import binascii | |||
| import hashlib | |||
| import itertools | |||
| import shutil | |||
| import sys | |||
| from struct import pack, unpack | |||
| min_ftpr_offset = 0x400 | |||
| spared_blocks = 4 | |||
| unremovable_modules = ("ROMP", "BUP") | |||
| unremovable_modules_me11 = ("rbe", "kernel", "syslib", "bup") | |||
| unremovable_partitions = ("FTPR",) | |||
| pubkeys_md5 = { | |||
| "763e59ebe235e45a197a5b1a378dfa04": ("ME", ("6.x.x.x",)), | |||
| "3a98c847d609c253e145bd36512629cb": ("ME", ("6.0.50.x",)), | |||
| "0903fc25b0f6bed8c4ed724aca02124c": ("ME", ("7.x.x.x", "8.x.x.x")), | |||
| "2011ae6df87c40fba09e3f20459b1ce0": ("ME", ("9.0.x.x", "9.1.x.x")), | |||
| "e8427c5691cf8b56bc5cdd82746957ed": ("ME", ("9.5.x.x", "10.x.x.x")), | |||
| "986a78e481f185f7d54e4af06eb413f6": ("ME", ("11.x.x.x",)), | |||
| "bda0b6bb8ca0bf0cac55ac4c4d55e0f2": ("TXE", ("1.x.x.x",)), | |||
| "b726a2ab9cd59d4e62fe2bead7cf6997": ("TXE", ("1.x.x.x",)), | |||
| "0633d7f951a3e7968ae7460861be9cfb": ("TXE", ("2.x.x.x",)), | |||
| "1d0a36e9f5881540d8e4b382c6612ed8": ("TXE", ("3.x.x.x",)), | |||
| "be900fef868f770d266b1fc67e887e69": ("SPS", ("2.x.x.x",)), | |||
| "4622e3f2cb212a89c90a4de3336d88d2": ("SPS", ("3.x.x.x",)), | |||
| "31ef3d950eac99d18e187375c0764ca4": ("SPS", ("4.x.x.x",)) | |||
| } | |||
| class OutOfRegionException(Exception): | |||
| pass | |||
| class RegionFile: | |||
| def __init__(self, f, region_start, region_end): | |||
| self.f = f | |||
| self.region_start = region_start | |||
| self.region_end = region_end | |||
| def read(self, n): | |||
| if f.tell() + n <= self.region_end: | |||
| return self.f.read(n) | |||
| else: | |||
| raise OutOfRegionException() | |||
| def readinto(self, b): | |||
| if f.tell() + len(b) <= self.region_end: | |||
| return self.f.readinto(b) | |||
| else: | |||
| raise OutOfRegionException() | |||
| def seek(self, offset): | |||
| if self.region_start + offset <= self.region_end: | |||
| return self.f.seek(self.region_start + offset) | |||
| else: | |||
| raise OutOfRegionException() | |||
| def write_to(self, offset, data): | |||
| if self.region_start + offset + len(data) <= self.region_end: | |||
| self.f.seek(self.region_start + offset) | |||
| return self.f.write(data) | |||
| else: | |||
| raise OutOfRegionException() | |||
| def fill_range(self, start, end, fill): | |||
| if self.region_start + end <= self.region_end: | |||
| if start < end: | |||
| block = fill * 4096 | |||
| self.f.seek(self.region_start + start) | |||
| self.f.writelines(itertools.repeat(block, | |||
| (end - start) // 4096)) | |||
| self.f.write(block[:(end - start) % 4096]) | |||
| else: | |||
| raise OutOfRegionException() | |||
| def fill_all(self, fill): | |||
| self.fill_range(0, self.region_end - self.region_start, fill) | |||
| def move_range(self, offset_from, size, offset_to, fill): | |||
| if self.region_start + offset_from + size <= self.region_end and \ | |||
| self.region_start + offset_to + size <= self.region_end: | |||
| for i in range(0, size, 4096): | |||
| self.f.seek(self.region_start + offset_from + i, 0) | |||
| block = self.f.read(min(size - i, 4096)) | |||
| self.f.seek(self.region_start + offset_from + i, 0) | |||
| self.f.write(fill * len(block)) | |||
| self.f.seek(self.region_start + offset_to + i, 0) | |||
| self.f.write(block) | |||
| else: | |||
| raise OutOfRegionException() | |||
| def save(self, filename, size): | |||
| if self.region_start + size <= self.region_end: | |||
| self.f.seek(self.region_start) | |||
| copyf = open(filename, "w+b") | |||
| for i in range(0, size, 4096): | |||
| copyf.write(self.f.read(min(size - i, 4096))) | |||
| return copyf | |||
| else: | |||
| raise OutOfRegionException() | |||
| def get_chunks_offsets(llut): | |||
| chunk_count = unpack("<I", llut[0x04:0x08])[0] | |||
| huffman_stream_end = sum(unpack("<II", llut[0x10:0x18])) | |||
| nonzero_offsets = [huffman_stream_end] | |||
| offsets = [] | |||
| for i in range(0, chunk_count): | |||
| chunk = llut[0x40 + i * 4:0x44 + i * 4] | |||
| offset = 0 | |||
| if chunk[3] != 0x80: | |||
| offset = unpack("<I", chunk[0:3] + b"\x00")[0] | |||
| offsets.append([offset, 0]) | |||
| if offset != 0: | |||
| nonzero_offsets.append(offset) | |||
| nonzero_offsets.sort() | |||
| for i in offsets: | |||
| if i[0] != 0: | |||
| i[1] = nonzero_offsets[nonzero_offsets.index(i[0]) + 1] | |||
| return offsets | |||
| def remove_modules(f, mod_headers, ftpr_offset, me_end): | |||
| comp_str = ("uncomp.", "Huffman", "LZMA") | |||
| unremovable_huff_chunks = [] | |||
| chunks_offsets = [] | |||
| base = 0 | |||
| chunk_size = 0 | |||
| end_addr = 0 | |||
| for mod_header in mod_headers: | |||
| name = mod_header[0x04:0x14].rstrip(b"\x00").decode("ascii") | |||
| offset = unpack("<I", mod_header[0x38:0x3C])[0] + ftpr_offset | |||
| size = unpack("<I", mod_header[0x40:0x44])[0] | |||
| flags = unpack("<I", mod_header[0x50:0x54])[0] | |||
| comp_type = (flags >> 4) & 7 | |||
| print(" {:<16} ({:<7}, ".format(name, comp_str[comp_type]), end="") | |||
| if comp_type == 0x00 or comp_type == 0x02: | |||
| print("0x{:06x} - 0x{:06x} ): " | |||
| .format(offset, offset + size), end="") | |||
| if name in unremovable_modules: | |||
| end_addr = max(end_addr, offset + size) | |||
| print("NOT removed, essential") | |||
| else: | |||
| end = min(offset + size, me_end) | |||
| f.fill_range(offset, end, b"\xff") | |||
| print("removed") | |||
| elif comp_type == 0x01: | |||
| if not chunks_offsets: | |||
| f.seek(offset) | |||
| llut = f.read(4) | |||
| if llut == b"LLUT": | |||
| llut += f.read(0x3c) | |||
| chunk_count = unpack("<I", llut[0x4:0x8])[0] | |||
| base = unpack("<I", llut[0x8:0xc])[0] + 0x10000000 | |||
| chunk_size = unpack("<I", llut[0x30:0x34])[0] | |||
| llut += f.read(chunk_count * 4) | |||
| chunks_offsets = get_chunks_offsets(llut) | |||
| else: | |||
| sys.exit("Huffman modules found, but LLUT is not present") | |||
| module_base = unpack("<I", mod_header[0x34:0x38])[0] | |||
| module_size = unpack("<I", mod_header[0x3c:0x40])[0] | |||
| first_chunk_num = (module_base - base) // chunk_size | |||
| last_chunk_num = first_chunk_num + module_size // chunk_size | |||
| huff_size = 0 | |||
| for chunk in chunks_offsets[first_chunk_num:last_chunk_num + 1]: | |||
| huff_size += chunk[1] - chunk[0] | |||
| print("fragmented data, {:<9}): " | |||
| .format("~" + str(int(round(huff_size / 1024))) + " KiB"), | |||
| end="") | |||
| if name in unremovable_modules: | |||
| print("NOT removed, essential") | |||
| unremovable_huff_chunks += \ | |||
| [x for x in chunks_offsets[first_chunk_num: | |||
| last_chunk_num + 1] if x[0] != 0] | |||
| else: | |||
| print("removed") | |||
| else: | |||
| print("0x{:06x} - 0x{:06x}): unknown compression, skipping" | |||
| .format(offset, offset + size), end="") | |||
| if chunks_offsets: | |||
| removable_huff_chunks = [] | |||
| for chunk in chunks_offsets: | |||
| if all(not(unremovable_chk[0] <= chunk[0] < unremovable_chk[1] or | |||
| unremovable_chk[0] < chunk[1] <= unremovable_chk[1]) | |||
| for unremovable_chk in unremovable_huff_chunks): | |||
| removable_huff_chunks.append(chunk) | |||
| for removable_chunk in removable_huff_chunks: | |||
| if removable_chunk[1] > removable_chunk[0]: | |||
| end = min(removable_chunk[1], me_end) | |||
| f.fill_range(removable_chunk[0], end, b"\xff") | |||
| end_addr = max(end_addr, | |||
| max(unremovable_huff_chunks, key=lambda x: x[1])[1]) | |||
| return end_addr | |||
| def check_partition_signature(f, offset): | |||
| f.seek(offset) | |||
| header = f.read(0x80) | |||
| modulus = int(binascii.hexlify(f.read(0x100)[::-1]), 16) | |||
| public_exponent = unpack("<I", f.read(4))[0] | |||
| signature = int(binascii.hexlify(f.read(0x100)[::-1]), 16) | |||
| header_len = unpack("<I", header[0x4:0x8])[0] * 4 | |||
| manifest_len = unpack("<I", header[0x18:0x1c])[0] * 4 | |||
| f.seek(offset + header_len) | |||
| sha256 = hashlib.sha256() | |||
| sha256.update(header) | |||
| sha256.update(f.read(manifest_len - header_len)) | |||
| decrypted_sig = pow(signature, public_exponent, modulus) | |||
| return "{:#x}".format(decrypted_sig).endswith(sha256.hexdigest()) # FIXME | |||
| def print_check_partition_signature(f, offset): | |||
| if check_partition_signature(f, offset): | |||
| print("VALID") | |||
| else: | |||
| print("INVALID!!") | |||
| sys.exit("The FTPR partition signature is not valid. Is the input " | |||
| "ME/TXE image valid?") | |||
| def relocate_partition(f, me_end, partition_header_offset, | |||
| new_offset, mod_headers): | |||
| f.seek(partition_header_offset) | |||
| name = f.read(4).rstrip(b"\x00").decode("ascii") | |||
| f.seek(partition_header_offset + 0x8) | |||
| old_offset, partition_size = unpack("<II", f.read(0x8)) | |||
| llut_start = 0 | |||
| for mod_header in mod_headers: | |||
| if (unpack("<I", mod_header[0x50:0x54])[0] >> 4) & 7 == 0x01: | |||
| llut_start = unpack("<I", mod_header[0x38:0x3C])[0] + old_offset | |||
| break | |||
| if mod_headers and llut_start != 0: | |||
| # Bytes 0x9:0xb of the LLUT (bytes 0x1:0x3 of the AddrBase) are added | |||
| # to the SpiBase (bytes 0xc:0x10 of the LLUT) to compute the final | |||
| # start of the LLUT. Since AddrBase is not modifiable, we can act only | |||
| # on SpiBase and here we compute the minimum allowed new_offset. | |||
| f.seek(llut_start + 0x9) | |||
| lut_start_corr = unpack("<H", f.read(2))[0] | |||
| new_offset = max(new_offset, | |||
| lut_start_corr - llut_start - 0x40 + old_offset) | |||
| new_offset = ((new_offset + 0x1f) // 0x20) * 0x20 | |||
| offset_diff = new_offset - old_offset | |||
| print("Relocating {} from {:#x} - {:#x} to {:#x} - {:#x}..." | |||
| .format(name, old_offset, old_offset + partition_size, | |||
| new_offset, new_offset + partition_size)) | |||
| print(" Adjusting FPT entry...") | |||
| f.write_to(partition_header_offset + 0x8, | |||
| pack("<I", new_offset)) | |||
| if mod_headers: | |||
| if llut_start != 0: | |||
| f.seek(llut_start) | |||
| if f.read(4) == b"LLUT": | |||
| print(" Adjusting LUT start offset...") | |||
| lut_offset = llut_start + offset_diff + 0x40 - lut_start_corr | |||
| f.write_to(llut_start + 0x0c, pack("<I", lut_offset)) | |||
| print(" Adjusting Huffman start offset...") | |||
| f.seek(llut_start + 0x14) | |||
| old_huff_offset = unpack("<I", f.read(4))[0] | |||
| f.write_to(llut_start + 0x14, | |||
| pack("<I", old_huff_offset + offset_diff)) | |||
| print(" Adjusting chunks offsets...") | |||
| f.seek(llut_start + 0x4) | |||
| chunk_count = unpack("<I", f.read(4))[0] | |||
| f.seek(llut_start + 0x40) | |||
| chunks = bytearray(chunk_count * 4) | |||
| f.readinto(chunks) | |||
| for i in range(0, chunk_count * 4, 4): | |||
| if chunks[i + 3] != 0x80: | |||
| chunks[i:i + 3] = \ | |||
| pack("<I", unpack("<I", chunks[i:i + 3] + | |||
| b"\x00")[0] + offset_diff)[0:3] | |||
| f.write_to(llut_start + 0x40, chunks) | |||
| else: | |||
| sys.exit("Huffman modules present but no LLUT found!") | |||
| else: | |||
| print(" No Huffman modules found") | |||
| print(" Moving data...") | |||
| partition_size = min(partition_size, me_end - old_offset) | |||
| f.move_range(old_offset, partition_size, new_offset, b"\xff") | |||
| return new_offset | |||
| def check_and_remove_modules(f, me_end, offset, min_offset, | |||
| relocate, keep_modules): | |||
| f.seek(offset + 0x20) | |||
| num_modules = unpack("<I", f.read(4))[0] | |||
| f.seek(offset + 0x290) | |||
| data = f.read(0x84) | |||
| mod_header_size = 0 | |||
| if data[0x0:0x4] == b"$MME": | |||
| if data[0x60:0x64] == b"$MME" or num_modules == 1: | |||
| mod_header_size = 0x60 | |||
| elif data[0x80:0x84] == b"$MME": | |||
| mod_header_size = 0x80 | |||
| if mod_header_size != 0: | |||
| f.seek(offset + 0x290) | |||
| data = f.read(mod_header_size * num_modules) | |||
| mod_headers = [data[i * mod_header_size:(i + 1) * mod_header_size] | |||
| for i in range(0, num_modules)] | |||
| if all(hdr.startswith(b"$MME") for hdr in mod_headers): | |||
| if args.keep_modules: | |||
| end_addr = offset + ftpr_length | |||
| else: | |||
| end_addr = remove_modules(f, mod_headers, offset, me_end) | |||
| if args.relocate: | |||
| new_offset = relocate_partition(f, me_end, 0x30, min_offset, | |||
| mod_headers) | |||
| end_addr += new_offset - offset | |||
| offset = new_offset | |||
| return end_addr, offset | |||
| else: | |||
| print("Found less modules than expected in the FTPR " | |||
| "partition; skipping modules removal") | |||
| else: | |||
| print("Can't find the module header size; skipping " | |||
| "modules removal") | |||
| return -1, offset | |||
| def check_and_remove_modules_me11(f, me_end, partition_offset, | |||
| partition_length, min_offset, relocate, | |||
| keep_modules): | |||
| comp_str = ("LZMA/uncomp.", "Huffman") | |||
| if keep_modules: | |||
| end_data = partition_offset + partition_length | |||
| else: | |||
| end_data = 0 | |||
| f.seek(partition_offset + 0x4) | |||
| module_count = unpack("<I", f.read(4))[0] | |||
| modules = [] | |||
| modules.append(("end", partition_length, 0)) | |||
| f.seek(partition_offset + 0x10) | |||
| for i in range(0, module_count): | |||
| data = f.read(0x18) | |||
| name = data[0x0:0xc].rstrip(b"\x00").decode("ascii") | |||
| offset_block = unpack("<I", data[0xc:0x10])[0] | |||
| offset = offset_block & 0x01ffffff | |||
| comp_type = (offset_block & 0x02000000) >> 25 | |||
| modules.append((name, offset, comp_type)) | |||
| modules.sort(key=lambda x: x[1]) | |||
| for i in range(0, module_count): | |||
| name = modules[i][0] | |||
| offset = partition_offset + modules[i][1] | |||
| end = partition_offset + modules[i + 1][1] | |||
| removed = False | |||
| if name.endswith(".man") or name.endswith(".met"): | |||
| compression = "uncompressed" | |||
| else: | |||
| compression = comp_str[modules[i][2]] | |||
| print(" {:<12} ({:<12}, 0x{:06x} - 0x{:06x}): " | |||
| .format(name, compression, offset, end), end="") | |||
| if name.endswith(".man"): | |||
| print("NOT removed, partition manif.") | |||
| elif name.endswith(".met"): | |||
| print("NOT removed, module metadata") | |||
| elif any(name.startswith(m) for m in unremovable_modules_me11): | |||
| print("NOT removed, essential") | |||
| else: | |||
| removed = True | |||
| f.fill_range(offset, min(end, me_end), b"\xff") | |||
| print("removed") | |||
| if not removed: | |||
| end_data = max(end_data, end) | |||
| if relocate: | |||
| new_offset = relocate_partition(f, me_end, 0x30, min_offset, []) | |||
| end_data += new_offset - partition_offset | |||
| partition_offset = new_offset | |||
| return end_data, partition_offset | |||
| def check_mn2_tag(f, offset): | |||
| f.seek(offset + 0x1c) | |||
| tag = f.read(4) | |||
| if tag != b"$MN2": | |||
| sys.exit("Wrong FTPR manifest tag ({}), this image may be corrupted" | |||
| .format(tag)) | |||
| def flreg_to_start_end(flreg): | |||
| return (flreg & 0x7fff) << 12, (flreg >> 4 & 0x7fff000 | 0xfff) + 1 | |||
| def start_end_to_flreg(start, end): | |||
| return (start & 0x7fff000) >> 12 | ((end - 1) & 0x7fff000) << 4 | |||
| if __name__ == "__main__": | |||
| parser = argparse.ArgumentParser(description="Tool to remove as much code " | |||
| "as possible from Intel ME/TXE firmware " | |||
| "images") | |||
| softdis = parser.add_mutually_exclusive_group() | |||
| bw_list = parser.add_mutually_exclusive_group() | |||
| parser.add_argument("-v", "--version", action="version", | |||
| version="%(prog)s 1.2") | |||
| parser.add_argument("file", help="ME/TXE image or full dump") | |||
| parser.add_argument("-O", "--output", metavar='output_file', help="save " | |||
| "the modified image in a separate file, instead of " | |||
| "modifying the original file") | |||
| softdis.add_argument("-S", "--soft-disable", help="in addition to the " | |||
| "usual operations on the ME/TXE firmware, set the " | |||
| "MeAltDisable bit or the HAP bit to ask Intel ME/TXE " | |||
| "to disable itself after the hardware initialization " | |||
| "(requires a full dump)", action="store_true") | |||
| softdis.add_argument("-s", "--soft-disable-only", help="instead of the " | |||
| "usual operations on the ME/TXE firmware, just set " | |||
| "the MeAltDisable bit or the HAP bit to ask Intel " | |||
| "ME/TXE to disable itself after the hardware " | |||
| "initialization (requires a full dump)", | |||
| action="store_true") | |||
| parser.add_argument("-r", "--relocate", help="relocate the FTPR partition " | |||
| "to the top of the ME region to save even more space", | |||
| action="store_true") | |||
| parser.add_argument("-t", "--truncate", help="truncate the empty part of " | |||
| "the firmware (requires a separated ME/TXE image or " | |||
| "--extract-me)", action="store_true") | |||
| parser.add_argument("-k", "--keep-modules", help="don't remove the FTPR " | |||
| "modules, even when possible", action="store_true") | |||
| bw_list.add_argument("-w", "--whitelist", metavar="whitelist", | |||
| help="Comma separated list of additional partitions " | |||
| "to keep in the final image. This can be used to " | |||
| "specify the MFS partition for example, which stores " | |||
| "PCIe and clock settings.") | |||
| bw_list.add_argument("-b", "--blacklist", metavar="blacklist", | |||
| help="Comma separated list of partitions to remove " | |||
| "from the image. This option overrides the default " | |||
| "removal list.") | |||
| parser.add_argument("-d", "--descriptor", help="remove the ME/TXE " | |||
| "Read/Write permissions to the other regions on the " | |||
| "flash from the Intel Flash Descriptor (requires a " | |||
| "full dump)", action="store_true") | |||
| parser.add_argument("-D", "--extract-descriptor", | |||
| metavar='output_descriptor', help="extract the flash " | |||
| "descriptor from a full dump; when used with " | |||
| "--truncate save a descriptor with adjusted regions " | |||
| "start and end") | |||
| parser.add_argument("-M", "--extract-me", metavar='output_me_image', | |||
| help="extract the ME firmware from a full dump; when " | |||
| "used with --truncate save a truncated ME/TXE image") | |||
| parser.add_argument("-c", "--check", help="verify the integrity of the " | |||
| "fundamental parts of the firmware and exit", | |||
| action="store_true") | |||
| args = parser.parse_args() | |||
| if args.check and (args.soft_disable_only or args.soft_disable or | |||
| args.relocate or args.descriptor or args.truncate or args.output): | |||
| sys.exit("-c can't be used with -S, -s, -r, -d, -t or -O") | |||
| if args.soft_disable_only and (args.relocate or args.truncate): | |||
| sys.exit("-s can't be used with -r or -t") | |||
| if (args.whitelist or args.blacklist) and args.relocate: | |||
| sys.exit("Relocation is not yet supported with custom whitelist or " | |||
| "blacklist") | |||
| f = open(args.file, "rb" if args.check or args.output else "r+b") | |||
| f.seek(0x10) | |||
| magic = f.read(4) | |||
| if magic == b"$FPT": | |||
| print("ME/TXE image detected") | |||
| if args.descriptor or args.extract_descriptor or args.extract_me or \ | |||
| args.soft_disable or args.soft_disable_only: | |||
| sys.exit("-d, -D, -M, -S and -s require a full dump") | |||
| f.seek(0, 2) | |||
| me_start = 0 | |||
| me_end = f.tell() | |||
| mef = RegionFile(f, me_start, me_end) | |||
| elif magic == b"\x5a\xa5\xf0\x0f": | |||
| print("Full image detected") | |||
| if args.truncate and not args.extract_me: | |||
| sys.exit("-t requires a separated ME/TXE image (or --extract-me)") | |||
| f.seek(0x14) | |||
| flmap0, flmap1 = unpack("<II", f.read(8)) | |||
| frba = flmap0 >> 12 & 0xff0 | |||
| fmba = (flmap1 & 0xff) << 4 | |||
| fpsba = flmap1 >> 12 & 0xff0 | |||
| f.seek(frba) | |||
| flreg = unpack("<III", f.read(12)) | |||
| fd_start, fd_end = flreg_to_start_end(flreg[0]) | |||
| bios_start, bios_end = flreg_to_start_end(flreg[1]) | |||
| me_start, me_end = flreg_to_start_end(flreg[2]) | |||
| if me_start >= me_end: | |||
| sys.exit("The ME/TXE region in this image has been disabled") | |||
| mef = RegionFile(f, me_start, me_end) | |||
| mef.seek(0x10) | |||
| if mef.read(4) != b"$FPT": | |||
| sys.exit("The ME/TXE region is corrupted or missing") | |||
| print("The ME/TXE region goes from {:#x} to {:#x}" | |||
| .format(me_start, me_end)) | |||
| else: | |||
| sys.exit("Unknown image") | |||
| end_addr = me_end | |||
| print("Found FPT header at {:#x}".format(mef.region_start + 0x10)) | |||
| mef.seek(0x14) | |||
| entries = unpack("<I", mef.read(4))[0] | |||
| print("Found {} partition(s)".format(entries)) | |||
| mef.seek(0x30) | |||
| partitions = mef.read(entries * 0x20) | |||
| ftpr_header = b"" | |||
| for i in range(entries): | |||
| if partitions[i * 0x20:(i * 0x20) + 4] == b"FTPR": | |||
| ftpr_header = partitions[i * 0x20:(i + 1) * 0x20] | |||
| break | |||
| if ftpr_header == b"": | |||
| sys.exit("FTPR header not found, this image doesn't seem to be valid") | |||
| ftpr_offset, ftpr_length = unpack("<II", ftpr_header[0x08:0x10]) | |||
| print("Found FTPR header: FTPR partition spans from {:#x} to {:#x}" | |||
| .format(ftpr_offset, ftpr_offset + ftpr_length)) | |||
| mef.seek(ftpr_offset) | |||
| if mef.read(4) == b"$CPD": | |||
| me11 = True | |||
| num_entries = unpack("<I", mef.read(4))[0] | |||
| mef.seek(ftpr_offset + 0x10) | |||
| ftpr_mn2_offset = -1 | |||
| for i in range(0, num_entries): | |||
| data = mef.read(0x18) | |||
| name = data[0x0:0xc].rstrip(b"\x00").decode("ascii") | |||
| offset = unpack("<I", data[0xc:0xf] + b"\x00")[0] | |||
| if name == "FTPR.man": | |||
| ftpr_mn2_offset = offset | |||
| break | |||
| if ftpr_mn2_offset >= 0: | |||
| check_mn2_tag(mef, ftpr_offset + ftpr_mn2_offset) | |||
| print("Found FTPR manifest at {:#x}" | |||
| .format(ftpr_offset + ftpr_mn2_offset)) | |||
| else: | |||
| sys.exit("Can't find the manifest of the FTPR partition") | |||
| else: | |||
| check_mn2_tag(mef, ftpr_offset) | |||
| me11 = False | |||
| ftpr_mn2_offset = 0 | |||
| mef.seek(ftpr_offset + ftpr_mn2_offset + 0x24) | |||
| version = unpack("<HHHH", mef.read(0x08)) | |||
| print("ME/TXE firmware version {}" | |||
| .format('.'.join(str(i) for i in version))) | |||
| mef.seek(ftpr_offset + ftpr_mn2_offset + 0x80) | |||
| pubkey_md5 = hashlib.md5(mef.read(0x104)).hexdigest() | |||
| if pubkey_md5 in pubkeys_md5: | |||
| variant, pubkey_versions = pubkeys_md5[pubkey_md5] | |||
| print("Public key match: Intel {}, firmware versions {}" | |||
| .format(variant, ", ".join(pubkey_versions))) | |||
| else: | |||
| if version[0] >= 6: | |||
| variant = "ME" | |||
| else: | |||
| variant = "TXE" | |||
| print("WARNING Unknown public key {}\n" | |||
| " Assuming Intel {}\n" | |||
| " Please report this warning to the project's maintainer!" | |||
| .format(pubkey_md5, variant)) | |||
| if not args.check and args.output: | |||
| f.close() | |||
| shutil.copy(args.file, args.output) | |||
| f = open(args.output, "r+b") | |||
| mef = RegionFile(f, me_start, me_end) | |||
| if me_start > 0: | |||
| fdf = RegionFile(f, fd_start, fd_end) | |||
| if me11: | |||
| fdf.seek(fpsba) | |||
| pchstrp0 = unpack("<I", fdf.read(4))[0] | |||
| print("The HAP bit is " + | |||
| ("SET" if pchstrp0 & 1 << 16 else "NOT SET")) | |||
| else: | |||
| fdf.seek(fpsba + 0x28) | |||
| pchstrp10 = unpack("<I", fdf.read(4))[0] | |||
| print("The AltMeDisable bit is " + | |||
| ("SET" if pchstrp10 & 1 << 7 else "NOT SET")) | |||
| # ME 6 Ignition: wipe everything | |||
| me6_ignition = False | |||
| if not args.check and not args.soft_disable_only and \ | |||
| variant == "ME" and version[0] == 6: | |||
| mef.seek(ftpr_offset + 0x20) | |||
| num_modules = unpack("<I", mef.read(4))[0] | |||
| mef.seek(ftpr_offset + 0x290 + (num_modules + 1) * 0x60) | |||
| data = mef.read(0xc) | |||
| if data[0x0:0x4] == b"$SKU" and data[0x8:0xc] == b"\x00\x00\x00\x00": | |||
| print("ME 6 Ignition firmware detected, removing everything...") | |||
| mef.fill_all(b"\xff") | |||
| me6_ignition = True | |||
| if not args.check: | |||
| if not args.soft_disable_only and not me6_ignition: | |||
| print("Reading partitions list...") | |||
| unremovable_part_fpt = b"" | |||
| extra_part_end = 0 | |||
| whitelist = [] | |||
| blacklist = [] | |||
| whitelist += unremovable_partitions | |||
| if args.blacklist: | |||
| blacklist = args.blacklist.split(",") | |||
| elif args.whitelist: | |||
| whitelist += args.whitelist.split(",") | |||
| for i in range(entries): | |||
| partition = partitions[i * 0x20:(i + 1) * 0x20] | |||
| flags = unpack("<I", partition[0x1c:0x20])[0] | |||
| try: | |||
| part_name = \ | |||
| partition[0x0:0x4].rstrip(b"\x00").decode("ascii") | |||
| except UnicodeDecodeError: | |||
| part_name = "????" | |||
| part_start, part_length = unpack("<II", partition[0x08:0x10]) | |||
| # ME 6: the last partition has 0xffffffff as size | |||
| if variant == "ME" and version[0] == 6 and \ | |||
| i == entries - 1 and part_length == 0xffffffff: | |||
| part_length = me_end - me_start - part_start | |||
| part_end = part_start + part_length | |||
| if flags & 0x7f == 2: | |||
| print(" {:<4} ({:^24}, 0x{:08x} total bytes): nothing to " | |||
| "remove" | |||
| .format(part_name, "NVRAM partition, no data", | |||
| part_length)) | |||
| elif part_start == 0 or part_length == 0 or part_end > me_end: | |||
| print(" {:<4} ({:^24}, 0x{:08x} total bytes): nothing to " | |||
| "remove" | |||
| .format(part_name, "no data here", part_length)) | |||
| else: | |||
| print(" {:<4} (0x{:08x} - 0x{:09x}, 0x{:08x} total bytes): " | |||
| .format(part_name, part_start, part_end, part_length), | |||
| end="") | |||
| if part_name in whitelist or (blacklist and | |||
| part_name not in blacklist): | |||
| unremovable_part_fpt += partition | |||
| if part_name != "FTPR": | |||
| extra_part_end = max(extra_part_end, part_end) | |||
| print("NOT removed") | |||
| else: | |||
| mef.fill_range(part_start, part_end, b"\xff") | |||
| print("removed") | |||
| print("Removing partition entries in FPT...") | |||
| mef.write_to(0x30, unremovable_part_fpt) | |||
| mef.write_to(0x14, | |||
| pack("<I", len(unremovable_part_fpt) // 0x20)) | |||
| mef.fill_range(0x30 + len(unremovable_part_fpt), | |||
| 0x30 + len(partitions), b"\xff") | |||
| if (not blacklist and "EFFS" not in whitelist) or \ | |||
| "EFFS" in blacklist: | |||
| print("Removing EFFS presence flag...") | |||
| mef.seek(0x24) | |||
| flags = unpack("<I", mef.read(4))[0] | |||
| flags &= ~(0x00000001) | |||
| mef.write_to(0x24, pack("<I", flags)) | |||
| if me11: | |||
| mef.seek(0x10) | |||
| header = bytearray(mef.read(0x20)) | |||
| header[0x0b] = 0x00 | |||
| else: | |||
| mef.seek(0) | |||
| header = bytearray(mef.read(0x30)) | |||
| header[0x1b] = 0x00 | |||
| checksum = (0x100 - sum(header) & 0xff) & 0xff | |||
| print("Correcting checksum (0x{:02x})...".format(checksum)) | |||
| # The checksum is just the two's complement of the sum of the first | |||
| # 0x30 bytes in ME < 11 or bytes 0x10:0x30 in ME >= 11 (except for | |||
| # 0x1b, the checksum itself). In other words, the sum of those | |||
| # bytes must be always 0x00. | |||
| mef.write_to(0x1b, pack("B", checksum)) | |||
| print("Reading FTPR modules list...") | |||
| if me11: | |||
| end_addr, ftpr_offset = \ | |||
| check_and_remove_modules_me11(mef, me_end, | |||
| ftpr_offset, ftpr_length, | |||
| min_ftpr_offset, | |||
| args.relocate, | |||
| args.keep_modules) | |||
| else: | |||
| end_addr, ftpr_offset = \ | |||
| check_and_remove_modules(mef, me_end, ftpr_offset, | |||
| min_ftpr_offset, args.relocate, | |||
| args.keep_modules) | |||
| if end_addr > 0: | |||
| end_addr = max(end_addr, extra_part_end) | |||
| end_addr = (end_addr // 0x1000 + 1) * 0x1000 | |||
| end_addr += spared_blocks * 0x1000 | |||
| print("The ME minimum size should be {0} bytes " | |||
| "({0:#x} bytes)".format(end_addr)) | |||
| if me_start > 0: | |||
| print("The ME region can be reduced up to:\n" | |||
| " {:08x}:{:08x} me" | |||
| .format(me_start, me_start + end_addr - 1)) | |||
| elif args.truncate: | |||
| print("Truncating file at {:#x}...".format(end_addr)) | |||
| f.truncate(end_addr) | |||
| if args.soft_disable or args.soft_disable_only: | |||
| if me11: | |||
| print("Setting the HAP bit in PCHSTRP0 to disable Intel ME...") | |||
| pchstrp0 |= (1 << 16) | |||
| fdf.write_to(fpsba, pack("<I", pchstrp0)) | |||
| else: | |||
| print("Setting the AltMeDisable bit in PCHSTRP10 to disable " | |||
| "Intel ME...") | |||
| pchstrp10 |= (1 << 7) | |||
| fdf.write_to(fpsba + 0x28, pack("<I", pchstrp10)) | |||
| if args.descriptor: | |||
| print("Removing ME/TXE R/W access to the other flash regions...") | |||
| if me11: | |||
| flmstr2 = 0x00400500 | |||
| else: | |||
| fdf.seek(fmba + 0x4) | |||
| flmstr2 = (unpack("<I", fdf.read(4))[0] | 0x04040000) & 0x0404ffff | |||
| fdf.write_to(fmba + 0x4, pack("<I", flmstr2)) | |||
| if args.extract_descriptor: | |||
| if args.truncate: | |||
| print("Extracting the descriptor to \"{}\"..." | |||
| .format(args.extract_descriptor)) | |||
| fdf_copy = fdf.save(args.extract_descriptor, fd_end - fd_start) | |||
| if bios_start == me_end: | |||
| print("Modifying the regions of the extracted descriptor...") | |||
| print(" {:08x}:{:08x} me --> {:08x}:{:08x} me" | |||
| .format(me_start, me_end - 1, | |||
| me_start, me_start + end_addr - 1)) | |||
| print(" {:08x}:{:08x} bios --> {:08x}:{:08x} bios" | |||
| .format(bios_start, bios_end - 1, | |||
| me_start + end_addr, bios_end - 1)) | |||
| flreg1 = start_end_to_flreg(me_start + end_addr, bios_end) | |||
| flreg2 = start_end_to_flreg(me_start, me_start + end_addr) | |||
| fdf_copy.seek(frba + 0x4) | |||
| fdf_copy.write(pack("<II", flreg1, flreg2)) | |||
| else: | |||
| print("\nWARNING:\n The start address of the BIOS region " | |||
| "isn't equal to the end address of the ME\n region: if " | |||
| "you want to recover the space from the ME region you " | |||
| "have to\n manually modify the descriptor.\n") | |||
| else: | |||
| print("Extracting the descriptor to \"{}\"..." | |||
| .format(args.extract_descriptor)) | |||
| fdf_copy = fdf.save(args.extract_descriptor, fd_end - fd_start) | |||
| fdf_copy.close() | |||
| if args.extract_me: | |||
| if args.truncate: | |||
| print("Extracting and truncating the ME image to \"{}\"..." | |||
| .format(args.extract_me)) | |||
| mef_copy = mef.save(args.extract_me, end_addr) | |||
| else: | |||
| print("Extracting the ME image to \"{}\"..." | |||
| .format(args.extract_me)) | |||
| mef_copy = mef.save(args.extract_me, me_end - me_start) | |||
| if not me6_ignition: | |||
| print("Checking the FTPR RSA signature of the extracted ME " | |||
| "image... ", end="") | |||
| print_check_partition_signature(mef_copy, | |||
| ftpr_offset + ftpr_mn2_offset) | |||
| mef_copy.close() | |||
| if not me6_ignition: | |||
| print("Checking the FTPR RSA signature... ", end="") | |||
| print_check_partition_signature(mef, ftpr_offset + ftpr_mn2_offset) | |||
| f.close() | |||
| if not args.check: | |||
| print("Done! Good luck!") | |||
+ 23
- 0
t430/util/me_cleaner/setup.py
View File
| @ -0,0 +1,23 @@ | |||
| #!/usr/bin/python | |||
| from setuptools import setup | |||
| setup( | |||
| name="me_cleaner", | |||
| version="1.2", | |||
| description="Tool for partial deblobbing of Intel ME/TXE firmware images", | |||
| url="https://github.com/corna/me_cleaner", | |||
| author="Nicola Corna", | |||
| author_email="nicola@corna.info", | |||
| license="GPLv3+", | |||
| scripts=['me_cleaner.py'], | |||
| classifiers=[ | |||
| 'Development Status :: 4 - Beta', | |||
| 'Intended Audience :: Developers', | |||
| 'License :: OSI Approved :: GNU General Public License v3 or later (GPLv3+)', | |||
| 'Operating System :: OS Independent', | |||
| 'Programming Language :: Python :: 2', | |||
| 'Programming Language :: Python :: 3', | |||
| ] | |||
| ) | |||